Introduction to Computers/Security
| This page has been nominated for cleanup for the following reason: Needs to be rewritten to focus on practical concerns relevant to a modern survey course, rather than outdated techno-alarmism.. Please edit this page to improve it. See this module's talk page for discussion. |
Course Navigation
| << Previous - Networks | Next - Internet >> |
|---|
|
Introduction to Computers → Security
|
Computer Security
[edit | edit source]Computer Security is the field which tries to keep computers safe and secure. Security means allowing things you do want, while stopping things you don't want from happening. Parts of this include authentication and validation (making sure you are who you claim to be), encryption (making sure data gets where you want to go, without others being able to observe it) and physical security.

Malware
[edit | edit source]Malware is any software specifically designed to damage a computer system without owner knowledge. The examples of malware are worms, viruses, Trojan horses and etc. Some normal computer users are unfamiliar with the term and never use it. Instead the term: "computer virus" is used. It describes all kinds of malware, though not all malware are viruses. It is short for "malicious software."
Trojan horse
[edit | edit source]A Trojan Horse is program that is packaged with a useful application, usually free, such as a screen or game saver, but carries a destructive virus, that creates problems for your computer without your knowledge. Once the program initiates, the camouflaged virus is released creating havoc and mayhem. example: FormatC. (347) This virus is named after the mythical Trojan horse that was left as a gift to the Trojan people from the Achaeans as a trick. By hiding in the horse, Achaean soldiers were able to invade the walled city of Troy. (see w:Trojan_War) A trojan horse is one of the biggest threats to computer security as they cannot be identified easily. [1]
Virus
[edit | edit source]A "deviant" program stored on a computer floppy disk, hard drive, or CD, that can cause unexpected and often undesirable effects such as destroying or corrupting data. An example of a virus was the "Love Bug" which started in the Philippines in May 2000 and caused approximately $10 billion in damage.
Worm
[edit | edit source]A worm is a type of malicious software (malware) that copies itself repeatedly into a computers memory (RAM) using up all available RAM. It also can copy on to a disk drive so it can load into RAM again. It spreads through a network to infect the RAM on other connected computers.
A worm can infect your computer through email (the worm is disguised by pretending it came from somewhere it did not). When you open the email attachment the worm looks through your Windows Outlook and other address books choosing names at random. Using built-in software, the worm sends copies of itself to many names in the address books.
Will take over ram on a computer and will take over ram on others computers that the original computer is hooked up to.
What they do
[edit | edit source]Adware
[edit | edit source]Adware is used for advertising purposes. Although it is often legal and used by big companies such as Verizon and Panasonic, it can be used by illegitimate companies promoting pornography or gambling. Adware works by automatically downloading an advertisement to a computer that is accessing a specific website. In addition, Adware is often downloaded with software. This causes the advertisements to automatically pop up when the program is in use.
Adware usually exploit the cookie tracker to monitor what sites you're going to and record your browsing habit for marketing purposes.
Examples of Adware programs include Ad-Aware and Spybot Search & Destroy.
Spyware
[edit | edit source]Spyware is misleading software that is secretly installed on a computer through the web. Confidential information can be obtained by the installer such as passwords, keystrokes and email addresses.
Too much spyware can slow down the operation of a computer. Running anti-software programs have become very popular! (wikipedia, 2007)
Web Page can take over Router
[edit | edit source]According to PC World this is how a router takes over a web page: The victim would visit a malicious Web page that would use JavaScript code to trick the browser into making changes on the Web-based router configuration page. The JavaScript could tell the router to let the bad guys remotely administer the device, or it could force the router to download new firmware, again putting the router under the hacker's control. The attacker would be able to control his victim's Internet communications.

Viruses to Hit 1 Million in 2008
[edit | edit source]
According to PC World, the total number of viruses are expected to reach one million by year's end. The reason for the increase in viruses is that as individuals improve security practices, malware writers are forced to create new types of viruses and exploits more regularly. Paul Ducklin, chief technology officer at Sophos said the decline in infections are due to better gateway filters, more relevant corporate policies and user education, and dilution from a rise in legitimate e-mail traffic. [2]
Boot Sector Virus
[edit | edit source]This is a virus that replaces the boot instructions on the system software with its own. When the computer is booting, the virus sneaks into the main memory before the OS. This then allows the virus to infect other files. Any diskette used on this computer becomes infected. When this disk is moved to another computer, the contagion continues. [347]
Macro Virus
[edit | edit source]A virus which takes advantage of a task where miniature programs (a.k.a. macros) are rooted in regular data files (files made through emails, spreadsheets...) which are sent over computer networks. Example: a virus that hides in a power point presentation sent over email.
Logic Bomb
[edit | edit source]A logic bomb is when there is a piece of code that has been placed intentionally into a software system. When specific conditions are met (like a date or a certain combination of keys being pressed), this code will set off harmful activities within your computer. For example, a programmer may place a logic bomb in the software so that when he leaves the company he is working for, all the information on his computer will be destroyed. (don't try this at work) w:Logic_bomb
DOS
[edit | edit source]DOS stands for Denial Of Service.This happens when a webserver cannot handle all the request asked. It "can" happenen legitimately when lots of people go to that website, but usually it happens because many computers have been zombied by a logic bomb virus to go to a specific website at the same time.
Email Related issues
[edit | edit source]Spam
[edit | edit source]
Spam is flooding the internet with many copies of the same message. Most spam is derived from commercial advertising.
You can obtain spam filters that spare the hassle of junk mail, ads etc. Spam can also be called "bulk e-mail" or "junk e-mail". w:E-mail_spam
Phishing
[edit | edit source]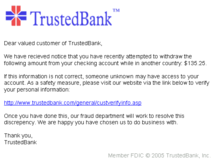
Phishing (credential harvesting) is an illegal activity where someone attempts to acquire sensitive information such as user names, passwords and credit card information. Often, users are asked to enter these details onto a website which they are stolen from. The term Phishing originates from the internet argot leetspeak. w:Phishing Phishing often employs highly advanced imitation websites which steal digital information, however they often employ simpler messages like emails requesting bank information disguised as a desperate cry for financial help or a random donation from a wealthy individual. [3]
The purpose of the fraudulent sender is to "phish" for, or entice people to share, their personal, financial, or password data. It's then used to commit crimes.
Damage by phishing
[edit | edit source]A survey has shown that phishing scams not only hurt consumers, but also the brands hijacked by the criminals to carry out their attacks. Phishing attacks are having a terrible effect on brands their reputation. In one survey 42 % claimed their trust in their brand would be damaged by a phishing attack, even though the scam had nothing to do with it. [4]
Only 26% of people see it as the consumers responsibility to protect themselves, most others blame their internet service provider for not protecting them. [5]
evil twin attack (wifi-phishing)
[edit | edit source]The next level of phishing, evil twin attack (wifi-phishing) is someone who has set up a spot near your home network - and then he/she logs onto your wireless network in order to steal your private or personal information as you send it to a secure website.
pharm
[edit | edit source]Software that's planted on a computer; redirects to impostor web page even though you type in the right URL. You can protect yourself against it by going to websites that contain https not http.
Webjack
[edit | edit source]To use fraudulent means, which allows the individual to assume the ownership of a Web site domain name belonging to another individual or groups of people. Hackers hijacking legitimate Web pages and redirecting users to their own website (usually pornography or gambling). [6]
Cyber Villains
[edit | edit source]Hacker
[edit | edit source]
The term "Hacker" originated in the 1960's, meaning simply a computer programmer. Recently, they have gotten a bad reputation, and are now commonly thought of as being malicious. [7]
Hackers are individuals who want to learn the different program languages and computer systems. Hackers are also individuals who gain unauthorized access to computers and/or networks.
There are often two types of hackers: Black-hats or White-hats.
Hackers generally particpate in these activities to create challanges for themselves, and usually there is no financial gain.
Cracker
[edit | edit source]Crackers are hackers who break into computers and networks for corrupt purposes. They can do major damage. There are four different classes of crackers: Script kiddies, hacktivists, black-hat hackers and cyberterrorists.
Examples: Pirate software, steal people’s credit card info, obtain information private information, shut down hardware, alter/destroy data. [txt359]
Crackers differ from Hackers based on the intent and motive behind their actions, crackers seek financial or other monetary gains
Hacktivists
[edit | edit source]"Hacker Activists" are people with a politically or socially motivated purpose who break into a computer system. For example, someone, who after breaking in, leaves a political or social viewpoint/opinion on the homepage of a website to express a position or practice they oppose.
Armed with what may become one of the most important weapons in the struggle for human rights - computer code - the "hactivists" are trying to give activists electronic ways to circumvent government surveillance and information management. [8]
Early in 2002, the Chinese government shut down accessibility to Google. It took 'Hactivists' less than one day to reopen it.
Cyberterrorism
[edit | edit source]Cyber-terrorism is the leveraging of a target's computers and information technology, particularly via the Internet, to cause physical, real-world harm or severe disruption of infrastructure. As the Internet continues to expand, and computer systems continue to be assigned more responsibility while becoming more and more complex and interdependent, sabotage or terrorism via cyberspace may become a more serious threat.Individuals or groups can use the anonymity afforded by cyberspace to threaten citizens, specific groups (i.e. with membership based on ethnicity or belief), communities and entire countries, without the inherent threat of capture, injury, or death to the attacker that being physically present would bring. It could be defined as the use of information technology by terrorist groups and individuals to further their agenda. This can include use of information technology to organize and execute attacks against networks, computer systems and telecommunications infrastructures, or for exchanging information or making threats electronically.
Cyberterrorism can have a serious large-scale influence on significant numbers of people. It can weaken countries' economy greatly, thereby stripping the it of its resources and making it more vulnerable to military attack. Cyberterror can also affect internet-based businesses. Like brick and mortar retailers and service providers, most websites that produce income (whether by advertising, monetary exchange for goods or paid services) could stand to lose money in the event of downtime created by cyber criminals.
w:Cyber-terrorism#Examples_of_Cyber-Terrorism
Cyber Fraud
[edit | edit source]Cyber Fraud is a type of social engineering attack where the victim is led to believe to give a fraudster a sum of money. This could be in the form of creating a website that claims to be a social organization that accepts donations that would be given to the poor, while in fact the money would directly go to the fraudster's pocket (many cyber frauds are much more sophisticated than this).
Protection
[edit | edit source]Cybercrime Treaty Gains Momentum
[edit | edit source]The number of countries that will adopt the only international treaty concerning cybercrime is going to almost double this year. 22 countries have ratified the treaty, but they hope at least 40 will adopt the treaty by Feb. 2009. 43 countries have so far signed the convention, 21 have ratified it and 22 have put the treaty into force. The convention is supposed to help prosecute cybercrime and increase cooperation of law enforcement agencies. The slow pace of getting countries to implement the treaty is from legal and legislative complexities. (http://www.pcworld.com/article/id,144017-c,internetlegalissues/article.html)
Follow this link for a picture of "Cybercrime treaty gets green light" (news.bbc.co.uk/1/low/sci/tech/1651381.stm)
Online gaming
[edit | edit source]The topic of online gaming legislation is really hot in United States and Canada. A french group is proposing an online gaming guidelines to monitor the process. This would be similar to the U.S. act of "unlawful internet gambling enforcement act of 2006". This U.S. law makes it illegal for banks and credit card companies to transfer funds from U.S. customers to online gambling sites. It make it very difficult for Americans to deposit cash in online gambling accounts. We do not have a similar law in place in Canada. That is the reason for this French group to be proposing the guidelines.
internet rights forum
[edit | edit source]The internet is booming everywhere. In order to protect minors in getting in wrong sites we need to have an agreement. In the future, the internet rights forum has plans to create a website for the parents and teachers to explain in simple terms for a non-players what online games are about and what risks they can pose.
Online Banking Security Products
[edit | edit source]Security products using behavioral analysis monitor how the users are interacting with the system. This makes it unlikely for hackers to go through different accounts without being detected. [9]
Antivirus
[edit | edit source]Scans primary and secondary storage devices such as a hard drive, floppy drive,or main memory to try to find viruses, quarantine them and destroy them. Ensuring you have up to date antivirus software installed on your computer is a very important component of personal IT security.
It works in 2 ways: 1. It scans files to look for known viruses to compare to a virus dictionary. 2. It analyzes suspicious behavior of computer programs
Firewall
[edit | edit source]A system (either software of hardware) that protects the computer from a intruders. - A hardware firewall is needed if you have more than one computer connected to the internet. If there is just one computer, a software firewall will do.
The firewall monitors all internet and other network activity, looking for suspicious data and preventing unauthorized access.[ txt 360 ], moreover, the firewall can be set at different trust levels to permit and deny certain applications/programs. (wikipedia, 2007)
Firewall itself is useless unless configured properly, it merely guards the doors, if you give him the proper list of invited guests, the firewall will allow entrance.
A firewall's function within a network is similar to firewalls with fire doors in building construction. In the former case, it is used to prevent network intrusion to the private network. In the latter case, it is intended to contain and delay structural fire from spreading to adjacent structures.
Without proper configuration, a firewall can often become worthless. Standard security practices dictate a "default-deny" firewall ruleset, in which the only network connections which are allowed are the ones that have been explicitly allowed. Unfortunately, such a configuration requires detailed understanding of the network applications and endpoints required for the organization's day-to-day operation. Many businesses lack such understanding, and therefore implement a "default-allow" ruleset, in which all traffic is allowed unless it has been specifically blocked. This configuration makes inadvertent network connections and system compromise much more likely.(http://en.wikipedia.org/wiki/Firewall_(networking))
Encryption
[edit | edit source]Encryption is the process of turning readable data into a form of unreadable data in order to prevent access that is not authorized.
Able to use mathematical concepts to create coded messages that difficult or even virtually impossible to break. [ txt 353 ]
All encryptions can be broken given enough time. The number of combination and the level of encryption complexity is key to a good encryption.
authentication
[edit | edit source]Password
[edit | edit source]
A password or watchword is a form of authentication used to guard or control a "resource" (usually used to protect electronic data). Despite the name, a password is usually an alphanumeric (letters and numbers) phrase entered to grant a user access to data that he/she is only permitted access (such as mobile phones, ATM's, computer operating systems, etc.). A password could be better described as a "passphrase". A password with numbers could be better described as a "passcode".
Passwords have been around since ancient Roman times. Guards or sentries protecting a location would challenge for a password. Access was only granted by those that knew the password.
A good password should be at least 7 characters[10], containing both letters and numbers, thus making the password more difficult to guess.
A good password is one that's hard to guess, yet easy to remember. No password is perfect, they can all be decrypted if given enough time. However, as the password encryption increase in size, the possible combination increases and makes it more difficult to break.
Biometrics
[edit | edit source]
Biometrics is the science of measuring of human physical or behavioral characteristics. It is used to identify and compare some specific people’s characteristics such as voice, fingerprints, hand geometry, eye or facial characteristics. Biometric history indicates that the science did not originate at a single place. People all over the world were using the basics for mainly identifying individuals from each other. We'll explain about biometric history in brief over the next few paragraphs.
The history of biometrics dates back to a long time. Possibly the most primary known instance of biometrics in practice was a form of finger printing being used in China in the 14th century, as reported by explorer Joao de Barros.
Barros wrote that the Chinese merchants were stamping children's palm prints and footprints on paper with ink so as to differentiate the young children from one another. This is one of the most primitive known cases of biometrics in use and is still being used today.
Apart from its Chinese genesis, use of biometrics was also noted elsewhere in the world. Up until the late 1800s, identification largely relied upon "photographic memory". In the 1890s, an anthropologist and police desk clerk in Paris, Alphonse Bertillon, decided to fix the problem of identifying convicted criminals and turned biometrics into a distinct field of study.
Bertillon developed a technique of multiple body measurements which later got named after him - Bertillonage. His method was then used by police authorities throughout the world, until it quickly faded when it was discovered that some people shared the same measurements and based on the measurements alone, two people could get treated as one.
After the failure of Bertillonage, the police started using finger printing, which was developed by Richard Edward Henry of Scotland Yard, essentially reverting to the same methods used by the Chinese for years. (which still is going strong !)
Biometric history in the recent past (three decades) has seen drastic advancements and the technology has moved from a single method (fingerprinting) to more than ten prudent methods. Companies involved with new methods have grown into the hundreds and continue to improve their methods as the technology available to them also advances. Prices for the harware required continue to fall making systems more feasible for low and mid-level budgets and thus making this more adaptable in small businesses and even households.
As the industry grows however, so does the public concern over privacy issues. Laws and regulations continue to be drafted and standards are beginning to be developed. While no other biometric has yet reached the breadth of use of fingerprinting, some are beginning to be used in both legal and business areas. http://www.questbiometrics.com
The National Biometric Security Project (NBSP) Enterprise is an independent, nonprofit organization created to increase national security and personal identity protection by enhancing identity assurance through biometrics. To reflect its expanded biometric application services, the NBSP Enterprise recently re-established its Test, Research and Data Center under the new name Biometric Services International, LLC (BSI). Located in Morgantown, West Virginia, BSI is a wholly owned, non-profit subsidiary of NBSP and is the only laboratory, exclusively focused on biometrics, to achieve the coveted ISO/IEC 17025:2005 accreditation for testing. http://www.nationalbiometric.org/
Palm/finger print
[edit | edit source]palm/finger print scanning is a unique way to protect your privacy. You run your finger across a window or sensor to identify yourself. Microsoft offers finger print readers with its Windows XP.
Iris/face
[edit | edit source]Iris/ face scans are very reliable identifiers. Each individual person has different eyes and face shape, making this type of scan very effective. These types of scans are used in high security situations such as immigration controls, federal buildings etc.
Voice recognition
[edit | edit source]A systems that extract features from speech patterns in order to recognize someones voice which is then digitalized and stored.
DNA
[edit | edit source]A system which recognizes someones personal DNA through scientific analysis to differentiate or determine that person for security reasons. Since DNA is very individual, it's proven to be extremely secure.
Mistakes
[edit | edit source]Hardware
[edit | edit source]Line down
[edit | edit source]Also known as "Data Down" or loss of data Prevention - using various backup methods to ensure data is safe
- disk redundancy - use of multiple hard drives to ensure data safety
Power Failure
[edit | edit source]
A power failure, also known as power cut, power loss, or blackout, is the loss of the electricity supply to an area. Uninterrupted power supplies (UPS) are high end power generating or backup power systems which don't allow a break in power.
Pentium Bug
[edit | edit source]The Pentium bug has the potential to crash Pentium computers and could be used for sabotage. The bug is apparently coded as a single illegal instruction and not something that would be deliberately coded into a software program. [11]
A bug in Intel's original Pentium floating point unit. The Bug was disclosed by Thomas Nicely. Affects Pentium's with a clock processor speed of at least 120 MHz is new enough not to have this bug. w:Pentium_bug
Source: http://www.news.com/2100-1001-205144.html
Related Links
[edit | edit source]Software bugs
[edit | edit source]
A software bug (or just "bug") is an error, flaw or mistake in a computer program that prevents it from behaving as intended (for example: producing an incorrect result). Most bugs are from mistakes made by people in the program's source code or it's design. Some are from compliers producing incorrect codes. Y2K bug is the most famous example of a software bug. w:Computer_bug#Etymology
Another famous software bug was found in the world famous video game POKEMON, the Missing bug allowed the gamer to surf around an island and receive free items for doing so w:Computer_bug#Etymology
The original bug was actually a moth that was caught between relays.
Bugs are a major concern as it opens up opportunities for intender to exploit those bugs. Bugs are countered with updates and patches released by the software company to address those issues. That's why it's important to keep your OS up to date. Serious bugs can cause programs to crash or freeze leading to a denial of service. (http://en.wikipedia.org/wiki/Computer_bug)
The Excel Bug--- Changes numbers to a binary format.
heisenbug-is a computer bug that disapper of alter its characteristic when it is research
Course Navigation
| << Previous - Networks | Next - Internet >> |
|---|



