Internet Fundamentals/Collection
Internet Fundamentals
[edit | edit source]Learning Guide
[edit | edit source]This learning guide supports the Wikiversity course Internet Fundamentals, available at http://en.wikiversity.org/wiki/Internet_Fundamentals.
Overview
[edit | edit source]Internet Fundamentals/Collection/Sidebar
The Internet is the global system of interconnected computer networks that use the Internet protocol suite (TCP/IP) to link billions of devices worldwide.[1] Fundamental Internet concepts include web browsers, search engines, email, social media, communications, networking, security, HTML, CSS, graphics and multimedia, web accessibility, JavaScript, database concepts, project management concepts, and related career opportunities.[2][3]
This course comprises 15 lessons covering fundamental Internet concepts. The first half of the course approaches the Internet from a user perspective. The second half of the course provides an introduction to web development. Each lesson includes a combination of Wikipedia readings, YouTube videos, and hands-on learning activities. The course also assists learners in preparing for CIW Internet Business Associate certification.
Preparation of internet
[edit | edit source]This is an introductory college-level computer course. Learners should have basic computer skills, including typing, mouse, and web browser navigation.
Lessons
[edit | edit source]
- Introduction
- Web Browsers
- Search Engines
- Social Media
- Communications
- Networking
- Security
- HTML
- CSS
- Graphics and Multimedia
- Web Accessibility
- JavaScript
- Databases
- Project Management
- IT Careers
See Also
[edit | edit source]- Computer Skills
- Digital Literacy
- Internet
- Web Foundations
- IT Fundamentals
- HTML
- CSS
- JavaScript
- Microsoft: Web Development for Beginners
Assessments
[edit | edit source]- Flashcards: Quizlet: CIW
- Quiz: Quizlet: CIW
References
[edit | edit source]Lesson 1 - Introduction
[edit | edit source]
The Internet is the global system of interconnected computer networks that use the Internet protocol suite (TCP/IP) to link devices worldwide.[1] This lesson introduces fundamental Internet concepts and terms used throughout the course.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:
- Understand fundamental Internet concepts and vocabulary.
- Review basic computer skills including typing, computer navigation, file management, and Internet web browsing email. This also includes being familiar with online systems and text editors or word processing software.
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: What is the Internet?
- YouTube: The Internet: Wires, Cables, & Wifi
- YouTube: Andrew Blum: What is the Internet, really?
- YouTube: Learn Keyboard Typing
- YouTube: Basic Computer Skills
- YouTube: How to Save a Document
- YouTube: Saving Files and Creating File Folders
- YouTube: What is GIT?
Activities
[edit | edit source]- Complete the following tutorials:
- Complete the following GCFLearnFree tutorials:
- Complete the following WikiHow tutorials:
- Manage folders and files:
- Windows: Review GCF Global: Windows Basics - Working with Files. Review the existing structure and properties for the Documents folder. Improve file organization, if necessary.
- macOS: Review GCF Global: macOS Basics - Working with Files. Review the existing structure and information for the Documents folder. Improve file organization, if necessary.
- Linux: Review IBM: Learn Linux, 101: File and directory management. Review the existing structure and detailed information for the Documents folder. Improve file organization, if necessary.
- IP Addresses and Geolocation
- Review Livewire: Does IP Address Location (Geolocation) Really Work?
- Visit https://whatismyipaddress.com or https://www.whatismyip.com to identify your IPv4 and IPv6 addresses.
- Visit https://tools.keycdn.com/geo to look up your IP address geolocation. Look up your IPv4 address and your IPv6 address if you have both addresses.
- Tracing Internet Traffic
- Review HowToGeek: How to use traceroute to Identify Network Problems
- Use the
tracert(Windows) ortraceroute(macOS / Linux) command to trace the route from you to en.wikiversity.org or another host. - Use https://traceroute-online.com/ to visually trace the route to en.wikiversity.org or another host.
- Git
- Complete one or more of the following tutorials:
- Create a git repository and website to use for this course:
- Review Bitbucket/Get Started and Bitbucket/Website Hosting. Create a Bitbucket repository and website.
- Review GitHub/Get Started and GitHub/Website Hosting. Create a GitHub repository and website.
Lesson Summary
[edit | edit source]- The Internet is the global system of interconnected computer networks that use the Internet protocol suite (TCP/IP) to link devices worldwide.[2]
- The Internet carries an extensive range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing.[3]
- The origins of the Internet date back to research commissioned by the United States federal government in the 1960s to build robust, fault-tolerant communication via computer networks.[4]
- The primary precursor network, the ARPANET, initially served as a backbone for interconnection of regional academic and military networks in the 1980s.[5]
- Common file-management functions include opening, closing, saving, or using save-as, creating, printing, resizing, including minimizing and maximizing, searching for and viewing files. All of these functions can be performed via the Menu bar in most office applications.
- Most traditional communications media, including telephony, radio, television, paper mail and newspapers are being reshaped or redefined by the Internet, giving birth to new services such as email, Internet telephony, Internet television, online music, digital newspapers, and video streaming websites.[6]
- Newspaper, book, and other print publishing are adapting to website technology, or are reshaped into blogging, web feeds and online news aggregators.[7]
- The Internet has enabled and accelerated new forms of personal interactions through instant messaging, Internet forums, and social networking.[8]
- The Internet has no centralized governance in either technological implementation or policies for access and usage; each constituent network sets its own policies.[9]
- Only the overreaching definitions of the two principal name spaces in the Internet, the Internet Protocol address (IP address) space and the Domain Name System (DNS), are directed by a maintainer organization, the Internet Corporation for Assigned Names and Numbers (ICANN).[10]
- The technical underpinning and standardization of the core protocols is an activity of the Internet Engineering Task Force (IETF), a non-profit organization of loosely affiliated international participants that anyone may associate with by contributing technical expertise.[11]
- The World Wide Web or the Web is only one of a large number of Internet services.[12]
- The Internet carries many network services, most prominently mobile apps such as social media apps, the World Wide Web, electronic mail, multiplayer online games, Internet telephony, and file sharing services.[13]
- The Web is a collection of interconnected documents (web pages) and other web resources, linked by hyperlinks and URLs.[14]
- Hypertext Transfer Protocol, or HTTP, is the language used on the Web for information transfer, yet it is just one of many languages or protocols that can be used for communication on the Internet.[15]
- Common methods of Internet access by users include dial-up with a computer modem via telephone circuits, broadband over coaxial cable, fiber optics or copper wires, Wi-Fi, satellite and cellular telephone technology (3G, 4G).[16]
- Internet resources, hardware, and software components are the target of criminal or malicious attempts to gain unauthorized control to cause interruptions, commit fraud, engage in blackmail or access private information.[17]
- Git is a version control system for tracking changes in computer files and coordinating work on those files among multiple people.[18]
Key Terms
[edit | edit source]- cloud computing
- Internet-based computing that provides shared computer processing resources and data to computers and other devices on demand.[19]
- communication protocol
- A system of rules that allow two or more entities of a communications system to transmit information.[20]
- computer security
- The protection of computer systems from the theft or damage to their hardware, software or information, as well as from disruption or misdirection of the services they provide.[21]
- copyright
- A legal right created by the law of a country that grants the creator of an original work exclusive rights for its use and distribution.[22]
- CSS (Cascading Style Sheets)
- A style sheet language used for describing the presentation of a document written in a markup language.[23]
- database
- An organized collection of data, including schemas, tables, queries, reports, views and other objects.[24]
- email (electronic mail)
- A method of exchanging digital messages from an author to one or more recipients.[25]
- graphics
- Visual images or designs used to inform, illustrate, or entertain.[26]
- HTML (Hypertext Markup Language)
- The standard markup language for creating web pages and web applications.[27]
- HTTP (Hypertext Transfer Protocol)
- An application protocol for distributed, collaborative, and hypermedia information systems.[28]
- ICANN (Internet Corporation for Assigned Names and Numbers)
- A nonprofit organization responsible for coordinating the maintenance and procedures of several databases related to the namespaces of the Internet, ensuring the network's stable and secure operation.[29]
- IEEE (Institute of Electrical and Electronics Engineers)
- A professional organization with objectives for the educational and technical advancement of electrical and electronic engineering, telecommunications, computer engineering and allied disciplines.[30]
- information technology
- The application of computers to store, study, retrieve, transmit, and manipulate data, or information, often in the context of a business or other enterprise.[31]
- intellectual property
- Creations for which a monopoly is assigned to designated owners by law.[32]
- ISO (International Organization for Standardization)
- An international standard-setting body composed of representatives from various national standards organizations.[33]
- IETF (Internet Engineering Task Force)
- The organization that develops and promotes voluntary Internet standards, and in particular the standards that comprise the Internet protocol suite (TCP/IP).[34]
- Internet service provider (ISP)
- An organization that provides services accessing and using the Internet.[35]
- IPv4
- One of the core protocols of standards-based internetworking methods in the Internet, and was the first version deployed for production in the ARPANET in 1983.[36]
- IPv6
- The most recent version of the communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet.[37]
- Java
- A general-purpose computer programming language that is concurrent, class-based, object-oriented, and specifically designed to have as few implementation dependencies as possible.[38]
- JavaScript
- A high-level, dynamic, untyped, object-based, multi-paradigm, and interpreted programming language used alongside HTML and CSS to make webpages interactive and provide online programs.[39]
- multimedia
- Content that uses a combination of different forms such as text, audio, images, animations, video and interactive content.[40]
- network
- A telecommunications network which allows nodes to share resources.[41]
- open-source software
- Computer software with its source code made available with a license in which the copyright holder provides the rights to study, change, and distribute the software to anyone and for any purpose.[42]
- paradigm shift
- A fundamental change in the basic concepts and experimental practices of a scientific discipline.[43]
- project management
- The discipline of initiating, planning, executing, controlling, and closing the work of a team to achieve specific goals and meet specific success criteria.[44]
- proprietary software
- Computer software for which the software's publisher or another person retains intellectual property rights[45]
- RFC (Request for Comments)
- A type of publication from the Internet Engineering Task Force (IETF) and the Internet Society (ISOC) that describes methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems.[46]
- search engine
- A software system that is designed to locate information on the World Wide Web.[47]
- social media
- Computer-mediated technologies that facilitate the creation and sharing of information, ideas, career interests and other forms of expression via virtual communities and networks.[48]
- TIA (Telecommunications Industry Association)
- Accredited by the American National Standards Institute (ANSI) to develop voluntary, consensus-based industry standards for a wide variety of Information and Communication Technologies (ICT) products.[49]
- URL (Uniform Resource Locator)
- A reference to a web resource that specifies its location on a computer network and a mechanism for retrieving it.[50]
- W3C (World Wide Web Consortium)
- The main international standards organization for the World Wide Web.[51]
- web browser
- A software application used to present, access, and pass information resources on the world wide web [52]
Assessments
[edit | edit source]- Flashcards: Quizlet: Introduction to the Internet
- Quiz: Quizlet: Introduction to the Internet
See Also
[edit | edit source]References
[edit | edit source]- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Internet
- ↑ Wikipedia: Git
- ↑ Wikipedia: Cloud computing
- ↑ Wikipedia: Communications protocol
- ↑ Wikipedia: Computer security
- ↑ Wikipedia: Copyright
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Database
- ↑ Wikipedia: Email
- ↑ Wikipedia: Graphics
- ↑ Wikipedia: HTML
- ↑ Wikipedia: Hypertext Transfer Protocol
- ↑ Wikipedia: ICANN
- ↑ Wikipedia: Institute of Electrical and Electronics Engineers
- ↑ Wikipedia: Information technology
- ↑ Wikipedia: Intellectual property
- ↑ Wikipedia: International Organization for Standardization
- ↑ Wikipedia: Internet Engineering Task Force
- ↑ Wikipedia: Internet service provider
- ↑ Wikipedia: IPv4
- ↑ Wikipedia: IPv6
- ↑ Wikipedia: Java
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Open-source software
- ↑ Wikipedia: Paradigm shift
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Proprietary software
- ↑ Wikipedia: Request for Comments
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Telecommunications Industry Association
- ↑ Wikipedia: URL
- ↑ Wikipedia: World Wide Web Consortium
- ↑ Wikipedia: Web browser
Lesson 2 - Web Browsers
[edit | edit source]



A web browser (commonly referred to as a browser) is a software application for retrieving, presenting and traversing information resources on the World Wide Web.[1] This lesson introduces web browsers.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[2][3][4]
- Identify the functions of Web browsers, and use them to access the World Wide Web and other computer resources.
- Identify and configure user customization features in Web browsers, including preferences, caching, cookies.
- Connect to and access the Internet
- Connect to Internet via existing Internet connection and confirm functionality
- Open Internet browser and set home page of personal choice by setting Internet options
- Ensure Internet browser software security
- Adjust display of the Internet browser to suit personal requirements
- Modify toolbar to meet user and Internet browser needs
- Access a particular website, note privacy and other conditions of use, and retrieve data
- Use socially responsible behaviour when sharing information on the Internet
- Enter uniform resource locator (URL) in address line of Internet browser
- Access and use consumer specific sites on the Internet
- Identify, access and review information specific sites to gain consumer information
- Identify and use Internet application sites to lodge details and gain access and information
- Access and use online forms on the Internet
- Undertake online transactions
- Access online transaction site
- Ensure security of transaction site
- Enter required information into fields on merchant's website
- Ensure pop-up dialog boxes, prompts or feedback mechanisms are completed
- Enter, check and make changes to preferred transaction options
- Complete online transaction
- Record and archive receipts according to business processes
- Close down and leave transaction process
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: What is a browser?
- YouTube: Browser Basics
- YouTube: Browsing in Chrome
- YouTube: Getting Started with Firefox
- YouTube: Customizing Chrome
- YouTube: Customize Firefox controls, buttons and toolbars
Student Presentations
[edit | edit source]Activities
[edit | edit source]- Complete the following tutorials:
- Install multiple web browsers to compare the different programs:
- Brave
- Review Brave: Download and Install Brave
- Download and install Brave.
- Chrome
- Review Google: Download and Install Google Chrome.
- Download and install Chrome.
- Edge
- Review Microsoft: Download Microsoft Edge Web Browser
- Download and install Edge
- Firefox
- Review Mozilla: Firefox
- Download and install Firefox.
- Opera
- Review Opera: Browser
- Download and install Opera.
- Brave
- Practice using web browsers:
- All platforms:
- Complete the tutorial GCFLearnFree: Chrome
- Complete the tutorial GCFLearnFree: Edge
- Complete the tutorial GCFLearnFree: Firefox
- Complete the tutorial Opera: Getting started with Opera
- MacOS
- Complete the tutorial GCFLearnFree: Safari
- All
- After completing the tutorials, search the Internet for tips on using your preferred web browser(s).
- All platforms:
- Configure browser settings.
- Brave
- Review available resources in the Brave: Brave Help Center.
- Check Brave settings and advanced settings and modify any settings that would improve your Internet experience.
- Chrome
- Review available resources in the Google: Chrome Help Center.
- Check Chrome settings and advanced settings and modify any settings that would improve your Internet experience.
- Edge
- Review available resources under Edge: Settings and Tools.
- Check Edge settings and modify any settings that would improve your Internet experience.
- Firefox
- Review available resources under Mozilla: Firefox Help Topics.
- Check Firefox preferences and modify any settings that would improve your Internet experience.
- Opera
- Review available resources under Opera: Personalize Opera.
- Check Opera preference settings and modify and settings that would improve your Internet experience.
- Safari
- Review available resources under Apple: Safari Support.
- Check Safari preferences and modify any settings that would improve your Internet experience.
- Brave
- Configure browser extensions and add-ons.
- Review Websitebuilders: Installing Plug-ins and ComputerHope: How to Disable or Remove Installed Extensions in Any Browser.
- View add-ons installed in your browser(s). Disable any add-ons you don't use.
- Search the Internet for the most popular add-ons for your browser(s). Consider adding and testing a password manager, ad blocker, autoplay blocker, grammar checker, or other add-on.
- Compare browser HTML5 compatibility.
- Review HTML Accessibility and HTML5 Test: How well does your browser support HTML5?. Note the version numbers of the browsers being compared and how well those versions met the HTML5 standard. All browsers have made improvements since the comparisons were made, but the results can be an indicator of how important standards are to a given browser's development team.
Lesson Summary
[edit | edit source]- A web browser (commonly referred to as a browser) is a software application for retrieving, presenting and traversing information resources on the World Wide Web.[5]
- The most popular web browsers are Google Chrome, Microsoft Edge (preceded by Internet Explorer), Firefox, Safari, and Opera.[6][7]
- The primary purpose of a web browser is to bring information resources to the user ("retrieval" or "fetching"), allowing them to view the information ("display", "rendering"), and then access other information ("navigation", "following links").[8]
- The prefix of the URL, the Uniform Resource Identifier or URI, determines how the URL will be interpreted.[9]
- The most commonly used kind of URI starts with http: and identifies a resource to be retrieved over the Hypertext Transfer Protocol (HTTP).[10]
- Many browsers also support a variety of other prefixes, such as https: for HTTPS, ftp: for the File Transfer Protocol, and file: for local files.[11]
- Prefixes that the web browser cannot directly handle are often handed off to another application entirely. For example, mailto: URIs are usually passed to the user's default e-mail application, and news: URIs are passed to the user's default newsgroup reader.[12]
- HTML and associated content (image files, formatting information such as CSS, etc.) is passed to the browser's layout engine to be transformed from markup to an interactive document, a process known as "rendering".[13]
- Most browsers can display images, audio, video, and XML files, and often have plug-ins to support Flash applications and Java applets.[14]
- All major web browsers allow the user to open multiple information resources at the same time, either in different browser windows or in different tabs of the same window.[15]
- Major browsers also include pop-up blockers to prevent unwanted windows from "popping up" without the user's consent.[16]
- Most web browsers can display a list of web pages that the user has bookmarked so that the user can quickly return to them. Bookmarks are also called "Favorites" in Internet Explorer.[17]
- In addition, all major web browsers have some form of built-in web feed aggregator.[18]
- Most browsers can be extended via plug-ins, downloadable components that provide additional features.[19]
- Most major web browsers have common user interface elements:[20]
- Back and forward buttons to go back to the previous resource and forward respectively.
- A refresh or reload button to reload the current resource.
- A stop button to cancel loading the resource. In some browsers, the stop button is merged with the reload button.
- A home button to return to the user's home page.
- An address bar to input the Uniform Resource Identifier (URI) of the desired resource and display it.
- A search bar to input terms into a web search engine. In some browsers, the search bar is merged with the address bar.
- A status bar to display progress in loading the resource and also the URI of links when the cursor hovers over them, and page zooming capability.
- The viewport, the visible area of the webpage within the browser window.
- The ability to view the HTML source for a page.
- An incremental find features to search within a web page.
- A browser extension is a plug-in that extends the functionality of a web browser.[21]
- Many browsers have an online store that allows users to find extensions and see lists of popular extensions.[22]
- Browser extensions are used for improving a browser's user interface, security or accessibility, blocking advertisements, and various other features to make browsing the internet easier and more pleasant.[23]
- Browser extensions have access to everything done by the browser, and can do things like inject ads into web pages, or make "background" HTTP requests to third-party servers. As a result, a malicious browser extension may take action against the interest of the user that installed it.[24]
Key Terms
[edit | edit source]- aggregator
- A web site or computer software that aggregates a specific type of information from multiple online sources.[25]
- ActiveX
- An early software framework developed by Microsoft to enhance browser functionality, which was supported only by x86-based computers using Internet Explorer.[26]
- bookmark
- A Uniform Resource Identifier (URI) that is stored for later retrieval in any of various storage formats.[27]
- browser cache
- An information technology for the temporary storage of web documents, such as HTML pages and images, to reduce bandwidth usage, server load, and perceived lag.[28]
- CAPTCHA
- A type of challenge-response test used in computing to determine whether or not the user is human.[29]
- cookie
- A small piece of data sent from a website and stored on the user's computer by the user's web browser while the user is browsing.[30]
- favorite
- See bookmark.
- Flash
- A multimedia software platform developed by Adobe which used for production of animations, rich Internet applications, desktop applications, mobile applications and mobile games.[31]
- history
- The list of web pages a user has visited recently.[32]
- home page
- The initial or main web page of a website or a browser.[33]
- hyperlink
- A reference to data that the reader can directly follow either by clicking, tapping, or hovering.[34]
- Java applet
- A small application which is written in Java or another programming language that compiles to Java bytecode and delivered to users in the form of that bytecode.[35]
- mashup
- A web page, or web application, that uses content from more than one source to create a single new service displayed in a single graphical interface.[36]
- plug-in
- A software component that adds a specific feature to an existing computer program.[37]
- pop-up ad
- Online advertising using a new web browser window for display.[38]
- proxy server
- A computer system or an application that acts as an intermediary for requests from clients seeking resources from other servers.[39]
- RSS
- A type of web feed which allows users to access updates to online content in a standardized, computer-readable format.[40]
- Silverlight
- A deprecated application framework developed by Microsoft for writing and running rich Internet applications.[41]
- Uniform Resource Identifier (URI)
- A string of characters used to identify a resource.[42]
- Uniform Resource Locator (URL)
- A reference to a web resource that specifies its location on a computer network and a mechanism for retrieving it.[43]
- web feed
- A subscription-supporting data format used for providing users with frequently updated content.[44]
Assessments
[edit | edit source]- Flashcards: Quizlet: Web Browsers
- Quiz: Quizlet: Web Browsers
See Also
[edit | edit source]- Computer Skills/Basic/Internet
- IC3/Internet Fundamentals
- Web Designer Depot: Best Browsers for Developers
References
[edit | edit source]- ↑ Wikipedia: Web browser
- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Training.gov.au: ICTICT103 - Use, communicate and search securely on the Internet
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ NetMarketShare: Browser market share
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Web browser
- ↑ Wikipedia: Browser extension
- ↑ Wikipedia: Browser extension
- ↑ Wikipedia: Browser extension
- ↑ Wikipedia: Browser extension
- ↑ Wikipedia: Aggregator
- ↑ Wikipedia: ActiveX
- ↑ Wikipedia: Bookmark (World Wide Web)
- ↑ Wikipedia: Web cache
- ↑ Wikipedia: CAPTCHA
- ↑ Wikipedia: HTTP cookie
- ↑ Wikipedia: Adobe Flash
- ↑ Wikipedia: Web browsing history
- ↑ Wikipedia: Home page
- ↑ Wikipedia: Hyperlink
- ↑ Wikipedia: Java applet
- ↑ Wikipedia: Mashup (web application hybrid)
- ↑ Wikipedia: Plug-in (computing)
- ↑ Wikipedia: Pop-up ad
- ↑ Wikipedia: Proxy server
- ↑ Wikipedia: RSS
- ↑ Wikipedia: Microsoft Silverlight
- ↑ Wikipedia: Uniform Resource Identifier
- ↑ Wikipedia: URL
- ↑ Wikipedia: Web feed
Lesson 3 - Search Engines
[edit | edit source]


A web search engine is a software system that is designed to search for information on the World Wide Web.[1] This lesson introduces search engines.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[2][3][4]
- Use different types of Web search engines effectively.
- Search the Internet
- Review organisational guidelines on Internet access
- Open Internet application and locate and access a search engine on the Internet, and define search expressions based on data required
- Enter appropriate key words into the search engine to locate desired information
- Refine a search depending on outcomes of original search
- Save search expression results and present them in a report according to information requirements
- Create a bookmark within the Internet browser or a link for the required web page for the key results
- Save key results in a bookmark folder
- Modify Internet browser options for printing and print a web page
- Close Internet browser
- Conduct an advanced search
- Use search tools and advanced search features
- Use Boolean search techniques when required to enhance the search
- Use multiple or meta-search tools with a range of key words
- Use search engines particular to a field of knowledge to refine the outcome
- Access related virtual community sites and newsgroups, and note their objectives and operational arrangements
- Conduct a search with domain names to refine the search
- Use information that has been located
- Cross reference information found by using several websites to determine accuracy of information
- Check date that website was last updated or properties of website to determine currency of information
- Determine website authority by looking at copyright statements, privacy statements and organisational information
- Save and print information found in different file forms
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: Search Engines
- YouTube: How Search Works
- YouTube: Basic Search Strategies
- YouTube: Google Advanced Search Tips
- YouTube: How do I search Google effectively? Part I: Boolean Operators & Phrase Searching
- YouTube: How do I effectively search Google? Part II: Domain Limit Searching
- YouTube: What is Search Engine Optimization (SEO)
Student Presentations
[edit | edit source]Activities
[edit | edit source]- Complete the following tutorials:
- Compare search engines.
- Search for
web search engineusing Google, Bing, Yahoo, and Ask. Compare the results from each search engine. Which search engine has the best user interface? Which search engine provides the most useful results? - Using your preferred search engine, search for
search engine market share. Which search engine has the highest market share?
- Search for
- Use search engines.
- Search using exact phrases. Review Google: Search Operators. Using your preferred search engine, search for the exact phrase
"search engine" "market share". Compare the results of searching without quotes and with quotes. Does an exact phrase search return more accurate results for this search? - Search a specific site. Review Google: Search Operators. Using your preferred search engine, search Wikiversity for information on search engines using
search engine site:wikiversity.org. Compare the results with using Wikiversity's built in Special:Search page. Which search approach provides the most useful results? - Use a Boolean search. Review Google: Search Operators. Using your preferred search engine, search for information on search engines or SEO using
"search engine" or SEO. Review the results and read any that interest you. - Evaluate search results. Review Georgetown: Evaluating Internet Reources. Based on these guidelines, identify which of the search results above were the most reliable or credible.
- Search using exact phrases. Review Google: Search Operators. Using your preferred search engine, search for the exact phrase
- Learn about Search Engine Optimization (SEO):
- Add a web page to a search engine. Review Google: Get your content on Google. Practice by adding this Wikiversity page URL to Google Search.
- Learn about Artificial Intelligence (AI)
- Review IBM Technologyː AI vs. Machine Language to view the difference between machine learning and AI.
- Review IBM Technologyː Risks of Large Language Models to view the shortcomings of large language models.
- Read Tech Explainedː 9 Best Alternatives of ChatGPT to identify alternatives to ChatGPT.
- Use ChatGPTː Login. Once you have an account, explore the capabilities of ChatGPT.
- To get to the playground: Log in. Scroll down the page to review the variety of examples. At the bottom of the page, click on "message ChatGPT" and enter a message to search. Create several queries to ChatGPT that interest you.
- Share one of your queries by posting the query and the ChatGPT response.
- Evaluate your experience with ChatGPT .
- Use the Internet Archive.
- Use the Internet Archive Wayback Machine to view historical web page versions, including those that are no longer available on the primary site. For example, versions of the Wikiversity home page are available going back to 2005.
- Review Archive.org: If You See Something, Save Something. Add a page URL to the Internet Archive.
- Cite a web page.
- Use Special:CiteThisPage to cite a Wikiversity web page. For example, this page's citation information is at Special:CiteThisPage/Internet Fundamentals/Collection. Compare the different citation formats available. Do all formats include the same information?
Lesson Summary
[edit | edit source]- A web search engine is a software system that is designed to search for information on the World Wide Web.[5]
- Search engines maintain real-time information by running an algorithm on a web crawler.[6]
- Web search engines get their information by web crawling from site to site.[7]
- Indexing means associating words and other definable tokens found on web pages to their domain names and HTML-based fields.[8]
- Beyond simple keyword lookups, search engines offer their own GUI- or command-driven operators and search parameters to refine the search results.[9]
- Most search engines support the use of the boolean operators AND, OR and NOT to help end users refine the search query.[10]
- The usefulness of a search engine depends on the relevance of the result set it gives back.[11]
- Most Web search engines are commercial ventures supported by advertising revenue and thus some of them allow advertisers to have their listings ranked higher in search results for a fee.[12]
- Search engines that do not accept money for their search results make money by running search related ads alongside the regular search engine results.[13]
- The most popular search engines are Google, Bing, Baidu, and Yahoo![14]
- Many search engines such as Google and Bing provide customized results based on the user's activity history.[15]
- Search engine submission is a process in which a webmaster submits a website directly to a search engine.[16]
- Web sites or web pages should be submitted to a search engine to add an entirely new web site without waiting for a search engine to discover it, and to have a web site's record updated after a substantial redesign.[17]
- Search engine optimization (SEO) is the process of affecting the visibility of a website or a web page in a web search engine's unpaid results—often referred to as "natural", "organic", or "earned" results.[18]
- AI is a field of computer science that focuses on creating machines that can work and learn like human.[19]
Key Terms
[edit | edit source]- Boolean operator
- A symbol or word used to connect two or more search terms in a grammatically valid way, such that the value of the compound sentence produced depends only on that of the original terms and on the meaning of the operator. Common search Boolean operators include AND, OR, and NOT.[20]
- cache
- A hardware or software component that stores data so future requests for that data can be served faster.[21]
- data mining
- The computing process of discovering patterns in large data sets involving methods at the intersection of machine learning, statistics, and database systems[22]
- filter bubble
- A separation of users from information that disagrees with their viewpoints, resulting from personalized searches based on information about the user such as location, past click-behavior and search history.[23]
- index
- A list of words or phrases and associated pointers to where useful material relating to that word or phrase can be found in a document or collection of documents.[24]
- keyword
- A term that captures the essence of the topic of a document.[25]
- link rot
- The process by which hyperlinks on individual websites or the Internet in general point to web pages, servers or other resources that have become permanently unavailable.[26]
- machine learning
ːMachine learning is a scientific discipline that is concerned with the design and development of algorithms that allow computers to evolve behaviors based on empirical data, such as from sensor data or databases.[27]
- meta tag
- Tags used in HTML and XHTML documents to provide structured metadata about a Web page.[28]
- metadata
- Data [information] that provides information about other data.[29]
- proximity
- A numerical description of how far apart objects are.[30]
- query
- A request that a user enters into a web search engine to satisfy his or her information needs.[31]
- rank
- A relationship between a set of items such that, for any two items, the first is either 'higher than', 'lower than' or 'equal to' the second.[32]
- relevance
- The concept of one topic being connected to another topic in a way that makes it useful to consider the second topic when considering the first.[33]
- robots.txt
- A standard used by websites to communicate with web crawlers and other web robots.[34]
- Search Engine Optimization (SEO)
- The process of affecting the visibility of a website or a web page in a web search engine's unpaid results.[35]
- site map
- A list of pages of a web site accessible to crawlers or users.[36]
- web crawler
- An Internet bot that systematically browses the World Wide Web, typically for the purpose of Web indexing.[37]
- web directory
- An online list or catalog of websites, most often built manually by human editors.[38]
- web robot
- A software application that runs automated tasks (scripts) over the Internet.[39]
- weighting
- Emphasizing the contribution of some aspects of a phenomenon (or of a set of data) to a final effect or result.[40]
Assessments
[edit | edit source]- Flashcards: Quizlet: Search Engines
- Quiz: Quizlet: Search Engines
See Also
[edit | edit source]References
[edit | edit source]- ↑ Wikipedia: Web search engine
- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Training.gov.au: ICTICT103 - Use, communicate and search securely on the Internet
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Web search engine
- ↑ Wikipedia: Search engine optimization
- ↑ Artificial intelligence
- ↑ Wikipedia: Logical connective
- ↑ Wikipedia: Cache (computing)
- ↑ Wikipedia: Data mining
- ↑ Wikipedia: Filter bubble
- ↑ Wikipedia: Index (publishing)
- ↑ Wikipedia: Index term
- ↑ Wikipedia: Link rot
- ↑ Machine learning
- ↑ Wikipedia: Meta tag
- ↑ Wikipedia: Metadata
- ↑ Wikipedia: Proximity
- ↑ Wikipedia: Web search query
- ↑ Wikipedia: Ranking
- ↑ Wikipedia: Relevance
- ↑ Wikipedia: Robots exclusion standard
- ↑ Wikipedia: Search engine optimization
- ↑ Wikipedia: Site map
- ↑ Wikipedia: Web crawler
- ↑ Wikipedia: Web directory
- ↑ Wikipedia: Internet bot
- ↑ Wikipedia: Weighting
Lesson 4 - Email
[edit | edit source]


Electronic mail (email) is a method of exchanging messages between people using electronics.[1] This lesson introduces email.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[2][3][4]
- Use e-mail clients to send simple messages and files to other Internet users.
- Use email for communications
- Open email application package, create new email message and add addressees
- Compose text of an email message according to organisational guidelines, and spell check and edit text as required
- Create and add an automatic signature for the user
- Attach files to email message where required
- Determine and set priority and send email message
- Reply to and forward a received message using available features
- Open and save an attachment to the relevant folder
- Search for, sort and save email message using available settings
- Adjust email accounts to restrict and quarantine possible email security problems
- Print email message as required
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: Gmail: Sending Email.
- YouTube: Gmail: Responding to Email with Gmail.
- YouTube: How Email Works
- YouTube: How to know if an email is real
Student Presentations
[edit | edit source]Activities
[edit | edit source]- Complete the following tutorials:
- Send, receive, and respond to email.
- If you don't already have an email account, consider signing up for a Google Gmail, Microsoft Outlook, or Yahoo! Mail account.
- Complete the GCF Global: Gmail: Sending Email tutorial.
- Use your email account to send an email message.
- Reply to an email message you receive from someone else.
- Use an email client program.
- Review Wikipedia: Mozilla Thunderbird.
- Review InMotion: How to Setup your Email Account in Thunderbird.
- Download and install Mozilla: Thunderbird.
- Complete the tutorial Thunderbirdː Email Setup
- Configure Thunderbird to connect to your email account.
- Use Thunderbird to send and receive email.
- View email message headers.
- Review Wikipedia: Email spoofing.
- Review Google: Message headers or Livewire: How to View the Source of a Message in Mozilla Thunderbird to learn how to view email headers in your webmail service or email client.
- Follow the instructions to view message headers for a message you received. Verify that the message was sent by the displayed
From:address rather than being spoofed.
- Use Internet mailing lists.
- Research popular Internet mailing lists. Consider signing up for any that interest you.
- Research bulk email restrictions and identify appropriate ways to send bulk email messages.
Lesson Summary
[edit | edit source]- Electronic mail (email) is a method of exchanging messages between people using electronics.[5]
- Today's email systems are based on a store-and-forward model. Email servers accept, forward, deliver, and store messages.[6]
- Multipurpose Internet Mail Extensions (MIME) carry text in other character sets and support multimedia content attachments.[7]
- The typical sequence of events in transmitting a message is:[8]
- A mail user agent (email program) sends the message to its outbound mail server using SMTP.
- The mail server determines the destination mail server based on the domain name of the email address and corresponding DNS MX record.
- The mail server sends the message to the destination mail server using SMTP.
- The destination mail server delivers the message to the recipient's mailbox.
- The recipient's mail user agent retrieves the message from the server using either POP or IMAP.
- Message headers include fields for
Date:,From:,To:,Subject:,Cc:, andBcc:.[9] - Most modern graphic email clients allow the use of either plain text or HTML for the message body at the option of the user.[10]
- Messages are exchanged between hosts using the Simple Mail Transfer Protocol with software programs called mail transfer agents (MTAs); and delivered to a mail store by programs called mail delivery agents (MDAs).[11]
- Accepting a message obliges an MTA to deliver it, and when a message cannot be delivered, that MTA must send a bounce message back to the sender, indicating the problem.[12]
- Users can retrieve their messages from servers using standard protocols such as POP or IMAP, or with a proprietary protocol specific to Novell Groupwise, Lotus Notes, or Microsoft Exchange Servers.[13]
- Programs used by users for retrieving, reading, and managing email are called mail user agents (MUAs).[14]
- Mail can be stored on the client, on the server side, or in both places.[15]
- Many current email users do not run MTA, MDA or MUA programs themselves, but use a web-based email platform instead.[16]
- A URL beginning with
mailto:may be used to create a hyperlink to an email address, such as:
mailto:recipient@example.com?subject=Email%20Example[17] - The Post Office Protocol 3 (POP3) is a mail access protocol used by a client application to read messages from the mail server. Received messages are often deleted from the server.[18]
- The Internet Message Access Protocol (IMAP) provides features to manage a mailbox from multiple devices. IMAP shows the headers of messages, the sender and the subject and the device needs to request to download specific messages. Usually mail is left in folders on the mail server.[19]
- An electronic mailing list or email list is a special use of email that allows for widespread distribution of information to many Internet users.[20]
- Electronic mailing lists usually are fully or partially automated through the use of special mailing list software and a reflector address set up on a server capable of receiving email.[21]
- Incoming messages sent to the reflector address are processed by the software, and, depending on their content, are acted upon internally (in the case of messages containing commands directed at the software itself) or are distributed to all email addresses subscribed to the mailing list.[22]
- Electronic mailing list servers may be set to forward messages to subscribers of a particular mailing list either individually as they are received by the list server, or in digest form in which all messages received on a particular day by the list server are combined into one email that is sent once per day to subscribers.[23]
Key Terms
[edit | edit source]- attachment
- A computer file sent along with an email message.[24]
- BCC
- Allows the sender of a message to conceal the person entered in the BCC field from the other recipients.[25]
- CC
- Indicates those who are to receive a copy of a message addressed primarily to another recipient.[26]
- Internet Message Access Protocol (IMAP)
- An Internet standard protocol used by e-mail clients to retrieve e-mail messages from a mail server.[27]
- Mail Delivery Agent (MDA)
- A computer software component that is responsible for the delivery of e-mail messages to a local recipient's mailbox.[28]
- Mail Transfer Agent (MTA)
- Software that transfers electronic mail messages from one computer to another using a client–server application architecture.[29]
- Mail User Agent (MUA)
- A computer program used to access and manage a user's email.[30]
- Multipurpose Internet Mail Extensions (MIME)
- An Internet standard that extends the format of email to support attachments and non-ASCII character sets.[31]
- netiquette
- The rules of etiquette that apply when communicating over the Internet or social networks or devices.[32]
- open relay
- An SMTP server configured in such a way that it allows anyone on the Internet to send e-mail through it, not just mail destined to or originating from known users.[33]
- opt-in email
- Describes when someone is given the option to receive email, typically for some sort of mailing list, newsletter, or advertising.[34]
- Personal Information Management (PIM)
- The activities people perform in order to acquire, organize, maintain, retrieve and use personal information items.[35]
- Post Office Protocol (POP)
- An application-layer Internet standard protocol used by local e-mail clients to retrieve e-mail from a remote server over a TCP/IP connection.[36]
- Pretty Good Privacy (PGP)
- A program used for signing, encrypting, and decrypting e-mail messages and to increase the security of e-mail communications. [37]
- Secure MIME (S/MIME)
- A standard for public key encryption and signing of MIME data.[38]
- Simple Mail Transfer Protocol (SMTP)
- An Internet standard for electronic mail (email) transmission.[39]
- snail mail
- Refers to letters and missives carried by conventional postal delivery services.[40]
- spam
- The use of electronic messaging systems to send an unsolicited message.[41]
- spam filter
- Processing of email to organize or block it according to specified criteria.[42]
Assessments
[edit | edit source]- Flashcards: Quizlet: CIW IBA Lesson 7
- Quiz: Quizlet: CIW IBA Lesson 7
See Also
[edit | edit source]- Computer Skills/Basic/Email
- Computer Skills/Intermediate/Email
- Web 2.0 for Professional Use/E-Mail
References
[edit | edit source]- ↑ Wikipedia: Email
- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Training.gov.au: ICTICT103 - Use, communicate and search securely on the Internet
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Email
- ↑ Wikipedia: Electronic mailing list
- ↑ Wikipedia: Electronic mailing list
- ↑ Wikipedia: Electronic mailing list
- ↑ Wikipedia: Electronic mailing list
- ↑ Wikipedia: Email attachment
- ↑ Wikipedia: Blind carbon copy
- ↑ Wikipedia: Carbon copy
- ↑ Wikipedia: Internet Message Access Protocol
- ↑ Wikipedia: Mail delivery agent
- ↑ Wikipedia: Message transfer agent
- ↑ Wikipedia: Email client
- ↑ Wikipedia: MIME
- ↑ Wikipedia: Etiquette in technology
- ↑ Wikipedia: Open mail relay
- ↑ Wikipedia: Opt-in email
- ↑ Wikipedia: Personal information management
- ↑ Wikipedia: Post Office Protocol
- ↑ Wikipedia: Pretty Good Privacy
- ↑ Wikipedia: S/MIME
- ↑ Wikipedia: Simple Mail Transfer Protocol
- ↑ Wikipedia: Snail mail
- ↑ Wikipedia: Spamming
- ↑ Wikipedia: Email filtering
Lesson 5 - Social Media
[edit | edit source]








Social media are computer-mediated technologies that facilitate the creation and sharing of information, ideas, career interests and other forms of expression via virtual communities and networks.[1] This lesson introduces social media and social networking.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[2][3][4]
- Define essential social networking and Web 2.0 concepts.
- Describe the different types of social media tools and applications
- Explain the characteristics of the term ‘social media’
- Identify different types of social-media tools and applications
- Illustrate some of the issues associated with the use of social media tools and applications
- Compare different types of social media tools and applications
- Select one social media type to review
- Review the most popular tools, and applications, within that social media type
- Itemise the benefits across a range of the most popular tools and applications
- Select the most appropriate social media tool or application
- Set up and use, popular social media tools and applications
- Identify the social media tools and applications available for possible implementation
- Initiate the preferred social media tools, and applications, for use
- Establish the social media interface, using text and file content
- Initiate social networking interaction
- Test and evaluate tools, and applications, for ease of use
- Present the findings
Readings
[edit | edit source]Multimedia
[edit | edit source]Student Presentations
[edit | edit source]Activities
[edit | edit source]- Complete the tutorial TutorialsPoint: Social Networking. Based on the information provided, decide which of the following social media sites interest you.
- Complete one or more of the following. If you are completing this course as part of a real-world class, consider sharing account information with your classmates, or setting up a class group and/or class hashtag.
- Review GCFLearnFree: Blog Basics. Research free traditional blogging sites and create a new blog.
- Review GCFLearnFree: Facebook. If you don't already have a Facebook account, sign up for Facebook and set up your account.
- Review GCFLearnFree: Instagram. If you don't already have an Instagram account, sign up for Instagram and share photos.
- Review GCFLearnFree: LinkedIn Basics. If you don't already have a LinkedIn account, sign up for LinkedIn and set up your profile.
- Review GCFLearnFree: Pinterest. If you don't already have a Pinterest account, sign up for Pinterest and create a board.
- Review GCFLearnFree: Snapchat. If you don't already have a Snapchat account, sign up for Snapchat and share photos.
- Review Smart Insights: The Honeycomb model. Evaluate each of the most popular social media sites (Facebook, Instagram, LinkedIn, Pinterest, Reddit, Snapchat, Tumblr, Twitter, YouTube) based on their level of support for each of the honeycomb framework elements (identity, conversations, sharing, presence, relationships, reputation, groups). Which sites support the full honeycomb framework? Which sites are lacking elements?
Lesson Summary
[edit | edit source]- Social media are computer-mediated technologies that facilitate the creation and sharing of information, ideas, career interests and other forms of expression via virtual communities and networks.[5]
- Common social media features include:[6]
- Social media are interactive Web 2.0 Internet-based applications.
- User-generated content and data generated through all online interactions are the lifeblood of social media.
- Users create service-specific profiles for the website or app that are designed and maintained by the social media organization.
- Social media facilitate the development of online social networks by connecting a user's profile with those of other individuals or groups.
- Popular social media websites include Facebook, Instagram, LinkedIn, Pinterest, Reddit, Snapchat, Tumblr, Twitter, and YouTube.[7][8][9]
- Facebook supports user profiles, friends, message exchange, status updates, photo sharing, software applications, groups, and notifications.[10]
- Instagram supports photo and video sharing, digital filter application, geotags, hashtags, linking to other Instagram content, and connecting Instagram accounts to other social media profiles.[11]
- LinkedIn supports user profiles, professional networking, curriculum vitae (CV) / résumé sharing, and connections to other users.[12]
- Pinterest supports sharing and categorization of images using boards, and following other users' boards.[13]
- Reddit supports social news aggregation, web content rating, and discussion through text posts and direct links, with users rating submissions.[14]
- Snapchat supports image and multimedia messaging, with pictures and messages only available for a short time before they become inaccessible.[15]
- Tumblr supports microblogging with multimedia and other content, and following other users' blogs.[16]
- Twitter supports posting of 280-character messages known as "tweets", and following other users.[17]
- YouTube supports video-sharing, rating, and following other users' submissions.[18]
- Social media changes the way individuals and large organizations communicate.[19]
- For content contributors, the benefits of participating in social media have gone beyond simply social sharing to building a reputation and bringing in career opportunities and monetary income.[20]
- Social media operate in a dialogic transmission system (many sources to many receivers). This is in contrast to traditional media which operates under a monologic transmission model (one source to many receivers).[21]
- Social media can help to improve individuals' sense of connectedness with real or online communities and social media can be an effective communication (or marketing) tool for corporations, entrepreneurs, nonprofit organizations, including advocacy groups and political parties and governments.[22]
- Concerns have been raised about possible links between heavy social media use and depression, and issues of cyberbullying, online harassment and "trolling".[23]
- Companies are increasingly using social media monitoring tools to monitor, track, and analyze online conversations on the Web about their brand or products or about related topics of interest.[24]
- Social media services are defined by seven elements known as the "honeycomb framework":[25]
- Identity - The extent to which users reveal their personal or professional identities.
- Conversations - The extent to which users communicate with other users.
- Sharing - The extent to which users exchange, distribute, and receive content.
- Presence - The extent to which users know if other users are available.
- Relationships - The extent to which users can be connected to other users.
- Reputation - The extent to which users can identify the standing of users.
- Groups - The extent to which users can form communities and sub-communities.
- Chatbots and social bots are programmed to mimic natural human interactions such as liking, commenting, following, and unfollowing on social media platforms. The ability for bots to mimic human interaction makes it difficult for participants, marketers, and data analysts to differentiate between human interactions and automated bot interactions.[26]
- Privacy rights advocates warn users on social media about the collection of their personal data.
- A Web 2.0 website may allow users to interact and collaborate with each other in a social media dialogue as creators of user-generated content in a virtual community, in contrast to the first generation of Web 1.0-era websites where people were limited to the passive viewing of content.[27]
Key Terms
[edit | edit source]- blog
- A discussion or informational website published on the World Wide Web consisting of discrete, often informal diary-style text entries.[28]
- crowdsourcing
- Individuals or organizations use contributions from Internet users to obtain needed services or ideas.[29]
- folksonomy
- A system in which users apply public tags to online items, typically to aid them in finding those items.[30]
- instant messaging
- A type of online chat that offers real-time text transmission over the Internet.[31]
- netiquette
- The rules of etiquette that apply when communicating over the Internet or social networks or devices.[32]
- presence
- A status indicator that conveys ability and willingness of a potential communication partner to communicate.[33]
- Semantic Web
- A common framework that allows data to be shared and reused across application, enterprise, and community boundaries.[34]
- social networking
- An online platform which people use to build social networks or social relations with other people who share similar personal or career interests, activities, backgrounds or real-life connections.[35]
- spim
- A type of spam targeting users of instant messaging (IM) services[36]
- text messaging
- The act of composing and sending electronic messages, typically consisting of alphabetic and numeric characters, between two or more users of fixed or portable devices.[37]
- Web 2.0
- Websites that emphasize user-generated content, usability, and interoperability for end users.[38]
- wiki
- A website on which users collaboratively modify content and structure directly from the web browser.[39]
Assessments
[edit | edit source]- Flashcards: Quizlet: Social Media
- Quiz: Quizlet: Social Media
See Also
[edit | edit source]References
[edit | edit source]- ↑ Wikipedia: Social media
- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Training.gov.au: ICTWEB201 - Use social media tools for collaboration and engagement
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ DreamGrow: Top 10 Social Networking Sites by Market Share of Visits
- ↑ Smart Insights: Global social media research summary 2017
- ↑ Wikipedia: Facebook
- ↑ Wikipedia: Instagram
- ↑ Wikipedia: LinkedIn
- ↑ Wikipedia: Pinterest
- ↑ Wikipedia: Reddit
- ↑ Wikipedia: Snapchat
- ↑ Wikipedia: Tumblr
- ↑ Wikipedia: Twitter
- ↑ Wikipedia: YouTube
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Social media
- ↑ Wikipedia: Web 2.0
- ↑ Wikipedia: Blog
- ↑ Wikipedia: Crowdsourcing
- ↑ Wikipedia: Folksonomy
- ↑ Wikipedia: Instant messaging
- ↑ Wikipedia: Etiquette in technology
- ↑ Wikipedia: Presence information
- ↑ Wikipedia: Semantic Web
- ↑ Wikipedia: Social networking service
- ↑ Wikipedia: Messaging spam
- ↑ Wikipedia: Text messaging
- ↑ Wikipedia: Web 2.0
- ↑ Wikipedia: Wiki
Lesson 6 - Communications
[edit | edit source]



This lesson introduces Internet communications services, including Voice over IP, file transfer, file sharing, and screen sharing.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[1][2]
- Define and use additional networking and Internet services.
- Efficiently transmit text and binary files using popular Internet services.
Readings
[edit | edit source]- Wikipedia: Voice over IP
- Wikipedia: Web conferencing
- Wikipedia: Remote desktop software
- Wikipedia: File transfer
- Wikipedia: File Transfer Protocol
- Wikipedia: Peer-to-peer file sharing
- Wikipedia: SMS
Multimedia
[edit | edit source]- YouTube: What is VoIP?
- YouTube: Get Started with Web Conferencing
- YouTube: Remote Desktop Applications
- YouTube: What is FTP (File Transfer Protocol) and how do I use it?
- YouTube: Peer to Peer Filesharing - Simply Speaking
Activities
[edit | edit source]- Internet Services
- Complete the tutorial TutorialsPoint: Internet Services.
- VoIP / Messaging
- Complete the tutorial TutorialsPoint: Internet Collaboration Overview. Based on the information provided, decide which of the following communication applications interest you. Then complete one of the following VoIP / messaging tutorials:
- Complete the tutorial GCFLearnFree: Skype. If you don't already have a Skype account, sign up for Skype and call or text a friend.
- Complete the tutorial GCFLearnFree: Google Hangouts. If you don't already have a Hangouts account, sign up for Hangounts and call or text a friend.
- Complete the tutorial GCFLearnFree: WhatsApp. If you don't already have a WhatsApp account, sign up for WhatsApp and call or text a friend.
- Complete the tutorial GCFLearnFree: Snapchat. If you don't already have a Snapchat account, sign up for Snapchat and send snaps to a friend.
- Complete the tutorial TutorialsPoint: Internet Collaboration Overview. Based on the information provided, decide which of the following communication applications interest you. Then complete one of the following VoIP / messaging tutorials:
- Screen Sharing / Remote Desktop
- Research remote desktop applications and use one of the following programs to remotely connect to another computer:
- FTP
- Review ExaVault: How to Access an FTP Server from the Browser or Hostinger: What is FTP?. Using a browser or FTP client, https://dlptest.com/ftp-test/ provides a demo FTP server to practice with.
- Intellectual Property
- Review RIAA:About Piracy. Research legal issues and potential penalties related to illegal peer-to-peer file sharing.
Lesson Summary
[edit | edit source]- Voice over Internet Protocol (also voice over IP, VoIP or IP telephony) is a methodology and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet.[3]
- The terms Internet telephony, broadband telephony, and broadband phone service specifically refer to the provisioning of communications services (voice, fax, SMS, voice-messaging) over the public Internet, rather than via the public switched telephone network (PSTN).[4]
- Instead of being transmitted over a circuit-switched network, VoIP information is packetized, and transmission occurs as IP packets over a packet-switched network.[5]
- VoIP is available on dedicated phones, smartphones, personal computers, and Internet access devices. Calls and SMS text messages may be sent over 3G/4G or Wi-Fi.[6]
- File transfer is the transmission of a computer file through a communication channel from one computer system to another. File transfer options include: transparent file transfers over network file systems, explicit file transfers from dedicated file transfer services like FTP or HTTP, and distributed file transfers over peer-to-peer networks like Bittorent or Gnutella.[7]
- The File Transfer Protocol (FTP) is a standard network protocol used for the transfer of computer files between a client and server on a computer network.[8]
- FTP is built on a client-server model architecture and uses separate control and data connections between the client and the server.[9]
- FTP users may authenticate themselves with a clear-text sign-in protocol, normally in the form of a username and password, but can connect anonymously if the server is configured to allow it.[10]
- For secure transmission that protects the username and password, and encrypts the content, FTP is often secured with SSL/TLS (FTPS).[11]
- SSH File Transfer Protocol (SFTP) is sometimes also used instead of FTP/FTPS, but it is technologically different.[12]
- Peer-to-peer file sharing is the distribution and sharing of digital media using peer-to-peer (P2P) networking technology.[13]
- P2P file sharing allows users to access media files such as books, music, movies, and games using a P2P software program that searches for other connected computers on a P2P network to locate the desired content.[14]
- The nodes (peers) of P2P networks are end-user computers and distribution servers are not required.[15]
- There are five types of P2P users: users who create services, users who allow services, users who facilitate search, users who allow communication, users who are uncooperative and free ride.[16]
- Researchers have examined potential P2P security risks including the release of personal information, bundled spyware, and viruses downloaded from the network.[17]
- The act of file sharing is not illegal and peer-to-peer networks are used for legitimate purposes. The legal issues in file sharing involve violating the laws of copyrighted material.[18]
- Remote desktop refers to a software or operating system feature that allows a personal computer's desktop environment to be run remotely on one system while being displayed on a separate client device.[19]
- Remote desktop applications may allow attaching to an existing user's session and "remote controlling", either displaying the remote control session or blanking the screen.[20]
- Remote desktop software captures the mouse and keyboard inputs from the local computer (client) and sends them to the remote computer (server). The remote computer in turn sends the display commands to the local computer.[21]
Key Terms
[edit | edit source]- application sharing
- An element of remote access, falling under the collaborative software umbrella, that enables two or more users to access a shared application or document from their respective computers simultaneously in real time.[22]
- collaboration
- Application software designed to help people involved in a common task to achieve goals. It can be divided into three categories depending on the level of collaboration: communication, conferencing and co-ordination.[23]
- convergence
- The tendency that as technology changes, different technological systems evolve toward performing similar tasks across information technologies, telecommunication, consumer electronics, and entertainment.[24]
- FTP
- A standard network protocol used for the transfer of computer files between a client and server on a computer network.[25]
- remote access
- Connection to a data-processing system from a remote location, for example, through a Remote Access Service or virtual private network.[26]
- remote desktop software
- A software or operating system feature that allows a personal computer's desktop environment to be run remotely on one system while being displayed on a separate client device.[27]
- RDP
- A proprietary protocol developed by Microsoft, which provides a user with a graphical interface to connect to another computer over a network connection.[28]
- unified communications
- The integration of enterprise communication services such as instant messaging (chat), presence information, voice, mobility features, audio, web & video conferencing, fixed-mobile convergence (FMC), desktop sharing, data sharing, call control and speech recognition with non-real-time communication services such as unified messaging.[29]
- version control
- The management of changes to documents, computer programs, large web sites, and other collections of information.[30]
- VNC
- A graphical desktop sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer.[31]
- VoIP
- A methodology and group of technologies for the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet.[32]
Assessments
[edit | edit source]- Flashcards: Quizlet: Internet Communications
- Quiz: Quizlet: Internet Communications
See Also
[edit | edit source]References
[edit | edit source]- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Wikipedia: Voice over IP
- ↑ Wikipedia: Voice over IP
- ↑ Wikipedia: Voice over IP
- ↑ Wikipedia: Voice over IP
- ↑ Wikipedia: File transfer
- ↑ Wikipedia: File Transfer Protocol
- ↑ Wikipedia: File Transfer Protocol
- ↑ Wikipedia: File Transfer Protocol
- ↑ Wikipedia: File Transfer Protocol
- ↑ Wikipedia: File Transfer Protocol
- ↑ Wikipedia: Peer-to-peer file sharing
- ↑ Wikipedia: Peer-to-peer file sharing
- ↑ Wikipedia: Peer-to-peer file sharing
- ↑ Wikipedia: Peer-to-peer file sharing
- ↑ Wikipedia: Peer-to-peer file sharing
- ↑ Wikipedia: Peer-to-peer file sharing
- ↑ Wikipedia: Remote desktop
- ↑ Wikipedia: Remote desktop
- ↑ Wikipedia: Remote desktop
- ↑ Wikipedia: Application sharing
- ↑ Wikipedia: Collaborative software
- ↑ Wikipedia: Technological convergence
- ↑ Wikipedia: File Transfer Protocol
- ↑ Wikipedia: Remote access
- ↑ Wikipedia: Remote desktop software
- ↑ Wikipedia: Remote Desktop Protocol
- ↑ Wikipedia: Unified communications
- ↑ Wikipedia: Version control
- ↑ Wikipedia: Virtual Network Computing
- ↑ Wikipedia: Voice over IP
Lesson 7 - Networking
[edit | edit source]

This lesson introduces networking fundamentals, including network devices, Internet protocols, and name resolution.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[1][2]
- Identify the infrastructure required to access the Internet, including hardware and software components.
- Define important Internet communications protocols and their roles in delivering basic Internet services.
- Identify the basic principles of the Domain Name System (DNS).
Readings
[edit | edit source]- Wikipedia: Computer network
- Wikipedia: Internet protocol suite
- Wikipedia: Domain Name System
- Just Added: Wikibooks: Introduction to Computer Information Systems/Computer Networks
Multimedia
[edit | edit source]- YouTube: Computer Networks - Crash Course
- YouTube: The Internet: IP Addresses and DNS
- YouTube: The Internet: Packets, Routing and Reliability
- YouTube: How does the INTERNET work?
- YouTube: DNS Explained
- YouTube: The OSI Model Demystified
- YouTube: IT Fundamentals - Basic Networking Devices
- YouTube: Introduction to Computer Networks Part 1 - Easy to understand basics
- YouTube: Introduction to Computer Networks Part 2 - Easy to understand basics
- YouTube: Introduction to Computer Networks Part 3 - Easy to understand basics
- YouTube: Installing a SOHO Network
Activities
[edit | edit source]- Complete the following tutorials:
- Review IP address settings for your local network:
- Windows:
- Review Microsoft: How do I fix network adapter problems? and Microsoft: Change TCP/IP Settings. Review network settings for your system.
- Review ipconfig. Complete the activities to display IP address information, all information, and release and renew a dynamic IP address.
- macOS:
- Review Apple: About Network Utility. Use Network Utility to review network settings for your system.
- Review MacWorld: Configuring Your Mac's Network Settings Use System Preferences / Network to review network settings for your system. Use the Advanced button and TCP/IP settings to renew your DHCP lease.
- Review Wikipedia: ifconfig. Use
ifconfigto review network settings for your system.
- Linux:
- Review YoLinux: Network GUI Configuration Tools. Use Network Configuration or System Settings / Networking to review network settings for your system.
- Review Wikipedia: ifconfig. Use
ifconfigto review network settings for your system. Review CyberCiti: Linux Force DHCP Client to Renew IP Address. Usedhclientto release and renew a dynamic IP address.
- Windows:
- Verify Internet connectivity:
- Verify a physical connection:
- Wired: Check for connectivity lights on the network adapter and switch or router.
- Wireless: Check for connectivity through the user interface.
- Verify ip address settings.
- Windows: Use
ipconfig. - macOS: Use Network Utility, System Preferences / Network, or
ifconfig. - Linux: Use Network Configuration, System Settings / Networking, or
ifconfig.
- Windows: Use
- Review Ping/Host. Verify local and remote connectivity using
ping.- Ping your local IP address.
- Ping your local default gateway address.
- Ping an Internet host such as 8.8.8.8.
- Review Tracert. Trace the route to an Internet host such as 8.8.8.8.
- Use https://traceroute-online.com/ to visually trace the route to en.wikiversity.org or another host.
- Review Nslookup. Verify name resolution using
nslookupand an Internet host name, such as en.wikiversity.org.
- Verify a physical connection:
- Share a folder and connect to the shared folder:
- Windows GUI:
- Review Microsoft: File Sharing Essentials. Share a folder on your system.
- From another computer, use a UNC path to connect to the shared folder.
- Windows CLI:
- Review Microsoft: Net Share. Use the
net sharecommand to share a folder on your system. - Review Microsoft: Net Use. From another computer, use the
net usecommand to connect to the shared folder.
- Review Microsoft: Net Share. Use the
- macOS:
- Review Apple: Mac Basics: File Sharing. Share a folder on your system.
- Review Apple: Connect to Shared Computers and File Servers on a Network. From another computer, connect to the shared folder.
- Linux:
- Review TechGage: Using Samba to Share Your Linux Folders. Install Samba if necessary and share a folder on your system.
- Review HowToGeek: 3 Easy Ways to Connect to Windows Shared Folders from Linux. From another computer, connect to the shared folder.
- Windows GUI:
- Research and compare license and support costs for Windows, macOS, and Linux.
- Research plans available from different wired (cable, DSL) and wireless (cellular, wireless, satellite) Internet providers. Compare mobility, availability, bandwidth, reliability, delay, concurrent connections, security, and cost.
- Research, identify and describe the necessary components required to set-up a home network for yourself.
Lesson Summary
[edit | edit source]- A computer network or data network is a digital telecommunications network that allows computers to exchange data. Networked computing devices pass data to each other in the form of packets across connections established using either cable or wireless media.[3]
- A network packet is a formatted unit of data sent through a network to the destination. Once packets arrive, they are reassembled into their original message.[4]
- Wired media includes coaxial cable, twisted-pair cable, and optical fiber.[5]
- Wireless local area network connections use spread spectrum technology based on a common flavor of open-standards wireless radio-wave technology defined as IEEE 802.11 and known as Wi-Fi.[6]
- A network interface controller (NIC) is hardware that provides a computer with the ability to access the transmission media, and has the ability to process low-level network information.[7]
- In Ethernet networks, each NIC has a unique 48-bit Media Access Control (MAC) address.[8]
- A repeater or hub is an electronic device that receives a network signal in the form of bits, cleans it of unnecessary noise, and regenerates it. In local area networks, switches have replaced hubs.[9]
- A bridge or switch is a device that connects and filters multiple network segments or devices, by forwarding data only to one or multiple devices that need to receive the data based on destination MAC address.[10]
- A router is a device that forwards data packets between different computer networks based on network address (IP address).[11]
- A modem is a device used to connect network nodes via wire not originally designed for digital network traffic, by modulating the digital signal to produce an analog signal for transmission.[12]
- A firewall is a device used to control network security and access rules by rejecting access requests from unrecognized sources while allowing actions from recognized ones.[13]
- Network topology is the layout or organizational hierarchy of interconnected nodes of a computer network. Common topologies include bus, star, ring, and mesh.[14]
- A communications protocol is a set of rules for exchanging information over a network. In a protocol stack, each protocol leverages the services of the protocol below it.[15]
- An important example of a protocol stack is HTTP (the World Wide Web protocol) running over TCP over IP (the Internet protocols) over IEEE 802.11 (the Wi-Fi protocol).[16]
- Participants in the Internet use a diverse array of methods of several hundred documented, and often standardized, protocols compatible with the Internet Protocol Suite and an addressing system (IP addresses) administered by the Internet Assigned Numbers Authority and address registries.[17]
- A network can be characterized by its physical capacity or its organizational purpose. These include personal area network (PAN), local area network (LAN), and wide area network (WAN).[18]
- A virtual private network (VPN) is an overlay network in which some of the links between nodes are carried by open connections or virtual circuits in some larger network instead of by physical wires.[19]
- An intranet is a set of networks that are under the control of a single administrative entity.[20]
- An extranet is a network that is under the administrative control of a single organization, but supports a limited connection to a specific external network.[21]
- Routing is the process of selecting network paths to carry network traffic.[22]
- Network services are applications hosted by servers on a computer network, to provide some functionality for members or users of the network, or to help the network itself to operate.[23]
- Network security consists of provisions and policies adopted by the network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of the computer network and its network-accessible resources.[24]
- The Internet protocol suite is the set of communications protocols used for the Internet and similar networks.[25]
- The Internet protocol suite is a four-layer model containing Link, Internet, Transport, and Application layers.[26]
- The Internet protocol suite is maintained by the Internet Engineering Task Force (IETF).[27]
- The Link layer contains communication technologies for a local network.[28]
- The Internet layer connects local networks, thus establishing internetworking.[29]
- The Transport layer handles host-to-host communication.[30]
- The Application layer contains all protocols for specific data communications services on a process-to-process level.[31]
- The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network.[32]
- The Domain Name System translates more readily memorized domain names to the numerical IP addresses needed for locating and identifying computer services and devices with the underlying network protocols.[33]
- The Domain Name System delegates the responsibility of assigning domain names and mapping those names to Internet resources by designating authoritative name servers for each domain. Network administrators may delegate authority over sub-domains of their allocated name space to other name servers.[34]
- The domain name space consists of a tree data structure. Each node or leaf in the tree has a label and zero or more resource records (RR), which hold information associated with the domain name.[35]
- The domain name itself consists of the label, possibly concatenated with the name of its parent node on the right, separated by a dot.[36]
- The domain name tree sub-divides into zones beginning at the root zone. The right-most label conveys the top-level domain.[37]
Key Terms
[edit | edit source]- 4G
- The fourth generation of mobile telecommunications technology.[38]
- address
- A numerical designation that uniquely refers to a specific communication entity.[39]
- backbone
- A part of computer network that interconnects various pieces of network, providing a path for the exchange of information between different LANs or subnetworks.[40]
- bandwidth
- The bit-rate of available or consumed information capacity expressed typically in metric multiples of bits per second.[41]
- client
- A piece of computer hardware or software that accesses a service made available by a server.[42]
- DARPA
- An agency of the U.S. Department of Defense responsible for the development of emerging technologies for use by the military.[43]
- domain name
- An identification string that defines a realm of administrative autonomy, authority or control within the Internet.[44]
- DSL (Digital Subscriber Line)
- A family of technologies that are used to transmit digital data over telephone lines.[45]
- frame
- A digital data transmission unit in computer networking and telecommunication.[46]
- FQDN (Fully Qualified Domain Name)
- A domain name that specifies its exact location in the tree hierarchy of the Domain Name System (DNS).[47]
- gateway
- A piece of networking hardware equipped for interfacing with another network that uses different protocols.[48]
- host
- A computer or other device connected to a computer network.[49]
- IANA (Internet Assigned Numbers Authority)
- A department of ICANN, a nonprofit private American corporation that oversees global IP address allocation, autonomous system number allocation, root zone management in the Domain Name System, media types, and other Internet Protocol-related symbols and Internet numbers.[50]
- IP (Internet Protocol)
- The principal communications protocol in the Internet protocol suite for relaying datagrams across network boundaries.[51]
- ISP (Internet Service Provider)
- An organization that provides services accessing and using the Internet.[52]
- packet
- A formatted unit of data carried by a packet-switched network.[53]
- protocol
- A system of rules that allow two or more entities of a communications system to transmit information via any kind of variation of a physical quantity.[54]
- proxy server
- A server that acts as an intermediary for requests from clients seeking resources from other servers.[55]
- server
- A computer program or a device that provides functionality for other programs or devices.[56]
- TCP (Transmission Control Protocol)
- One of the main protocols of the Internet protocol suite; It provides reliable, ordered, and error-checked delivery of a stream of bytes between applications running on hosts communicating by an IP network.[57]
- TLD (Top-Level Domain)
- One of the domains at the highest level in the hierarchical Domain Name System of the Internet.[58]
- throughput
- The rate of successful message delivery over a communication channel.[59]
- wireless access point
- A networking hardware device that allows a Wi-Fi device to connect to a wired network.[60]
Assessments
[edit | edit source]- Crossword Puzzle: Crossword Basic Networking Terms
See Also
[edit | edit source]References
[edit | edit source]- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Computer network
- ↑ Wikipedia: Internet protocol suite
- ↑ Wikipedia: Internet protocol suite
- ↑ Wikipedia: Internet protocol suite
- ↑ Wikipedia: Internet protocol suite
- ↑ Wikipedia: Internet protocol suite
- ↑ Wikipedia: Internet protocol suite
- ↑ Wikipedia: Internet protocol suite
- ↑ Wikipedia: Domain Name System
- ↑ Wikipedia: Domain Name System
- ↑ Wikipedia: Domain Name System
- ↑ Wikipedia: Domain Name System
- ↑ Wikipedia: Domain Name System
- ↑ Wikipedia: Domain Name System
- ↑ Wikipedia: 4G
- ↑ Live action: Glossary of Network Terms
- ↑ Wikipedia: Backbone network
- ↑ Wikipedia: Bandwidth (computing)
- ↑ Wikipedia: Client (computing)
- ↑ Wikipedia: DARPA
- ↑ Wikipedia: Domain name
- ↑ Wikipedia: Digital subscriber line
- ↑ Wikipedia: Frame (networking)
- ↑ Wikipedia: Fully qualified domain name
- ↑ Wikipedia: Gateway (telecommunications)
- ↑ Wikipedia: Host (network)
- ↑ Wikipedia: Internet Assigned Numbers Authority
- ↑ Wikipedia: Internet Protocol
- ↑ Wikipedia: Internet service provider
- ↑ Wikipedia: Network packet
- ↑ Wikipedia: Communications protocol
- ↑ Wikipedia: Proxy server
- ↑ Wikipedia: Server (computing)
- ↑ Wikipedia: Transmission Control Protocol
- ↑ Wikipedia: Top-level domain
- ↑ Wikipedia: Throughput
- ↑ Wikipedia: Wireless access point
Lesson 8 - Security
[edit | edit source]

This lesson introduces Internet security, including browser and browsing security, personally identifiable information, and related ethical and legal issues.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[1][2]
- Identify security issues related to Internet clients (e.g., Web browsers, e-mail, instant messaging) in the workplace, including certificates, malware, illicit servers, viruses.
- Identify and use principles of Personal Information Management (PIM), including common applications.
- Identify security-related ethical and legal issues faced by IT professionals.
Readings
[edit | edit source]- Wikipedia: Internet security
- Wikipedia: Personally identifiable information
- Wikibooks: Ethics for IT Professionals/Professional Code of Ethics
Multimedia
[edit | edit source]- YouTube: The Internet: Encryption & Public Keys
- YouTube: Symmetric Key and Public Key Encryption
- YouTube: The Internet: Cybersecurity & Crime
- YouTube: Cybersecurity 101
Student Presentations
[edit | edit source]Activities
[edit | edit source]- Complete the following tutorials:
- Practice web browser safety.
- Review browser options:
- Chrome: Google: Choose Your Privacy Settings.
- Firefox: Mozilla: Privacy and Security Settings.
- Internet Explorer: Microsoft: Change Security and Privacy Settings for Internet Explorer.
- Opera: Opera: Guide to security and privacy
- Safari: Apple: Manage Cookies and Other Website Data.
- Check your browser's version to ensure the browser is up to date.
- Check add-ons to ensure they are up to date.
- Disable unneeded add-ons.
- Clear the browser cache. Identify how to clear browser history and cookies.
- Check autoform settings and remove any personal information you do not want saved.
- Visit a secure website, such as https://en.wikiversity.org and view certificate information for that website.
- Use private / incognito browsing to visit a website that normally remembers you. Notice how you are unknown to the website when using private browsing.
- Review browser options:
- Use anti-malware software to scan your system and test malware detection.
- All: Review Wikipedia: Comparison of antivirus software. Download a free, well-known anti-malware application and scan your system.
- All: Review Wikipedia: EICAR test file. Download and save the EICAR test file to test your anti-malware application and follow the process for removing malware.
- Research password managers and multi-factor authentication. Consider setting up a password manager and using multi-factor authentication on your Apple, Facebook, Google, and/or Microsoft accounts, as well as your password manager and your financial institutions.
- Test your firewall using a testing service such as Gibson Research: ShieldsUP!
Lesson Summary
[edit | edit source]- Internet security is a branch of computer security specifically related to the Internet, often involving browser security but also network security on a more general level, as it applies to other applications or operating systems as a whole. Its objective is to establish rules and measures to use against attacks over the Internet.[3]
- The Internet represents an insecure channel for exchanging information leading to a high risk of intrusion or fraud, such as phishing, online viruses, trojans, worms, and more.[4]
- A computer user can be tricked or forced into downloading software onto a computer that is of malicious intent. Such software comes in many forms, such as viruses, Trojan horses, spyware, and worms.[5]
- Malware, short for malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. Malware is defined by its malicious intent, acting against the requirements of the computer user, and does not include software that causes unintentional harm due to some deficiency. The term badware is sometimes used, and applied to both true (malicious) malware and unintentionally harmful software.[6]
- A botnet is a network of zombie computers that have been taken over by a robot or bot that performs large-scale malicious acts for the creator of the botnet.[7]
- Computer Viruses are programs that can replicate their structures or effects by infecting other files or structures on a computer. The common use of a virus is to take over a computer to steal data.[8]
- Computer worms are programs that can replicate themselves throughout a computer network, performing malicious tasks throughout.[9]
- Ransomware is a type of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator(s) of the malware in order for the restriction to be removed.[10]
- Scareware is scam software with malicious payloads, usually of limited or no benefit, that are sold to consumers via certain unethical marketing practices. The selling approach uses social engineering to cause shock, anxiety, or the perception of a threat, generally directed at an unsuspecting user.[11]
- Spyware refers to programs that surreptitiously monitor activity on a computer system and report that information to others without the user's consent.[12]
- A Trojan horse, commonly known as a Trojan, is a general term for malicious software that pretends to be harmless, so that a user willingly allows it to be downloaded onto the computer.[13]
- KeyLogger, Keystroke logging, often referred to as keylogging or keyboard capturing, is the action of recording (logging) the keys struck on a keyboard.[14]
- A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer resource unavailable to its intended users.[15]
- Phishing occurs when the attacker pretends to be a trustworthy entity, either via email or web page.[16]
- TCP/IP protocols may be secured with cryptographic methods and security protocols. These protocols include Secure Sockets Layer (SSL), succeeded by Transport Layer Security (TLS) for web traffic, Pretty Good Privacy (PGP) for email, and IPsec for the network layer security.[17]
- Multi-factor authentication (MFA) is a method of computer access control in which a user is granted access only after successfully presenting several separate pieces of evidence to an authentication mechanism – typically at least two of the following categories: knowledge (something they know), possession (something they have), and inherence (something they are).[18]
- A computer firewall controls access between networks and generally consists of gateways and filters which vary from one firewall to another. Firewalls also screen network traffic and are able to block traffic that is dangerous.[19]
- Antivirus software and Internet security programs can protect a programmable device from attack by detecting and eliminating viruses.[20]
- A password manager is a software application that helps a user store and organize passwords.[21]
- Personally identifiable information (PII), or sensitive personal information (SPI), is information that can be used on its own or with other information to identify, contact, or locate a single person, or to identify an individual in context.[22]
- Ethical codes are adopted by organizations to assist members in understanding the difference between 'right' and 'wrong' and in applying that understanding to their decisions.[23]
- An ethical code generally implies documents at three levels: codes of business ethics, codes of conduct for employees, and codes of professional practice.[24]
Key Terms
[edit | edit source]- antivirus software
- Computer software used to prevent, detect, and remove malicious software.[25]
- asymmetric encryption
- A cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner.[26]
- authentication
- The act of confirming identity.[27]
- decryption
- The process of converting unintelligible ciphertext back to plaintext.[28]
- digital certificate
- An electronic document used to prove the ownership of a public key.[29]
- digital signature
- A mathematical scheme for demonstrating the authenticity of digital messages or documents.[30]
- encryption
- The process of converting plaintext into unintelligible ciphertext.[31]
- hash function
- Any function that allows one to easily verify that some input data maps to a given hash value, but if the input data is unknown, it is deliberately difficult to reconstruct it by knowing the stored hash value.[32]
- IPsec
- A network protocol suite that authenticates and encrypts the packets of data sent over a network.[33]
- malware (malicious software)
- Hostile or intrusive software, including computer viruses, worms, Trojan horses, ransomware, spyware, adware, scareware, and other malicious programs.[34]
- patch
- Software designed to update a computer program.[35]
- personally identifiable information (PII)
- Information that can be used to identify an individual in context.[36]
- phishing
- The attempt to obtain sensitive information such as usernames, passwords, and credit card details (and, indirectly, money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication.[37]
- ransomware
- Malware that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid.[38]
- right to be forgotten
- The right of an individual to have certain information deleted so that others can no longer trace them.[39]
- spyware
- Software that aims to gather information about a person or organization without their knowledge.[40]
- SSL/TLS
- Cryptographic protocols that provide communications security over a computer network.[41]
- symmetric encryption
- Algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext.[42]
- Trojan
- Any malicious computer program which misleads users of its true intent.[43]
- virus
- Malware that, when executed, replicates itself by modifying other computer programs and inserting its own code.[44]
- worm
- Standalone malware that replicates itself in order to spread to other computers.[45]
Assessments
[edit | edit source]- Flashcards: Quizlet: CIW IBA Lesson 8
- Flashcards: Quizlet: CIW IBA Lesson 8 Vocabulary
- Quiz: Quizlet: CIW IBA Lesson 8
- Quiz: Quizlet: CIW IBA Lesson 8 Vocabulary
See Also
[edit | edit source]- IT Fundamentals/Security
- Wikibooks: Introduction to Computer Information Systems/Security
- StaySafeOnline: Online Safety Basics
- US-CERT: Avoiding Social Engineering and Phishing Attacks
- CISA: Cyber Games
References
[edit | edit source]- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Internet security
- ↑ Wikipedia: Personally identifiable information
- ↑ Wikipedia: Ethical code
- ↑ Wikipedia: Ethical code
- ↑ Wikipedia: Antivirus software
- ↑ Wikipedia: Asymmetric encryption
- ↑ Wikipedia: Authentication
- ↑ Wikipedia: Cryptography
- ↑ Wikipedia: Digital certificate
- ↑ Wikipedia: Digital signature
- ↑ Wikipedia: Cryptography
- ↑ Wikipedia: Hash function
- ↑ Wikipedia: IPsec
- ↑ Wikipedia: Malware
- ↑ Wikipedia: Patch (computing)
- ↑ Wikipedia: Personally identifiable information
- ↑ Wikipedia: Phishing
- ↑ Wikipedia: Ransomware
- ↑ Wikipedia: Right to be forgotten
- ↑ Wikipedia: Spyware
- ↑ Wikipedia: Transport Layer Security
- ↑ Wikipedia: Symmetric encryption
- ↑ Wikipedia: Trojan horse (computing)
- ↑ Wikipedia: Computer virus
- ↑ Wikipedia: Computer worm
Lesson 9 - HTML
[edit | edit source]
Hypertext Markup Language (HTML) is the standard markup language for creating web pages and web applications.[1] This lesson introduces HTML.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[2]
- Understand basic HTML page structure.
- Create simple web pages.
- Review the requirements
- Review the requirements of the document
- Select the appropriate markup language, based on organizational standards
- Review the document structure
- Create the document structure
- Create and assign, the basic elements of the document
- Mark-up sections of the document to depict the structure
- Validate the documents
- Validate the markup of the language document, against the requirements
- Validate the markup of the language document, in different browsers
Readings
[edit | edit source]Multimedia
[edit | edit source]Student Presentations
[edit | edit source]- YouTube: How to Link Bitbucket to Visual Studio Code (Using GIT)
- YouTube: How to Use a Online HTML Editor
- YouTube: HTML Basics
- YouTube: How to Create a Simple HTML page
- YouTube: HTML Tags to Create a Website
- YouTube: Internet Fundamentals: Getting Started with HTML
- YouTube: Installing Visual Studio Code and Essential Plugins
Activities
[edit | edit source]- Complete one or more of the following tutorials:
- Create a simple web page.
- Review ShayHowe: Building Your First Web Page.
- Use HTML Online: Editor to create a simple web page about your favorite hobby.
- Include an
<img>tag to add one or more free images from Wikimedia Commons to your page.
- Validate your web page.
- Review W3C: Validating your HTML.
- Use the W3C: Validator to validate your web page. Make any necessary corrections to pass the validation test.
- Research free web hosting services. Select a free hosting service and add your new web page to the web server. Access the web page using a web browser to confirm that it displays correctly. See Bitbucket/Website Hosting for a free source code control and HTML/CSS/JavaScript hosting option.
- Research free HTML editors. Consider downloading and installing an HTML editor.
Lesson Summary
[edit | edit source]- Hypertext Markup Language (HTML) is the standard markup language for creating web pages and web applications.[3]
- Web browsers receive HTML documents from a web server or from local storage and render them into multimedia web pages.[4]
- HTML describes the structure of a web page semantically and originally included cues for the appearance of the document.[5]
- HTML elements are the building blocks of HTML pages.[6]
- With HTML constructs, images and other objects, such as interactive forms, may be embedded into the rendered page.[7]
- HTML provides a means to create structured documents by denoting structural semantics for text such as headings, paragraphs, lists, links, quotes and other items.[8]
- HTML elements are delineated by tags, written using angle brackets. Browsers do not display the HTML tags, but use them to interpret the content of the page.[9]
- HTML can embed programs written in a scripting language such as JavaScript which affect the behavior and content of web pages.[10]
- Inclusion of CSS defines the look and layout of content.[11]
- The World Wide Web Consortium (W3C), maintainer of both the HTML and the CSS standards, has encouraged the use of CSS over explicit presentational HTML since 1997.[12]
- The current HTML standard is HTML5, completed and standardized on 28 October 2014.[13]
- HTML markup consists of several key components, including those called tags (and their attributes), character-based data types, character references and entity references.[14]
- HTML tags most commonly come in pairs, although some represent empty elements and so are unpaired. The first tag in such a pair is the start tag, and the second is the end tag. They may also be called opening tags and closing tags.[15]
- The general form of an HTML element is
<tag attribute1="value1" attribute2="value2">content</tag>.[16] - Some HTML elements are defined as empty elements and take the form
<tag attribute1="value1" attribute2="value2">.[17] - If attributes are not mentioned, default values are used in each case.[18]
- A typical HTML document includes:[19]
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <title>Title</title> </head> <body> <p>Hello world!</p> </body> </html>
- The HTML document type declaration,
DOCTYPE, triggers standards mode rendering.[20] <html>and</html>tags describe the web page.[21]<head>and</head>tags describe page metadata.[22]meta charsetdescribes page character encoding. The default encoding for HTML5 is UTF-8.[23]<title>and</title>tags describe the page title.[24]<body>and</body>tags describe the visible page content.[25]<p>and</p>tags describe paragraphs.[26]<a>and</a>tags describe anchors (hyperlinks).[27]<br>tags describe line breaks.[28]<h1>and</h1>and similar tags describe content headings.[29]<img>tags describe images.[30]<!--and-->enclose comments.[31]- Special characters may be entered using
&code;syntax. Examples include:[32]- & -
& - < -
< - > -
>
- & -
- Semantic HTML is a way of writing HTML that emphasizes the meaning of the encoded information over its presentation (look).[33]
- Presentational markup tags are deprecated in current HTML in favor of using CSS to describe content presentation.[34]
Key Terms
[edit | edit source]- attribute
- A modifier of an HTML element type.[35]
- element
- An individual component of an HTML document or web page.[36]
- HTML (Hypertext Markup Language)
- The standard markup language for creating web pages and web applications.[37]
- HTML tags
- Are the hidden keywords within a web page that define how your web browser must format and display the content.[38]
- HTTP (Hypertext Transfer Protocol)
- An application protocol for distributed, collaborative, and hypermedia information systems.[39]
- markup language
- A system for annotating a document in a way that is syntactically distinguishable from the text.[40]
- metadata
- Is used by browsers (how to display content or reload page), search engines (keywords), and other web services.[41]
- SGML (Standard Generalized Markup Language)
- A standard for defining generalized markup languages for documents.[42]
- W3C (World Wide Web Consortium)
- The main international standards organization for the World Wide Web.[43]
- WYSIWYG (What You See Is What You Get)
- A system in which content (text and graphics) can be edited in a form closely resembling its appearance when printed or displayed as a finished product.[44]
Assessments
[edit | edit source]- Flashcards: Quizlet: HTML
- Quiz: Quizlet: HTML
See Also
[edit | edit source]- HTML
- Web Foundations
- Training.gov.au: Create a simple markup language document
- ShayHowe: Building Your First Web Page
- Saylor: HTML and CSS for Beginners
- PHP-T-POINT: HTML Tutorial
References
[edit | edit source]- ↑ Wikipedia: HTML
- ↑ Training.gov.au: ICTWEB301 - Create a simple markup language document
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ W3Schools: HTML Charset
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML attribute
- ↑ Wikipedia: HTML element
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML tags
- ↑ Wikipedia: Hypertext Transfer Protocol
- ↑ Wikipedia: Markup language
- ↑ Wikipedia: Metadata in HTML
- ↑ Wikipedia: Standard Generalized Markup Language
- ↑ Wikipedia: World Wide Web Consortium
- ↑ Wikipedia: WYSIWYG
Lesson 10 - CSS
[edit | edit source]
Cascading Style Sheets (CSS) is a style sheet language used for describing the presentation of a document written in a markup language. Along with HTML and JavaScript, CSS is a cornerstone technology used by most websites to create visually engaging webpages, user interfaces for web applications, and user interfaces for many mobile applications.[1] This lesson introduces CSS.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[2]
- Understand how to link cascading style sheets.
- Create and use simple CSS pages.
- Format, style and lay out the elements on a web page
- Obtain user requirements
- Style the elements of a web page using CSS
- Apply CSS to multiple pages in a website
- Position the document elements using CSS
- Test and validate the web pages
- Test the website in various browsers
- Validate CSS against industry standards
- Report the test results to the appropriate person
Readings
[edit | edit source]Multimedia
[edit | edit source]Student Presentations
[edit | edit source]Activities
[edit | edit source]- Complete one or more of the following tutorials:
- Create and use inline CSS.
- Review W3Schools: HTML CSS.
- Use inline CSS to format one or more elements of your web page. Consider including
color,background-color,text-align,font-size, andfont-family. - Use the W3C: Validator to validate your web page. Make any necessary corrections to pass the validation test.
- Create and use internal CSS.
- Review W3Schools: HTML CSS.
- Use internal CSS to format one or more elements of your web page. Consider including
color,background-color,text-align,font-size, andfont-family. - Use the W3C: Validator to validate your web page. Make any necessary corrections to pass the validation test.
- Create and use external CSS.
- Review W3Schools: HTML CSS.
- Use external CSS to position and format one or more elements of your web page. Consider including
color,background-color,text-align,font-size, andfont-family, as well asfloat,width,margin,padding, and / orborder. - Use the W3C: CSS Validator to validate your external style sheet. Make any necessary corrections to pass the validation test.
Lesson Summary
[edit | edit source]- Cascading Style Sheets (CSS) is a style sheet language used for describing the presentation of a document written in a markup language.[3]
- CSS is designed primarily to enable the separation of presentation and content, including aspects such as the layout, colors, and fonts.[4]
- CSS benefits include:[5]
- Improve content accessibility
- Provide more flexibility and control in the specification of presentation characteristics
- Enable multiple HTML pages to share common formatting
- Reduce complexity and repetition in the structural content
- Present the same markup page in different styles for different rendering methods
- Display the web page differently depending on the screen size or viewing device
- The CSS specification describes a priority scheme to determine which style rules apply if more than one rule matches against a particular element.[6]
- The CSS specifications are maintained by the World Wide Web Consortium (W3C).[7]
- A style sheet consists of a list of rules. Each rule or rule-set consists of one or more selectors, and a declaration block.[8]
- Selectors declare which part of the markup a style applies to by matching tags and attributes in the markup itself.[9]
- Classes and IDs are case-sensitive, start with letters, and can include alphanumeric characters and underscores. A class may apply to any number of instances of any elements. An ID may only be applied to a single element.[10]
- A declaration block consists of a list of declarations in braces. Each declaration itself consists of a property, a colon (:), and a value. If there are multiple declarations in a block, a semi-colon (;) must be inserted to separate each declaration.[11]
- Values may be keywords or numerical values.[12]
- CSS may be specified inline, internal, or external.[13]
- Inline CSS has the format:[14]
<element style="property: value;">content</element>
- Internal CSS has the format:[15]
<head> <style> selector {property: value;} </style> </head>
- External CSS is specified using a link element:[16]
<head> <link href="path/to/file.css" rel="stylesheet" type="text/css"> </head>
- External CSS files have the format:[17]
selector {property: value;}which may also be written as:
selector { property: value; }or
selector { property: value; }
- Whitespace between properties and selectors is ignored.[18]
- Comments may be placed wherever white space is allowed within a style sheet.[19]
/* Comment */
Key Terms
[edit | edit source]- class
- An identifier that can annotate multiple elements in a document.[20]
- declaration
- Consists of a property, a colon (:), and a value, separated by a trailing semi-colon (;).[21]
- Font-Family
- The font-family property sets the font of an HTML element’s text.[22]
- id
- A unique identifier within the document.[23]
- ID Selectors
- ID selectors are used to select only a single item on a page. Like the term (“identification”) indicates, ID selectors will ONLY select the first element with a matching ID.[24]
- inherit
- Copies the value of the property in effect for the element’s parent.[25]
- initial
- Represents the initial (or default) value for the property, over-riding any values set earlier in the cascade; initial values are defined on each property’s definition; it is not supported in Internet Explorer.[26]
- margin
- The margin is the space around the element. The larger the margin, the more space between our element and the elements around it. We can adjust the margin to move our HTML elements closer to or farther from each other. Here, the div with id ‘box’ will get 10px of margin above and below it, and 5px of margin to the left and right.[27]
- padding
- The padding is the spacing between the content and the border (edge of the element.). We can adjust this value with CSS to move the border closer to or farther from the content. Here, the div with id ‘box’ will get 10px of padding all around it.[28]
- property
- Consists of a name specified in the CSS standard.[29]
- rule
- Consists of one or more selectors, and a declaration block.[30]
- selector
- declares which part of the markup a style applies to by matching tags and attributes in the markup itself.[31]
- unset
- is equivalent to inherit if the property is normally inherited, or initial otherwise; it is not currently supported in most browsers (although Firefox implements it).[32]
- value
- Consists of a keyword or numerical value.[33]
Assessments
[edit | edit source]- Flashcards: Quizlet: CSS
- Quiz: Quizlet: CSS
See Also
[edit | edit source]- CSS
- Web Foundations
- W3C: Styles
- Wordpress: Inline vs Internal vs External CSS
- Saylor: HTML and CSS for Beginners
References
[edit | edit source]- ↑ Wikipedia: Cascading Style Sheets
- ↑ Training.gov.au: ICTWEB409 - Develop cascading style sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Mozilla: CSS Comments
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
- ↑ Wikipedia: Cascading Style Sheets
Lesson 11 - Graphics and Multimedia
[edit | edit source]




Computer graphics are pictures and films created using computers.[1] Multimedia is content that uses a combination of different content forms such as text, audio, images, animations, video and interactive content.[2] This lesson introduces computer graphics, including raster and vector graphics, and web multimedia audio and video content.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[3][4][5]
- Understand how to add existing graphics and multimedia to web pages.
- Create and use simple graphic images and multimedia files.
- Determine the client requirements
- Access and interpret the client brief to determine client needs
- Analyse client needs with regard to image content, quality and size
- Source the images
- Research the appropriate sources of images, to meet a range of needs
- Source the images appropriate to meet the needs, taking into consideration copyright restrictions
- Manipulate the images
- Select the appropriate industry-standard, image-editing software for the purpose
- Create backups of the assets to be used
- Use features of the image-editing software, to create a range of effects appropriate to client needs and web application
- Edit, resize, and slice images for use in web applications, as required to meet client needs
- Save the images
- Save the images, maintaining their individual effects
- Save the images in formats appropriate for use in web applications, and to client needs
- Save the images in the appropriate directory structure
- Demonstrate ways to communicate effectively using Internet technology.
- Conduct a Webcast and related services.
- Represent technical issues to a non-technical audience.
Readings
[edit | edit source]- Wikipedia: Computer graphics
- Wikipedia: Raster graphics
- Wikipedia: Vector graphics
- Wikipedia: Multimedia
- Wikipedia: Streaming media
- Wikipedia: Screencast
- W3Schools.com: HTML iframe tag
- W3Schools.com: HTML YouTube Videos
- WebAim: Webaim Contrast Checker
Multimedia
[edit | edit source]- YouTube: Bitmap and Vector Graphics: What's the Difference?
- YouTube: PIXLR 101-1. Getting Started
- YouTube: Picozu Tutorial
- YouTube: How to Use GIMP (Beginners Guide)
- YouTube: Inkscape for Beginners: Infinite Loop Icon
- YouTube: Record Your Computer Screen With VLC
- YouTube: Make Videos with Your Phone
- YouTube: HTML5 Video Tag Introduction
- YouTube: HTML - Audio Player
Student Presentations
[edit | edit source]- YouTube: Graphics
- YouTube: Uploading Raster Graphics to Bitbucket using Insomnia
- YouTube: SVG Graphics
Activities
[edit | edit source]- Create and use raster graphics.
- Review Wikipedia: Raster graphics. Use a free, web-based image editor, such as Picozu: Image Editor or Pixlr: Editor, to create a new raster image.
- Review Wikipedia: GIMP. Download and install GIMP and use it to create a new raster image for your web page. See GIMP: Tutorials for tutorials.
- Review W3Schools: HTML img tag. Add a raster image to the web page you created in the previous lesson.
- Create and use vector graphics.
- Review Wikipedia: Vector graphics. Complete the Vectr.com: Vector graphics tutorial and create a new vector graphics image.
- Review Wikipedia: Inkscape. Download and install Inkscape and use it to create a new vector graphics image for your web page. See Inkscape: Tutorials for tutorials.
- Review W3Schools: HTML img tag. Add a vector graphics image to the web page you created in the previous lesson.
- Use multimedia.
- Complete the tutorial GCFLearnFree: YouTube.
- Review Wikipedia: VLC media player. Download and install VLC media player and use it to play multimedia video and audio files.
- Create multimedia.
- Review WikiHow: How to Screen Capture to File Using VLC or HowToGeek: How to Record Your Desktop to a File or Stream It over the Internet.
- Use VLC or another screen capture program to capture a video of your desktop as you demonstrate something you've learned in this course, or record a similar video using a computer webcam, tablet, or smart phone.
- Review Google: YouTube Help Center and upload your screencast or video to YouTube.
- Add multimedia to a web page.
- Review W3Schools: HTML YouTube Videos. Add your YouTube video to the web page you created in the previous lesson.
- Review W3Schools: HTML Multimedia and W3Schools: HTML5 Video. Add a video element to your web page.
- Review W3Schools: HTML5 Audio. Add an audio element to your web page.
Lesson Summary
[edit | edit source]- Computer graphics are pictures and films created using computers.[6]
- Computer graphic development has had a significant impact on many types of media and has revolutionized animation, movies, advertising, video games, and graphic design generally.[7]
- Computer animation is the art of creating moving images via the use of computers.[8]
- A raster graphics or bitmap image is a dot matrix data structure, representing a generally rectangular grid of pixels, or points of color, viewable via a monitor, paper, or other display medium.[9]
- Raster graphics are resolution dependent, meaning they cannot scale up to an arbitrary resolution without loss of apparent quality.[10]
- Vector graphics is the use of polygons to represent images in computer graphics.[11]
- Vector art is ideal for printing since the art is made from a series of mathematical curves, it will print very crisply even when resized.[12]
- Raster-based image editors, such as Painter, Photoshop, Paint.NET, MS Paint, and GIMP, revolve around editing pixels.[13]
- Vector-based image editors, such as Xfig, CorelDRAW, Adobe Illustrator, or Inkscape, revolve around editing lines and shapes (vectors).[14]
- The
<img>element is used to insert an image into an HTML page. Thesrcattribute specifies the image URL. The requiredaltattribute provides alternative text in case the image cannot be displayed.[15] - A typical
imgelement includes:[16]
<img src="example.jpg" alt="Alternate text that describes the image.">
- Multimedia is content that uses a combination of different content forms such as text, audio, images, animations, video and interactive content.[17]
- Multimedia can be recorded and played, displayed, interacted with or accessed by information content processing devices, such as computerized and electronic devices.[18]
- The term "rich media" is synonymous with interactive multimedia.[19]
- Digital online multimedia may be downloaded or streamed. Streaming multimedia may be live or on-demand.[20]
- Enhanced levels of interactivity are made possible by combining multiple forms of media content. Online multimedia is increasingly becoming object-oriented and data-driven, enabling applications with collaborative end-user innovation and personalization on multiple forms of content over time.[21]
- In addition to seeing and hearing, haptic technology enables virtual objects to be felt. Emerging technology involving illusions of taste and smell may also enhance the multimedia experience.[22]
- Multimedia may be broadly divided into linear and non-linear categories:[23]
- Linear active content progresses often without any navigational control for the viewer such as a cinema presentation
- Non-linear uses interactivity to control progress as with a video game or self-paced computer-based training. Hypermedia is an example of non-linear content.
- Multimedia presentations can be live or recorded:[24]
- A recorded presentation may allow interactivity via a navigation system
- A live multimedia presentation may allow interactivity via an interaction with the presenter or performer.
- Multimedia finds its application in various areas including, but not limited to, advertisements, art, education, entertainment, engineering, medicine, mathematics, business, scientific research and spatial temporal applications.[25]
- Streaming media is multimedia that is constantly received by and presented to an end-user while being delivered by a provider. A client end-user can use their media player to begin to play the data file (such as a digital file of a movie or song) before the entire file has been transmitted.[26]
- Live streaming refers to Internet content delivered in real-time, as events happen.[27]
- There are challenges with streaming content on the Internet. If the user does not have enough bandwidth in their Internet connection, they may experience stops in the content and some users may not be able to stream certain content due to not having compatible computer or software systems.[28]
- The
<audio>element represents a sound, or an audio stream.[29] - A typical
audioelement includes:[30]
<audio controls> <source src="example.mp4" type='audio/mp4' /> <source src="example.oga" type='audio/ogg; codecs=vorbis' /> <p>Your user agent does not support the HTML5 Audio element.</p> </audio>
- Supported
audiotypes include PCM (WAV), MP3, AAC (MP4, ADTS), Vorbis (Ogg, WebM), Opus (Ogg, WebM), and FLAC (FLAC, Ogg).[31] - The
<video>element plays videos.[32] - A typical
videoelement includes:[33]
<video poster="movie.jpg" controls> <source src="example.webm" type='video/webm; codecs="vp8.0, vorbis"'> <source src="example.ogv" type='video/ogg; codecs="theora, vorbis"'> <source src="example.mp4" type='video/mp4; codecs="avc1.4D401E, mp4a.40.2"'> <p>Your user agent does not support the HTML5 video tag.</p> </video>
- Supported
videotypes include MP4, Ogg, and WebM.[34]
Key Terms
[edit | edit source]- AIFF (Audio Interchange File Format)
- An audio file format standard developed by Apple and used for storing sound data for personal computers and other electronic audio devices.[35]
- AVI (Audio Video Interleave)
- A multimedia container format introduced by Microsoft as part of its Video for Windows software.[36]
- CGI (computer-generated imagery)
- The application of computer graphics to create or contribute to images in art, printed media, video games, films, television programs, shorts, commercials, videos, and simulators.[37]
- codec
- A device or computer program for encoding or decoding a digital data stream or signal.[38]
- GIF (Graphics Interchange Format)
- A raster graphics file format that uses lossless compression and supports interlacing and animation.[39]
- haptic technology
- Creates a sense of touch by applying forces, vibrations, or motions to the user.[40]
- JPEG
- A raster graphics file format that uses lossy compression.[41]
- lossless compression
- Data encoding methods that allow the original data to be perfectly reconstructed from the compressed data.[42]
- lossy compression
- Data encoding methods that use inexact approximations and partial data discarding to represent the content.[43]
- MIDI (Musical Instrument Digital Interface)
- A technical standard that describes a protocol, digital interface, and connectors and allows a wide variety of electronic musical instruments, computers and other related devices to connect and communicate with one another.[44]
- MOV (Quicktime Movie)
- A computer file format used natively by the Apple QuickTime multimedia framework.[45]
- MPEG (Moving Picture Experts Group)
- A working group of authorities that was formed by ISO and IEC to set standards for audio and video compression and transmission.[46]
- MP3 (MPEG-1 Audio Layer3)
- An audio coding format for digital audio developed by the Moving Picture Experts Group that uses a form of lossy data compression.[47]
- MP4 (MPEG-4 Part 14)
- A digital multimedia container format most commonly used to store video and audio, which allows streaming over the Internet.[48]
- OGG
- A free, open container format maintained by the Xiph.Org Foundation that is unrestricted by software patents and is designed to provide for efficient streaming and manipulation of high quality digital multimedia.[49]
- pixel (picture element)
- A single point in a raster image.[50]
- PNG (Portable Network Graphics)
- A raster graphics file format that uses lossless data compression and supports interlacing but not animation.[51]
- podcast
- An episodic series of digital audio files which a user can download and listen to.[52]
- screencast
- A digital recording of computer screen output, often containing audio narration.[53]
- streaming media
- Multimedia that is constantly received by and presented to an end-user while being delivered by a provider.[54]
- SVG (Scalable Vector Graphics)
- A vector graphics file format defined using XML text files.[55]
- TIFF (Tagged Image File Format)
- A raster graphics file format that uses lossless compression but does not support interlacing or animation.[56]
- WAV (Waveform)
- An audio file format standard developed by Microsoft and IBM for storing an audio bitstream on PCs.[57]
- webcast
- A media presentation distributed over the Internet using streaming media technology to distribute a single content source to many simultaneous listeners/viewers.[58]
Assessments
[edit | edit source]- Flashcards: Quizlet: Multimedia on the Web
- Quiz: Quizlet: Multimedia on the Web
See Also
[edit | edit source]- W3.org: Audio Element
- W3.org: Video Element
- Mozilla: Supported media formats
- Training.gov.au: ICTWEB303 - Produce digital images for the web
- Training.gov.au: ICTWEB412 - Produce interactive web animation
References
[edit | edit source]- ↑ Wikipedia: Computer graphics
- ↑ Wikipedia: Multimedia
- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Training.gov.au: ICTWEB303 - Produce digital images for the web
- ↑ Wikipedia: Computer graphics
- ↑ Wikipedia: Computer graphics
- ↑ Wikipedia: Computer graphics
- ↑ Wikipedia: Raster graphics
- ↑ Wikipedia: Raster graphics
- ↑ Wikipedia: Vector graphics
- ↑ Wikipedia: Vector graphics
- ↑ Wikipedia: Raster graphics
- ↑ Wikipedia: Raster graphics
- ↑ Wikipedia: HTML
- ↑ Wikipedia: HTML
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Multimedia
- ↑ Wikipedia: Streaming media
- ↑ Wikipedia: Streaming media
- ↑ Wikipedia: Streaming media
- ↑ Wikipedia: HTML5 Audio
- ↑ Wikipedia: HTML5 Audio
- ↑ Wikipedia: HTML5 Audio
- ↑ Wikipedia: HTML5 video
- ↑ Wikipedia: HTML5 video
- ↑ Mozilla: Supported media formats
- ↑ Wikipedia: Audio Interchange File Format
- ↑ Wikipedia: Audio Video Interleave
- ↑ Wikipedia: Computer-generated imagery
- ↑ Wikipedia: Codec
- ↑ Wikipedia: GIF
- ↑ Wikipedia: Haptic technology
- ↑ Wikipedia: JPEG
- ↑ Wikipedia: Lossless compression
- ↑ Wikipedia: Lossy compression
- ↑ Wikipedia: MIDI
- ↑ Wikipedia: QuickTime File Format
- ↑ Wikipedia: Moving Picture Experts Group
- ↑ Wikipedia: MP3
- ↑ Wikipedia: MPEG-4 Part 14
- ↑ Wikipedia: Ogg
- ↑ Wikipedia: Computer graphics
- ↑ Wikipedia: Portable Network Graphics
- ↑ Wikipedia: Podcast
- ↑ Wikipedia: Screencast
- ↑ Wikipedia: Streaming media
- ↑ Wikipedia: Scalable Vector Graphics
- ↑ Wikipedia: TIFF
- ↑ Wikipedia: WAV
- ↑ Wikipedia: Webcast
Lesson 12 - Web Accessibility
[edit | edit source]
Web accessibility is the inclusive practice of ensuring there are no barriers that prevent interaction with, or access to, websites on the World Wide Web by people with physical disabilities, situational disabilities, and socio-economic restrictions on bandwidth and speed. When sites are correctly designed, developed and edited, more users have equal access to information and functionality.[1]
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:
- Understand web accessibility standards
- Apply web accessibility standards to web pages
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: Introduction to Web Accessibility and W3C Standards
- YouTube: Web Accessibility Guidelines - How to make your code Web Accessible
Activities
[edit | edit source]- Review Mozilla: What is accessibility?.
- Use the W3C Markup Validation Service to validate HTML for one or more web pages. Make any corrections necessary to pass the validation check.
- Use the WAVE Web Accessibility Evaluation Tool to evaluate web accessibility for one or more web pages. Make any corrections necessary to pass the accessibility check. Review SuperCoolDesign: How To Write Good Alt Text. Verify that ALT tags fully describe all images and multimedia used.
- Use the WebAIM: Contrast Checker to check color contrast for one or more web pages. Make any corrections necessary to pass the contrast check.
- Use the Paletton website to identify good color schemes. Experiment with monochromatic, adjacent-color, three-color, and four-color designs.
Lesson Summary
[edit | edit source]- Web accessibility is the inclusive practice of ensuring there are no barriers that prevent interaction with, or access to, websites on the World Wide Web by people with physical disabilities, situational disabilities, and socio-economic restrictions on bandwidth and speed.[2]
- The needs that web accessibility aims to address include:[3]
- Visual
- Motor/mobility
- Auditory
- Seizures
- Cognitive and intellectual
- Assistive technologies include:
- Screen reader software
- Braille terminals
- Screen magnification software
- Speech recognition software
- Keyboard overlays
- Subtitles / captions
- The Worldwide Web Consortium (W3C) has published Web Content Accessibility Guidelines.[4]
- Web accessibility depends on a combination of:[5]
- Content
- User agents (web browsers, etc.)
- Assistive technology
- User strategies (knowledge, experience, training, etc.)
- Content developers
- Authoring tools
- Evaluation tools
- Web accessibility guidelines include:[6]
- Authoring Tool Accessibility Guidelines (ATAG)
- Web Content Accessibility Guidelines (WCAG)
- User Agent Accessibility Guidelines (UAAG)
- Compliance with web accessibility guidelines is a legal requirement primarily in North America, Europe, parts of South America and parts of Asia.[7]
Key Terms
[edit | edit source]- accessibility
- The design of products, devices, services, vehicles, or environments so as to be usable by people with disabilities.[8]
- assistive technology
- Adaptive and rehabilitative devices for people with disabilities and the elderly.[9]
- authoring tool
- A program that has pre-programmed elements for the development of interactive multimedia software titles.[10]
- disability
- Any condition that makes it more difficult for a person to do certain activities or effectively interact with the world around them (socially or materially).[11]
- user agent
- Any software, acting on behalf of a user, which retrieves, renders and facilitates end-user interaction with Web content.[12]
Assessments
[edit | edit source]- Flashcards: Quizlet: Web Site Accessibility
- Quiz: Quizlet: Web Site Accessibility
See Also
[edit | edit source]References
[edit | edit source]- ↑ Wikipedia: Web accessibility
- ↑ Wikipedia: Web accessibility
- ↑ Wikipedia: Web accessibility
- ↑ Wikipedia: Web accessibility
- ↑ Wikipedia: Web accessibility
- ↑ Wikipedia: Web accessibility
- ↑ Wikipedia: Web accessibility
- ↑ Wikipedia: Accessibility
- ↑ Wikipedia: Assistive technology
- ↑ Wikipedia: Authoring system
- ↑ Wikipedia: Disability
- ↑ Wikipedia: User agent
Lesson 13 - JavaScript
[edit | edit source]
JavaScript, often abbreviated as JS, is a high-level, dynamic, weakly typed, prototype-based, multi-paradigm, and interpreted programming language.[1] This lesson introduces JavaScript and uses it to create and manipulate canvas graphics.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[2]
- Analyse the requirements for web documents
- Determine the necessary dynamic functionality of the web document
- Determine the appropriate language to achieve that functionality
- Determine the web document requirements
- Design and produce web documents
- Design the web document, and embedded scripts to achieve the required functionality
- Write a simple hypertext markup language (HTML), considering accessibility
- Write embedded scripts
- Test the scripts and debug
- Test the web document against the required functionality, and reiterate until correct
- Complete the documentation and submit it to the appropriate person for their approval
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: JavaScript Introduction
- YouTube: JavaScript Statements
- YouTube: JavaScript Variables
- YouTube: HTML5 Canvas Tag Tutorial Learn to Draw and Animate Using Javascript
Student Presentations
[edit | edit source]Examples
[edit | edit source]To test the following examples, copy the code and paste it in the body of an HTML file and view the file in a browser, or use a JavaScript test environment such as W3Schools: Tryit Editor.
document.getElementById()
[edit | edit source]document.getElementById() returns a reference to an element based on its ID.[3]
<p id="text"></p>
<script>
document.getElementById("text").innerHTML = "Hello Wikiversity!";
</script>
Date()
[edit | edit source]Date() creates a JavaScript Date object for the current date and time according to system settings.[4][5]
<p id="text"></p>
<script>
document.getElementById("text").innerHTML = Date();
</script>
Canvas
[edit | edit source]The <canvas> element is part of HTML5 and allows for dynamic, scriptable rendering of 2D shapes and bitmap images.[6]
<canvas id="example" width="360" height="240">
This text is displayed if your browser does not support HTML5 Canvas.
</canvas>
Canvas Text
[edit | edit source]JavaScript is used to draw text on a canvas.[7][8]
<canvas id="example" width="360" height="240">
This text is displayed if your browser does not support HTML5 Canvas.
</canvas>
<script>
var example = document.getElementById("example");
var context = example.getContext("2d");
// Set stroke and fill to blue
context.strokeStyle = "blue";
context.fillStyle = "blue";
// Select font, alignment, draw text, and fill characters
context.font = "36px sans-serif";
context.textAlign="center";
context.strokeText("HTML5 Canvas", 160, 50);
context.fillText("HTML5 Canvas", 160, 50);
</script>
Canvas Lines
[edit | edit source]JavaScript is used to draw lines on a canvas.[9][10]
<canvas id="example" width="360" height="240">
This text is displayed if your browser does not support HTML5 Canvas.
</canvas>
<script>
var example = document.getElementById("example");
var context = example.getContext("2d");
// Draw a line, width 4
context.lineWidth = 4;
context.moveTo(30, 65);
context.lineTo(290, 65);
context.stroke();
</script>
Canvas Circle
[edit | edit source]JavaScript is used to draw shapes on a canvas.[11][12]
<canvas id="example" width="360" height="240">
This text is displayed if your browser does not support HTML5 Canvas.
</canvas>
<script>
var example = document.getElementById("example");
var context = example.getContext("2d");
// Draw a red circle, radius 35
context.beginPath();
context.fillStyle = 'red';
context.arc(60, 140, 35, 0, 2 * Math.PI, false);
context.fill();
context.closePath();
</script>
Canvas Square
[edit | edit source]JavaScript is used to draw shapes on a canvas.[13][14]
<canvas id="example" width="360" height="240">
This text is displayed if your browser does not support HTML5 Canvas.
</canvas>
<script>
var example = document.getElementById("example");
var context = example.getContext("2d");
// Draw a green square, side 70
context.beginPath();
context.fillStyle = 'green';
context.fillRect(130, 105, 70, 70);
context.closePath();
</script>
Canvas Triangle
[edit | edit source]JavaScript is used to draw shapes on a canvas.[15][16]
<canvas id="example" width="360" height="240">
This text is displayed if your browser does not support HTML5 Canvas.
</canvas>
<script>
var example = document.getElementById("example");
var context = example.getContext("2d");
// Draw a blue triangle
context.beginPath();
context.fillStyle = 'blue';
context.beginPath();
context.moveTo(270, 105);
context.lineTo(235, 175);
context.lineTo(310, 175);
context.fill();
context.closePath();
</script>
Activities
[edit | edit source]- Complete one or more of the following tutorials:
- Display text.
- Review CodeMaven: JavaScript Hello World. Follow the example but use a paragraph tag rather than a div tag, and display
Hello <name>!, replacing <name> with your name.
- Review CodeMaven: JavaScript Hello World. Follow the example but use a paragraph tag rather than a div tag, and display
- Display the current date and time.
- Review W3Schools: JavaScript Dates. Use the Date() function to display the current date and time on a web page.
- Use the HTML5 canvas.
- Review W3Schools: HTML5 Canvas Intro. Experiment with the TutorialsPoint: Web Canvas Demo.
- Review W3Schools: HTML5 Canvas. Add a canvas drawing using JavaScript to the web page you created in the previous lesson.
Lesson Summary
[edit | edit source]- JavaScript, often abbreviated as JS, is a high-level, interpreted programming language.[17]
- Alongside HTML and CSS, JavaScript is one of the three core technologies of World Wide Web content engineering. It is used to make webpages interactive and provide online programs, including video games.[18]
- Although there are strong outward similarities between JavaScript and Java, including language name, syntax, and respective standard libraries, the two languages are distinct and differ greatly in design.[19]
- All modern Web browsers support JavaScript with built-in interpreters.[20]
- The most common use of JavaScript is to add client-side behavior to HTML pages, also known as Dynamic HTML (DHTML).[21]
- Scripts are embedded in or included from HTML pages and interact with the Document Object Model (DOM) of the page. Some simple examples of this usage are:[22]
- Loading new page content or submitting data to the server via Ajax without reloading the page (for example, a social network might allow the user to post status updates without leaving the page).
- Animation of page elements, fading them in and out, resizing them, moving them, etc.
- Interactive content, for example games, and playing audio and video.
- Validating input values of a Web form to make sure that they are acceptable before being submitted to the server.
- Transmitting information about the user's reading habits and browsing activities to various websites. Web pages frequently do this for Web analytics, ad tracking, personalization or other purposes.
- JavaScript and the DOM provide the potential for malicious authors to deliver scripts to run on a client computer via the Web.
- Browsers contain security risks using two restrictions:[23]
- First, scripts run in a sandbox in which they can only perform Web-related actions, not general-purpose programming tasks like creating files.
- Second, scripts are constrained by the same-origin policy: scripts from one Web site do not have access to information such as usernames, passwords, or cookies sent to another site.
- Most JavaScript-related security bugs are breaches of either the same origin policy or the sandbox.
- Developers of client-server applications must recognize that untrusted clients may be under the control of attackers. Some implications are:[24]
- Web site authors cannot perfectly conceal how their JavaScript operates because the raw source code must be sent to the client.
- JavaScript form validation only provides convenience for users, not security.
- Scripts can be selectively disabled, so JavaScript can't be relied on to prevent operations such as right-clicking on an image to save it.
- It is extremely bad practice to embed sensitive information such as passwords in JavaScript because it can be extracted by an attacker.
- Script debuggers are integrated within Internet Explorer, Firefox, Safari, Google Chrome, Opera and Node.js.[25]
- JavaScript is case sensitive and typically follows a camelCase naming convention.[26]
- JavaScript comments are indicated with either
//for single-line comments or/* */for block comments.[27] - Variables in standard JavaScript have no type attached, and any value can be stored in any variable.[28]
- The
<canvas>element is part of HTML5 and allows for dynamic, scriptable rendering of 2D shapes and bitmap images.[29]
Key Terms
[edit | edit source]- AJAX
- A set of Web development techniques using many Web technologies on the client side to create asynchronous Web applications using JavaScript.[30]
- cross-site scripting (XSS)
- A type of computer security vulnerability typically found in web applications which enables attackers to inject client-side scripts into web pages viewed by other users.[31]
- Document Object Model (DOM)
- A cross-platform and language-independent application programming interface that treats an HTML, XHTML, or XML document as a tree structure wherein each node is an object representing a part of the document.[32]
- ECMAScript
- A trademarked scripting-language specification created to standardize JavaScript, so as to foster multiple independent implementations.[33]
- JavaScript engine
- A program or interpreter which executes JavaScript code.[34]
- jQuery
- A cross-platform JavaScript library designed to simplify the client-side scripting of HTML.[35]
- JSON
- An open-standard file format that uses human-readable text to transmit data objects consisting of attribute–value pairs and array data types.[36]
- same-origin policy
- A web application security model in which a web browser permits scripts contained in a first web page to access data in a second web page, but only if both web pages have the same origin.[37]
- syntax
- The set of rules that defines the combinations of symbols that are considered to be a correctly structured document or fragment in that programming language.[38]
- WebAssembly (wasm, WA)
- A web standard that defines a binary format and a corresponding assembly-like text format for executable code in Web pages.[39]
Assessments
[edit | edit source]- Flashcards: Quizlet: Fundamental JavaScript Concepts
- JavaScript Flashcards: Basic Programming Principles
- Quiz: Quizlet: Fundamental JavaScript Concepts
See Also
[edit | edit source]- JavaScript
- Wikibooks: JavaScript
- WebPageFX: Bouncing a Ball Around with HTML5 and JavaScript
- Mozilla: 2D Breakout Game Pure JavaScript
- Microsoft: JavaScript Fundamentals for Absolute Beginners
- Flavio Copes: The HTML Canvas Guide
References
[edit | edit source]- ↑ Wikipedia: JavaScript
- ↑ Training.gov.au: ICTWEB411 - Produce basic client-side script for dynamic web pages
- ↑ Mozilla: document.getElementById()
- ↑ Mozilla: Date
- ↑ W3Schools: JavaScript Dates
- ↑ Wikipedia: Canvas element
- ↑ Wikipedia: Canvas element
- ↑ W3Schools: HTML5 Canvas
- ↑ Wikipedia: Canvas element
- ↑ W3Schools: HTML5 Canvas
- ↑ Wikipedia: Canvas element
- ↑ W3Schools: HTML5 Canvas
- ↑ Wikipedia: Canvas element
- ↑ W3Schools: HTML canvas fillRect
- ↑ Wikipedia: Canvas element
- ↑ Mozilla: Drawing shapes with canvas
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript
- ↑ Wikipedia: JavaScript syntax
- ↑ Wikipedia: JavaScript syntax
- ↑ Wikipedia: JavaScript syntax
- ↑ Wikipedia: Canvas element
- ↑ Wikipedia: Ajax (programming)
- ↑ Wikipedia: Cross-site scripting
- ↑ Wikipedia: Document Object Model
- ↑ Wikipedia: ECMAScript
- ↑ Wikipedia: JavaScript engine
- ↑ Wikipedia: jQuery
- ↑ Wikipedia: JSON
- ↑ Wikipedia: Same-origin policy
- ↑ Wikipedia: Syntax (programming languages)
- ↑ Wikipedia: WebAssembly
Lesson 14 - Databases
[edit | edit source]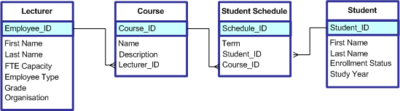


This lesson introduces database concepts.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[1][2]
- Recognize essential database concepts.
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: Relational Database Concepts
- YouTube: Intro to SQL
- YouTube: SQL JOIN Statement
- YouTube: SQL GROUP BY, HAVING & ORDER BY
- YouTube: SQL INSERT, UPDATE, and DELETE
Activities
[edit | edit source]- Complete one or more of the following tutorials:
- Practice writing single-table SELECT statements using W3Schools SQL TryIt Editor.
- Select all customers (SELECT *).
- Select only customer id and customer name fields (SELECT fields).
- Select customer name, address, city, and postal code for all customers from the United Kingdom (WHERE field = 'value').
- Select contact name and customer name for all customers, sorted alphabetically by contact name (ORDER BY field).
- Count the total number of customers (COUNT(*)).
- Count the number of customers from each country (GROUP BY).
- Count the number of customers from each country and sort the list in descending order by count and ascending order by country in case of a tie (GROUP BY, ORDER BY).
- Count the number of customers from each country and sort the list in descending order by count and ascending order by country in case of a tie, listing only those countries with more than 10 customers (GROUP BY, HAVING, ORDER BY).
- Practice writing multiple-table SELECT statements using W3Schools SQL TryIt Editor.
- Select customer name, order ID, and order date for all customers (INNER JOIN).
- Select customer name, order number, and order date for all customers, renaming the OrderID field as Order Number (INNER JOIN, AS).
- Select customer name, order number, and order date for all customers, sorted by customer name and order number (INNER JOIN, AS, ORDER BY).
- Select order number, order date, product name, and quantity ordered for all customers (INNER JOIN, AS).
- Select order number, order date, product name, quantity ordered, and extended price (quantity * price) for all customers (INNER JOIN, AS, calculated field).
- Select order number, order date, product name, quantity ordered, and extended price for customer 2 (INNER JOIN, AS, calculated field, WHERE).
- Select order number, order date, product name, quantity ordered, and extended price for customer 'Around the Horn' (INNER JOIN, AS, calculated field, WHERE).
- Practice writing INSERT, UPDATE, and DELETE statements using W3Schools SQL TryIt Editor.
- Add a new shipper with ID 4, name 'On Time Delivery', and phone '(503) 555 0123' (INSERT).
- Increase prices on all products by 1 (UPDATE).
- Reduce prices on all products by 1 (UPDATE).
- Change the new shipper's name from 'On Time Delivery' to 'On-Time Delivery' (UPDATE, WHERE).
- Delete the new shipper (DELETE, WHERE).
Lesson Summary
[edit | edit source]- A database is an organized collection of data.[3]
- A relational database is a collection of schemas, tables, queries, reports, views, and other elements.[4]
- A database-management system (DBMS) is a computer-software application that interacts with end-users, other applications, and the database itself to capture and analyze data.[5]
- A general-purpose DBMS allows the definition, creation, querying, update, and administration of databases.[6]
- Well-known DBMSs include MySQL, PostgreSQL, EnterpriseDB, MongoDB, MariaDB, Microsoft SQL Server, Oracle Database, Sybase, SAP HANA, MemSQL, SQLite and IBM DB2.[7]
- Virtually all relational database systems use SQL (Structured Query Language) as the language for querying and maintaining the database.[8]
- SQL (Structured Query Language) is a special-purpose programming language designed for managing data held in a relational database management system (RDBMS), or for stream processing in a relational data stream management system (RDSMS).[9]
- Data Manipulation Language (DML) commands include SELECT, INSERT, UPDATE, and DELETE.[10]
- The SQL SELECT statement returns a result set of records from one or more tables.[11]
- An asterisk ("*") can be used to specify that the query should return all columns of the queried tables.[12]
- SQL statements are terminated with a semicolon (";").[13]
- A WHERE clause in SQL specifies that a SQL Data Manipulation Language (DML) statement should only affect rows that meet specified criteria.[14]
- By default, relational database systems may return data rows in any order, or more specifically, without any order.[15]
- An ORDER BY clause in SQL specifies that a SQL SELECT statement returns a result set with the rows being sorted by the values of one or more columns.[16]
- A SQL JOIN clause combines columns from one or more tables in a relational database.[17]
- An SQL INSERT statement adds one or more records to any single table in a relational database.[18]
- An SQL UPDATE statement changes the data of one or more records in a table. Either all the rows can be updated, or a subset may be chosen using a condition.[19]
- An SQL DELETE statement removes one or more records from a table. Either all records are removed, or a subset may be chosen using a condition.[20]
Key Terms
[edit | edit source]- AJAX (Asynchronous JavaScript And XML)
- A set of Web development techniques using multiple Web technologies on the client side to create asynchronous Web applications that can send and retrieve data from a server asynchronously (in the background) without interfering with the display and behavior of the existing page.[21]
- data modeling
- A process used to define and analyze data requirements needed to support the business processes within the scope of corresponding information systems in organizations.[22]
- database
- An organized collection of data.[23]
- database management system (DBMS)
- A computer-software application that interacts with end-users, other applications, and the database itself to capture and analyze data.[24]
- field
- A set of data values of a particular simple type, one for each row of the table.[25]
- foreign key
- A field (or collection of fields) in one table that uniquely identifies a row of another table or the same table.[26]
- index
- A data structure that improves the speed of data retrieval operations on a database table at the cost of additional writes and storage space to maintain the index data structure.[27]
- many-to-many relationship
- A type of cardinality that refers to the relationship between two entities A and B in which A may contain a parent instance for which there are many children in B and vice versa.[28]
- one-to-many relationship
- A type of cardinality that refers to the relationship between two entities (see also entity–relationship model) A and B in which an element of A may be linked to many elements of B, but a member of B is linked to only one element of A.[29]
- Open Database Connectivity (ODBC)
- A standard application programming interface (API) for accessing database management systems (DBMS).[30]
- primary key
- A field (or collection of fields) in one table that uniquely identifies a row in the table.[31]
- query
- A precise request for information retrieval with database and information systems.[32]
- record
- A single, implicitly structured data item in a table.[33]
- relational database
- A collection of schemas, tables, queries, reports, views, and other elements.[34]
- Structured Query Language (SQL)
- A domain-specific language used in programming and designed for managing data held in a relational database management system[35]
- table
- A collection of related data held in a structured format within a database, consisting of columns and rows.[36]
Assessments
[edit | edit source]See Also
[edit | edit source]References
[edit | edit source]- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Wikipedia: Database
- ↑ Wikipedia: Database
- ↑ Wikipedia: Database
- ↑ Wikipedia: Database
- ↑ Wikipedia: Database
- ↑ Wikipedia: Relational database
- ↑ Wikipedia: SQL
- ↑ Wikipedia: Data manipulation language
- ↑ Wikipedia: Select (SQL)
- ↑ Wikipedia: SQL
- ↑ Wikipedia: SQL
- ↑ Wikipedia: Where (SQL)
- ↑ Wikipedia: Order by
- ↑ Wikipedia: Order by
- ↑ Wikipedia: Join (SQL)
- ↑ Wikipedia: Insert (SQL)
- ↑ Wikipedia: Update (SQL)
- ↑ Wikipedia: Delete (SQL)
- ↑ Wikipedia: AJAX
- ↑ Wikipedia: Data modeling
- ↑ Wikipedia: Database
- ↑ Wikipedia: Database
- ↑ Wikipedia: Column (database)
- ↑ Wikipedia: Foreign key
- ↑ Wikipedia: Database index
- ↑ Wikipedia: Many-to-many (data model)
- ↑ Wikipedia: One-to-many (data model)
- ↑ Wikipedia: Open Database Connectivity
- ↑ Wikipedia: Foreign key
- ↑ Wikipedia: Query
- ↑ Wikipedia: Row (database)
- ↑ Wikipedia: Database
- ↑ Wikipedia: SQL
- ↑ Wikipedia: Table (database)
Lesson 15 - Project Management
[edit | edit source]
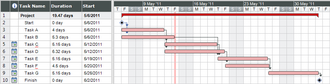
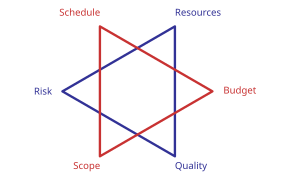
This lesson introduces project management concepts.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[1][2]
- Relate project management concepts and terms to the IT profession.
- Distinguish between proprietary and open-source development models.
Readings
[edit | edit source]Multimedia
[edit | edit source]- YouTube: Introduction to Project Management
- YouTube: Project Management Fundamentals
- YouTube: Create a Basic Gantt Chart
Student Presentations
[edit | edit source]Activities
[edit | edit source]- Plan a project related to this course. This may include a web site or some type of multimedia presentation. For the project:
- Identify the project objectives, scope, purpose, and deliverables to be produced.[3]
- Identify all stakeholders who might be involved with or impacted by the project, and seek out their requirements and suggestions.
- Create a project plan. Include a list of activities to be completed (work breakdown structure), timeline (schedule), people involved (resources), a quality plan, a budget (in hours and/or financial cost), and any risks associated with being able to complete the project successfully.
- Select project management software.
- Research free project management software options. These may include websites, downloadable software, or templates for office applications.
- Select a a project management software solution for use in managing the project plan created above. Add your project activities, expected timeline, resources, and quality assurance / quality control activities.
- If your software supports it, create or view the project Gantt chart. If not, review Excel-Easy: Gantt Chart, Spreadsheet Daddy: Gantt Chart, or search the Internet for a free Gantt chart template and create a Gantt chart using spreadsheet software.
- Complete (execute) the project.
- Use your project plan and software selection to monitor the project, and update the schedule and hours invested as you go.
- If you will be completing the project in coming weeks, describe your project plan, including schedule, quality, and risks, and the milestones that will be necessary to complete the project successfully.
- If you won't be completing the project as part of this course, simulate project execution by updating the project schedule and hours invested. Assume that the schedule does not always go according to plan. Anticipate delays and overruns, and adjust the schedule as necessary to meet the deadline.
- Close the project.
- Meet with the project stakeholders to discuss the project and obtain approval for the deliverables.
- Prepare a lessons learned report describing what went well during the project and what changes you would make to improve similar project plans in the future.
Lesson Summary
[edit | edit source]- Project management is the discipline of initiating, planning, executing, controlling, and closing the work of a team to achieve specific goals and meet specific success criteria.[4]
- A project is a temporary endeavor designed to produce a unique product, service or result with a defined beginning and end undertaken to meet unique goals and objectives.[5]
- The primary constraints are scope, time, budget, and quality.[6]
- Major project management phases or process groups generally include: initiating, planning, executing, monitoring and controlling, and closing.[7]
- Initiating determines the nature and overall scope of the project. This includes business requirements, operational analysis, financial analysis, stakeholder analysis, SWOT analysis, and a project charter.[8]
- Planning determines the scope statement, work breakdown structure, schedule, resources, quality assurance and quality control, cost planning, and risk planning.[9]
- Executing follows the project plan to complete the project's deliverables.[10]
- Monitoring and controlling observes project progress so that potential problems can be identified and corrective action can be taken, when necessary. Monitoring and controlling includes project scope, schedule, cost, and quality, while addressing risks and controlling changes.[11]
- Closing finalizes the project with formal acceptance of the project deliverables and some type of post implementation review identifying lessons learned to be applied to future projects.[12]
- Initiating, planning, and executing generally require formal approval before proceeding to the next phase.[13]
- A project manager is the person accountable for accomplishing the stated project objectives.[14]
Key Terms
[edit | edit source]- ISO 9000
- A family of quality management systems standards designed to help organizations ensure that they meet the needs of customers and other stakeholders while meeting statutory and regulatory requirements related to a product or program.[15]
- change management
- Change control processes wherein changes to the scope of a project are formally introduced and approved.[16]
- constraint
- Anything that limits a project from achieving its goal, including scope, time, cost, and quality.[17][18]
- Gantt chart
- A type of bar chart that illustrates a project schedule.[19]
- milestone
- Tools used in project management to mark specific points along a project timeline.[20]
- needs analysis
- A systematic process for determining and addressing needs, or "gaps" between current conditions and desired conditions or "wants".[21]
- Project Management Body of Knowledge (PMBOK)
- A set of standard terminology and guidelines for project management developed by PMI.[22]
- Project Management Institute (PMI)
- A US nonprofit professional organization that provides services including the development of standards, research, education, publication, training, and accreditation in project management.[23]
- program management
- The process of managing several related projects.[24]
- project schedule
- A listing of a project's milestones, activities, and deliverables, usually with intended start and finish dates.[25]
- quality assurance (QA)
- A way of preventing mistakes or defects in manufactured products and avoiding problems when delivering solutions or services to customers.[26]
- quality control (QC)
- A process by which entities review the quality of all factors involved in production.[27]
- quality management
- Ensures that an organization, product or service is consistent through four main components: quality planning, quality assurance, quality control, and quality improvement.[28]
- resource
- People, equipment, facilities, funding, or anything else required for the completion of a project activity.[29]
- Return on Investment (ROI)
- The benefit to the organization resulting from an investment of some resource.[30]
- scope
- The work that needs to be accomplished to deliver a product, service, or result with the specified features and functions.[31]
- scope creep
- Changes, continuous or uncontrolled growth in a project’s scope, at any point after the project begins.[32]
- stakeholder
- An individual, group, or organization, who may affect, be affected by, or perceive itself to be affected by a decision, activity, or outcome of a project.[33]
- statement of work (SOW)
- A document that defines project-specific activities, deliverables and timelines for a vendor providing services to the client.[34]
- SWOT analysis
- An evaluation of the strengths, weaknesses, opportunities, and threats of an organization, project or business venture.[35]
- task
- An activity that needs to be accomplished within a defined period of time or by a deadline to work towards project-related goals[36]
- work breakdown structure (WBS)
- A deliverable-oriented breakdown of a project into smaller components and manageable sections.[37]
Assessments
[edit | edit source]- Flashcards: Quizlet: Internet Business Associate Lesson 10
- Quiz: Quizlet: Internet Business Associate Lesson 10
See Also
[edit | edit source]References
[edit | edit source]- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Method123: Project Initiation Phase
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: Project management
- ↑ Wikipedia: ISO 9000
- ↑ Wikipedia: Change control
- ↑ Wikipedia: Theory of constraints
- ↑ Wikipedia: Project management triangle
- ↑ Wikipedia: Gantt chart
- ↑ Wikipedia: Milestone (project management)
- ↑ Wikipedia: Needs assessment
- ↑ Wikipedia: Project Management Body of Knowledge
- ↑ Wikipedia: Project Management Institute
- ↑ Wikipedia: Program management
- ↑ Wikipedia: Schedule (project management)
- ↑ Wikipedia: Quality assurance
- ↑ Wikipedia: Quality control
- ↑ Wikipedia: Quality management
- ↑ Wikipedia: Resource (project management)
- ↑ Wikipedia: Return on investment
- ↑ Wikipedia: Scope (project management)
- ↑ Wikipedia: Scope creep
- ↑ Wikipedia: Project stakeholder
- ↑ Wikipedia: Statement of work
- ↑ Wikipedia: SWOT analysis
- ↑ Wikipedia: Task (project management)
- ↑ Wikipedia: Work breakdown structure
Lesson 16 - IT Careers
[edit | edit source]
This lesson introduces Information Technology careers.
Objectives and Skills
[edit | edit source]Objectives and skills for this lesson include:[1][2]
- Identify job roles in the Information Technology (IT) industry, including the responsibilities, tasks and skills they require.
- Manage career opportunities in the IT industry.
Readings
[edit | edit source]- Wikipedia: Career
- Wikipedia: Job search
- Wikipedia: Résumé
- Bureau of Labor Statistics: Computer and Information Technology Careers
Multimedia
[edit | edit source]- YouTube: How To Get Started in a Information Technology career
- YouTube: Career Path in IT
- YouTube: Career In Tech: How To Find The Right Role For You
Student Presentations
[edit | edit source]Activities
[edit | edit source]- Career Planning - Complete one or more of the following:
- Complete the tutorial GCFLearnFree: Career Planning and Salary. Then download and fill out the GCFLearnFree: Career Planning Worksheet.
- Complete the tutorial GCFLearnFree: Job Search and Networking. Then download and fill out the GCFLearnFree: Personal Branding Worksheet.
- Job Outlook and Preparation - Complete one or more of the following:
- Review Creating IT Futures: IT Career videos. For one or more IT career job titles, use the BLS.gov: Occupational Outlook Handbook and Salary.com to research job prospects, education requirements, and current salary ranges for positions that interest you.
- Review IT Career Finder: IT Certfications. Research preparation requirements and current salary ranges for certifications that interest you.
- Resume and LinkedIn Profile - Complete one or more of the following:
- Complete the tutorial GCFLearnFree: Resume Writing. Use a sample resume template and create your own resume. Save the resume in different formats (plain text, PDF, word processor).
- Complete the tutorial GCFLearnFree: LinkedIn Basics. Create a LinkedIn profile. Add your summary, experience, and education.
- Connect with people you know (friends, family members, classmates, current and former work colleagues, teachers, professors, etc.) who would be able to recommend you to future employers and employment opportunities.
Lesson Summary
[edit | edit source]- A career is an individual's metaphorical "journey" through learning, work and other aspects of life.[3]
- Career management describes the active and purposeful management of a career by an individual.[4]
- Career choices are based on natural talents, work style, social interaction, work-life balance, altruism, stress levels, and income needs.[5]
- Career success may be measured by status, earnings, satisfaction, personal achievement, and personal values.[6]
- Job searching is the act of looking for employment, due to unemployment, underemployment, discontent with a current position, or a desire for a better position.[7]
- The immediate goal of job seeking is usually to obtain a job interview with an employer which may lead to getting hired.[8]
- Many job seekers research the employers to which they are applying, and some employers see evidence of this as a positive sign of enthusiasm for the position or the company, or as a mark of thoroughness.[9]
- Job seekers need to pay attention to what potential employers and recruiters find when they do their pre-interview information gathering about applicants.[10]
- Contacting as many people as possible is a highly effective way to find a job. It is estimated that 50% or higher of all jobs are found through personal connections (networking).[11]
- After finding a desirable job, seekers apply for the job by responding to an advertisement, applying through a website, or emailing or mailing in a hard copy of a résumé to a prospective employer.[12]
- Once an employer has received résumés, they will make a list of potential employees to be interviewed based on the résumé and any other information contributed.[13]
- A résumé (also spelled resume), is a document used by a person to present their backgrounds and skills.[14]
Key Terms
[edit | edit source]- computer programmer
- Write and test code that allows computer applications and software programs to function properly.[15]
- computer support specialist
- Provide help and advice to people and organizations using computer software or equipment.[16]
- computer systems analyst
- Study an organization’s current computer systems and procedures and design information systems solutions to help the organization operate more efficiently and effectively.[17]
- database administrator
- Use specialized software to store and organize data, such as financial information and customer shipping records.[18]
- information security analyst
- Plan and carry out security measures to protect an organization’s computer networks and systems.[19]
- network administrator
- Responsible for the day-to-day operation of computer networks.[20]
- network architect
- Design and build data communication networks, including local area networks (LANs), wide area networks (WANs), and intranets.[21]
- software developer
- Develop applications that allow people to do specific tasks on a computer or another device or develop the underlying systems that run the devices or that control networks.[22]
- system administrator
- Responsible for the day-to-day operation of computer systems.[23]
- web designer
- Design website front end, user interface, user experience, etc.[24]
- web developer
- Develop website back end, functionality, database connectivity, etc.[25]
Assessments
[edit | edit source]- Flashcards: Quizlet: IT Careers
- Quiz: Quizlet: IT Careers
See Also
[edit | edit source]- Careers and Employment
- LinkedIn: 10 LinkedIn Tips for Students & New Grads
- USA Today: 5 Templates That Will Make Writing the Perfect LinkedIn Summary a Breeze
References
[edit | edit source]- ↑ CIW: Internet Business Associate Exam Objectives
- ↑ CIW: Internet Business Associate Course Description
- ↑ Wikipedia: Career
- ↑ Wikipedia: Career
- ↑ Wikipedia: Career
- ↑ Wikipedia: Career
- ↑ Wikipedia: Job search
- ↑ Wikipedia: Job search
- ↑ Wikipedia: Job search
- ↑ Wikipedia: Job search
- ↑ Wikipedia: Job search
- ↑ Wikipedia: Job search
- ↑ Wikipedia: Job search
- ↑ Wikipedia: Résumé
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ BLS: Computer and Information Technology
- ↑ Rasmussen: Web Designer vs. Web Developer
- ↑ Rasmussen: Web Designer vs. Web Developer
