Data Networking/Spring 2015/GROUP 1
Project Objective
[edit | edit source]To build a robust, secure, dynamic and intelligent network consisting of a DNS server, DHCP server, Web server with firewall and a client for a start-up company situated in Boston.
Project Team members
[edit | edit source]Raveena Ovalekar
Ritesh Kurapati
Venkata Anupama Ghantasala
Hardik Shah
Network elements
[edit | edit source]Implemented demo network consists of following elements:
- DHCP
- DNS
- WEB SERVER AND FIREWALL
Dynamic Host Configuration Protocol (DHCP)
[edit | edit source]DHCP is a client/server protocol which dynamically assigns IP addresses to clients connected to the network along with other network information such as DNS IP address, default gateway etc. It lets network administrator to centrally manage and allocate IP addresses within the network.
Behavior of the protocol
[edit | edit source]It is a client-server protocol; which uses UDP at port 67. The server dynamically assigns IP addresses, subnet mask and gateways to clients from a pool of IP addresses given to it.
Signaling
[edit | edit source]Following steps taken place in a DHCP scenario:
- First, all newly entered host have to locate DHCP server. For that, client sends a discovery request with client id 0.0.0.0 and destination address of 255.255.255.255
- When DHCP server receives a discovery request from client it sends DHCP offer message with valid subnet IP addresses in response.
- Newly arrived client will choose one offer from a number of available offers from different DHCP servers and send request to that particular server.
- That DHCP server will assign the IP address to the client and send an acknowledgement to the client.
DHCP Configuration
[edit | edit source]Most widely used DHCP servers are
- Windows DHCP server
- ISC-DHCP server
We have used ISC-DHCP as it is open source software; which can be freely run on Linux machine and it’s mostly matches its performance environment. Following commands are used to implement DHCP server on ubuntu Linux machine.
1. Update package list
sudo apt-get update
2. Install DHCP server
sudo apt-get install isc-dhcp-server -y
3. Make changes into DHCP configuration file
sudo nano /etc/dhcp/dhcpd.conf
Following changes are made in DHCP file:
- While inspecting the dhcpd.conf file locate simple subnet configuration
- Here, mention Subnet mask, Gateway router, leasing address range for subnet, broadcast address and Default and Max lease time as per your network need
4. Configure static IP addresses for Web server and DNS server (as we don’t want DHCP to allocate dynamic IP addresses to these everytime)
sudo nano /etc/dhcp/dhcpd.conf
After doing all changes the DHCP configuration file will look like this.
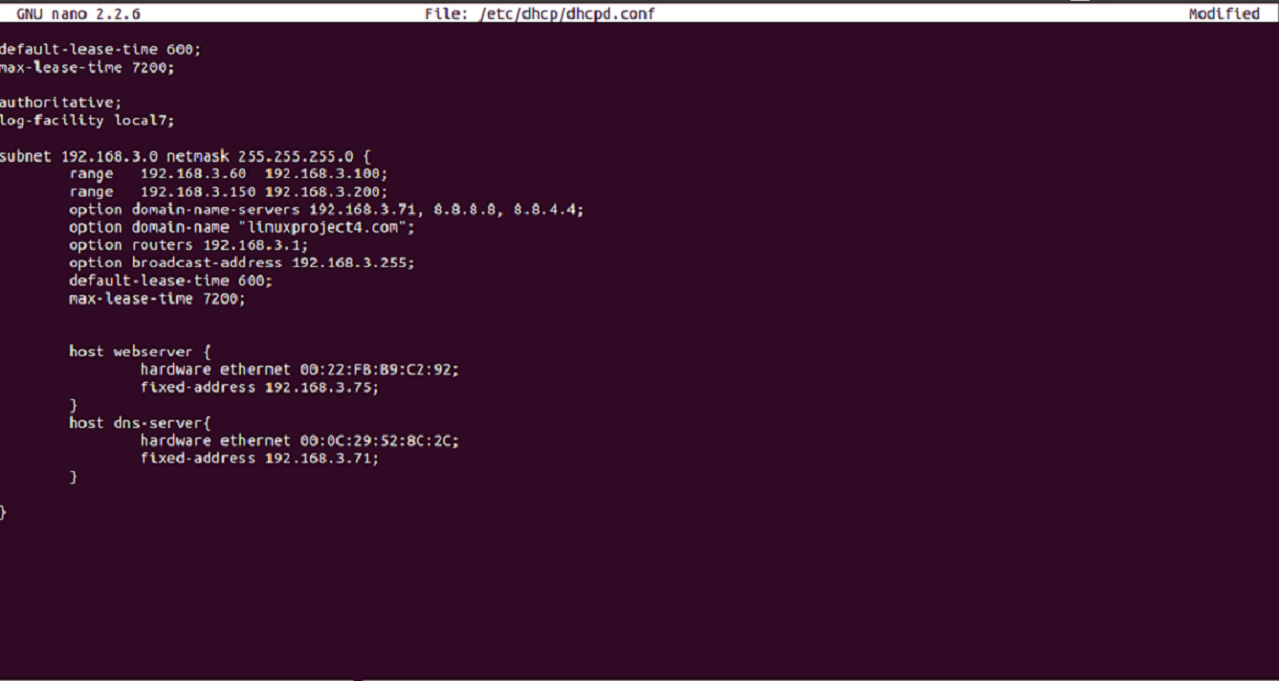
5. Restart DHCP server to apply the changes.
sudo service isc-dhcp-server restart
After entering this command in terminal; the server must be in ok/started state, otherwise recheck the dhcpd.conf file.
Testing
[edit | edit source]1. DHCP leasing: - the leases on the DHCP server and the IP addresses that has been leased to the client can be verified by using the following command.
sudo tail /var/lib/dhcp/dhcpd.leases
2. DHCP LOG: - the log output of DHCP can be verified using this command.
sudo tail –f /var/log/syslog
Domain Name System (DNS)
[edit | edit source]The Domain Name System is a hierarchical database, its responsibility is to provide name against each public domain IP address and vice –versa for websites on Internet. It is an overhead application layer protocol. It is defined by RFC 1034 & RFC 1035.
Behaviour of Protocol
[edit | edit source]DNS is a client-server type application layer protocol which uses UDP port 53. DNS client requests host mapping with a DNS request packet and the DNS server fetches the corresponding record, encapsulates it in a reply packet and sends it over UDP.
DNS Server
[edit | edit source]The authoritative name server of a company holds the records for its web servers, mail servers and canonical names of the servers. These records are configured in the DNS server by registrars certified by Internet Corporation for Assigned Names and Numbers (ICANN).
Signaling
[edit | edit source]Following steps are performed in DNS request-reply cycle:
1. The client sends a DNS query to the LOCAL DNS.
2. The LOCAL DNS forwards query to the ROOT server and reply will be sent to LOCAL DNS containing NS and A records of corresponding TLD server.
3. The reply will be sent to ROOT DNS server containing NS and A records of corresponding AUTHORATIVE Name Server.
4. The ROOT server will then send a query to the AUTHORITATIVE server & will forward the reply to the LOCAL server.
DNS Configuration
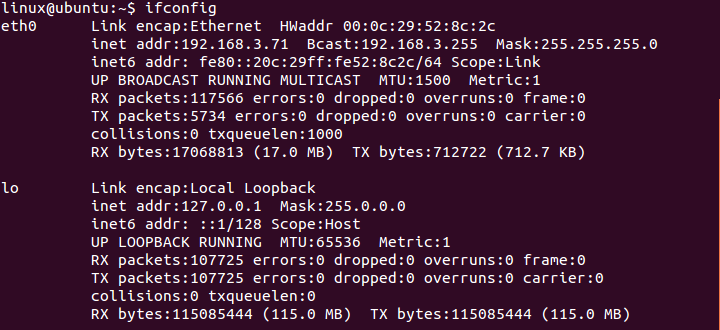
[edit | edit source]As explained in DHCP section, the DNS server is given a static IP address.
Some of the DNS software packages available are BIND, Power DNS and Posadis. Among all BIND is widely used and it fulfils all native requirement of DNS functionality like recursive, authoritative, cacheing name-server and it also contains a resolver client library. Whereas, Power DNS contains two different packages namely “PowerDNS Authoritative Server” & “PowerDNS Recursor”. The later package is more vulnerable (resolved as of now but still not recommended by network administrators). Posadis ,an open source DNS package, but it’s not maintained by any community and hence not preferable.
We have used BIND software. The latest version is Bind9.4 which supports a compile-time option for zone strategy in a variety of database formats. Moreover Bind9 also overcomes some serious security issues which were present in Bind 4 and Bind 8. Thus, Bind9 provides a robust architecture for our DNS server. Following steps are used to implement DNS server.
1.Update the package list.
sudo apt-get update
2.Install bind9.
sudo apt-get install bind9
3. Create a forward zone file.
sudo cp /etc/bind/db.local /etc/bind/db.linuxproject4.com
4. Open file /etc/bind/db.linuxproject4.com and edit it. After edition the file will look like below.
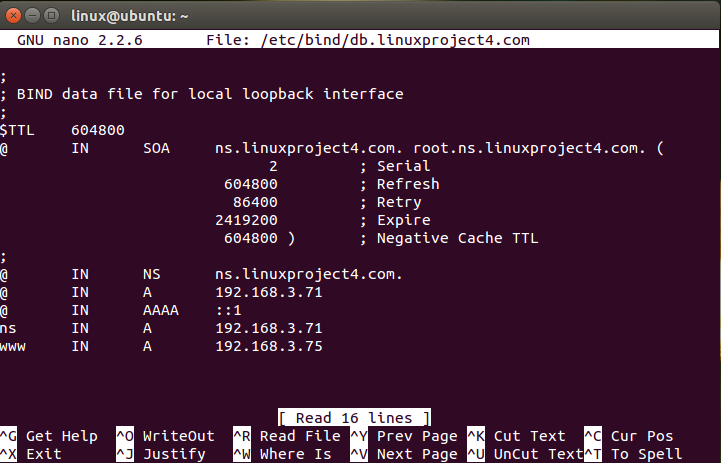
5. Create reverse zone file
sudo cp /etc/bind/db.127 /etc/bind/db.192
6. Open file /etc/bind/db.192 & edit it as below.

7. Open /etc/bind/named.conf.local file & add forward and reverse zones.

8. Change nameserver.
sudo nano /etc/resolv.conf

9. Restart Bind.
sudo service bind9 restart

Testing
[edit | edit source]We can use following commands to check whether our DNS server is working properly or not.
1. nslookup for forward zone.

2. nslookup for reverse zone.

Web Server and Firewall
[edit | edit source]Web server
[edit | edit source]Web server is an Information Technology tool which processes HTTP requests and distributes information in World Wide Web. The primary function of a web server is to store, process and deliver web pages to clients. Web server not necessarily always means to be an Internet server, large organizations have their own web servers which are used for their own Local Area Network to connect various devices within company premises. (e.g. printers, PCs, routers etc.) In any case, a server is an always ON machine & hence it must be kept at proper temperature to avoid breakdown due to overheating. A server is a heart of any network. If a server fails whole network will break down. Hence, organizations normally use a backup server in case of emergency (hot-standby configuration).
Behavior of Protocol
[edit | edit source]Hypertext Transfer Protocol (HTTP) is an Application Layer protocol most widely used in today’s Internet. It is defined in RFC 2616 (HTTP/1.1) which was modified into RFC 7230, RFC 7231, RFC 7232, RFC 7233, RFC 7234 & RFC 7235. HTTP/2 is currently under development. Default port for HTTP is 80. In a typical HTTP communication, the client sends a request a page & establishes a TCP connection between itself & server via three-way handshake process. After the connection is establishes, client requests a web page. Server sends requested HTTP page over the TCP connection. The connection is either closed or kept open after the transfer depending upon the type of connection (i.e. persistent or non-persistent).
Signaling
[edit | edit source]- The client obtains server IP address from DNS server.
- Client initiates TCP connection by sending SYN message on port 80 of the server.
- Server responds with SYN-ACK message thereby opening the port for the client to request the information.
- Client completes three-way handshake process by sending ACK message. It also requests for basic HTML page along with this.
Web server configuration
[edit | edit source]We have used Apache2 Web Server. The main reason behind choosing Apache is that it provides more compatibility with add-on modules as well as speed and flexibility in small network like the one we have created. Following commands are used to install Web Server on Linux machine.
1. Install updates
sudo apt-get update
2. Install Web server Apache2
sudo apt-get install apache2
3. Make a directory
sudo mkdir /var/www/linuxproject4.com
4. Create and edit html page
sudo nano index.html
5. Configuring 000-default.conf in Apache2. Add website folder in configuration file i.e. apache2 Edit the following file to make the web page accessible
sudo nano /etc/apache2/sites-available/000-default.conf
Add these commands in the file.
ServerAdmin webmaster@localhost ServerName linuxproject4.com DocumentRoot /var/www/linuxproject4.com
6. Secure your Apache server from DDoS
The following commands would prevent DDoS attacks on Web Server Apache
sudo apt-get -y install libapache2-mod-evasive. sudo mkdir -p /var/log/apache2/evasive sudo chown -R www-data:root /var/log/apache2/evasive sudo nano /etc/apache2/mods-available/mod-evasive.load
Testing
[edit | edit source]- Open the web browser and type web server IP address in the URL bar. Upon pressing ‘Enter’ you will get the web page of the project.
- Do the above procedure; but this time type website name i.e. ‘www.linuxproject4.com’. If you are getting the same web page that means your web server is working properly.
Firewall
[edit | edit source]A firewall is a network security system, either hardware or software based, that controls incoming and outgoing network traffic based on set of rules. We can block certain packets by configuring our firewall to certain rules.
Packages used We have used iptables and ufw packages to modify the set of rules for our Firewall.
configuration
[edit | edit source]IPTABLES: - a set of rules configured on Linux machine terminal. It has some built-in chains.
INPUT chain: - for packets coming into the machine
OUTPUT chain: - for packets generated inside and going outside of the machine.
FORWARD: - for packets routed through the local host
Following commands are used to configure Firewall.
1. Rejects ping from any host to the server.
sudo iptables -A INPUT -p icmp -j REJECT
2. Reject telnet request from a particular host to the server.
sudo iptables -A INPUT -p tcp --dport 23 -j REJECT
3. Reject FTP request from any particular host to the server.
sudo iptables -A INPUT -d 192.168.3.63 -p tcp --dport 20 -j DROP sudo iptables -A INPUT -d 192.168.3.63 -p tcp --dport 21 -j DROP
4. Accept HTTP request from a particular network
sudo ufw allow from 192.168.3.0 port 80
5. Reject HTTP request from a particular host.
sudo iptables -A INPUT -p tcp -s 192.168.3.63 --dport 80 -j REJECT
6. Enable Firewall by following command
sudo ufw enable
7. After configuring Firewall rules, restart the web server in order to apply Firewall.
Testing
[edit | edit source]1. To list all rules configured in firewall.
sudo iptables -L
2. To flush/remove the rule from iptable.
sudo iptables -F
3. To check status of ufw
sudo status ufw
Algorithm and Flow chart
[edit | edit source]Algorithm
[edit | edit source]1. A client tries to connect to the network.
2. Once the client gets connected to the network, he will send an IP address request to DHCP server.
3. If DHCP request is successful, DHCP server will reply with an IP address
Else DHCP will reply with ‘request fail.’ In this case, re-connect or contact network administrator for help.
4. Client wants to access the web page.
if domain name is correct, a request will be sent to DNS for IP address of the domain.
DNS will reply with IP address of the website.
else if DNS reply fails An error message will be displayed saying, ‘server not found.’
else if URL entered is wrong An error message will be displayed saying, ‘webpage unavailable.’
Retry
5. Client accessed the web server. Now he sends HTTP request to the server.
if the request is successful, Web page will be displayed
else Error message like ‘no data received’ will be displayed.
Retry
Flow chart
[edit | edit source]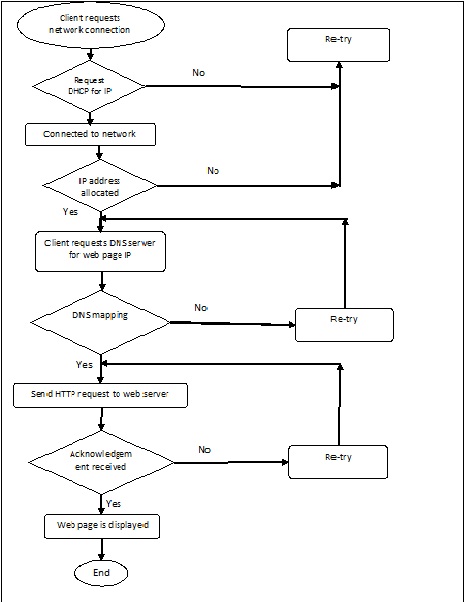
Add-ons implemented
[edit | edit source]Web Server Backup
[edit | edit source]To add redundancy to our network and make it robust, we have to implement a backup to our web server. So that if our server fails, whole network will automatically routed to the backup server & hence there will be no black out.
Configuration backup
[edit | edit source]1. Install ‘Rsync’ in both server and client
sudo apt-get install rsync
2. copy file from server to client
rsync –avzhe ssh ritesh@192.168.3.75:/var/www /var/www
3. Generate public and private key
ssh-keygen –t rsa –b 2048
4. Share public and private keys with main server
ssh-copy-id –I /root/ .ssh/id_rsa.pub ritesh@192.168.3.75
5. Setup ‘cron’ to schedule automatic backup every 60 minutes and edit the file.
crontab –e */60 * * * * rsync –avzhe ssh ritesh@192.168.3.75:/var/www /var/www/
Testing
[edit | edit source]1. Shut down the main server and try to access the web page. If webpage accessed Backup is working correctly. Else Some problem with backup.
2. Now make some changes in main server. Shut down main server & see if those changes are reflected in backup server. If changes are reflected ‘rsync’ is working. Else ‘rsync’ is not working.
Network File System (NFS)
[edit | edit source]It is a file distribution system protocol. NFS allows a client to share its content with other users on the network. In order to access the file, all clients have to mount the shared directory to make it their own directory.
Configuration
[edit | edit source]Following commands are used to install and configure NFS server as well as client. 1. Install and update packages.
sudo apt-get update
NFS server 2. Type following command to install NFS server
sudo apt-get install nfs-kernel-server
3. Make directory which will be shared with clients.
sudo mkdir /home
4. Open /etc/exports file. This is main NFS configuration file.
sudo nano /etc/exports

5. Start the service with following command.
sudo /etc/init.d/nfs-kernel-server start
NFS client 6. Install client and dependencies.
sudo apt-get install nfs-common rpcbind
7. Create a directory
sudo mkdir /chome
8. Mount the remote share directory on client’s local directory
sudo mount 192.168.3.75:/home /chome
9. Add the following line to mount the directory permanently.
sudo 192.168.3.75:/home /chome nfs rw,sync,hard,intr 0 0
Testing
[edit | edit source]1. In server, type this command to see shared directories.
sudo nano /etc/exports

2. In client, type following command to see shared directory.

File Transfer Protocol (FTP)
[edit | edit source]FTP is used to transfer files from one computer to another over TCP connection. It is a client-server based protocol and uses separate connection for control and data signals.
Configuration
[edit | edit source]Following commands are used to implement FTP. 1. Update & install FTP package.
sudo apt-get install vsftpd
2. Open file /etc/vsftpd.conf file & make following changes. Remove ‘#’ sign.
sudo nano /etc/vsftpd.conf write_enable=yes anonymous=yes
3. Restart vsftp.
sudo restart vsftpdt
4. Create some files.
cd /srv/ftp sudo touch text1 text2 sudo chmod 777 text1 text2
Testing
[edit | edit source]Write following command on client to see shared files. Enter ‘username’ and ‘password’ to logged in. Once accessed, client can make changes into the file also.
ftp 192.168.3.75
Virtual Private Network
[edit | edit source]A virtual private network extends your private network to public network like Internet.It lets the client connect to the private network and behave as if it is connected to a public network, while retaining features of private network such as functionality, security and management policies. Resources are accessed in same way as in a private network.
Configuration
[edit | edit source]1. Install packet ‘pptpd’
sudo apt-get install pptpd
2. Edit file /etc/pptpd.conf as follows
sudo nano /etc/pptpd.conf localip <VPN server IP> remoteip <Range of IPs of VPN clients>
3. Edit /etc/ppp/pptpd/options file.
sudo nano /etc/ppp/pptpd.options ms-dns 192.168.3.254
4. Set ‘user-id’ and ‘password’
sudo nano /etc/ppp/chap-secrets ritesh pptpd group1 *
Network Information Service (NIS)
[edit | edit source]This is a client-server protocol which is used to exchange system configuration data between users on a computer network. NIS contains a central directory of user & group information along with other useful data.
Configuration
[edit | edit source]1. Install nis portmap
sudo apt-get install nis portmap
2. Edit domain as well as server name and refresh the database.
sudo nano /etc/default/nis set nisserver=master
sudo nano /etc/yp.conf domain Group1Server server ritesh
sudo nano /etc/ypserv.securenets “255.255.255.0 192.168.3.*”
Refreshes the database
sudo /user/lib/yp/ypinit -m
3. For NIS client, type following command
sudo apt-get install portmap nis
4. Edit domain & server name
sudo nano /etc/passwd
5. Make following changes
Add a line +: : : : : :
sudo nano /etc/group Add a line +: : :
sudo nano /etc/shadow Add a line +: : : : : : : :
sudo nano /etc/yp.conf set the ypserver’s IP address <192.168.3.75>
After making above changes update the database in the server.
Testing
[edit | edit source]Use commands ‘yptest ypswitch’ and ‘ypcat –x’ to test NIS.
Mail Server
[edit | edit source]Mail server is responsible for receiving, sending and distributing e-mail messages from your computer to others. In Linux we call it ‘mail daemon’.
Configuration
[edit | edit source]To implement mailserver, we have used postfix mail services with webmail client squirrelmail. This configuration contains open source packages which support IMAP, SMTP and POP3. This configuration also protect against malware and spam; hence the packages fulfils the requirement of basic mailserver. To configure mailserver, following packages need to be downloaded in to the system.
sudo apt-get update sudo apt-get install bind9 dnsutils apache2 php5 postfix dovecot-common dovecot-imapd doecot-pop3d squirrelmail cd /etc/bind nano named.conf.local (add and edit forward and reverse zone for your domain) cp db.local db.hardy.home
DNS Forward zone addition

Now do ‘nslookup’.
nslookup mail.hardy.home dig mail.hardy.home
cd /etc/apache2/sites-available/ cp 000-default.conf mail.conf nano mail.conf (add and edit: ServerName and document root for squirrelmail) a2ensite mail (enabling mailsite) invoke-rc.d apache2 restart ( restart apache2 services)
dpkg-reconfigure postfix (configure postfix services with respect to your server IP and domain name)
nano /etc/squirrelmail/apache.conf (add & edit: documentroot and domain name) nano /etc/dovecot/dovecot.conf (add protocols IMAP & POP3 and mail_location)
- stopping all related services
killall named killall apache2 killall dovecot
nano /etc/network/interfaces (define ststic IP with netmask and default gateway for Mailserver)
- enabling all mail related services
invoke-rc.d bind9 restart invoke-rc.d apache2 restart invoke-rc.d postfix restart invoke-rc.d dovecot restart
- add user as per requirement of the network
Working:


Testing
[edit | edit source]1. Send/receive mail from web-client squirrelmail
2. open web browser: mail.hardy.net
3. You should get the mail page.
Working with an example
[edit | edit source]We have used all Linux machines to implement various components like DNS, DHCP, WEB SERVER. We have used 192.168.3.0/24 network with 192.168.3.1 as our default gateway and 192.168.3.255 as broadcast address.
First, all devices will be connected to the network via router. Then DHCP will allocate IP addresses to clients.
Web Server will have 192.168.3.75
DNS will have 192.168.3.71
Now, client will open his browser and try to access the web page.
DNS static IP allocation
Forward and Reverse zone lookup for DNS

DHCP static configuration
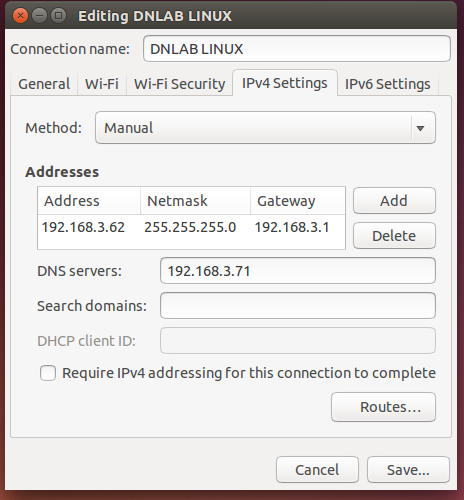
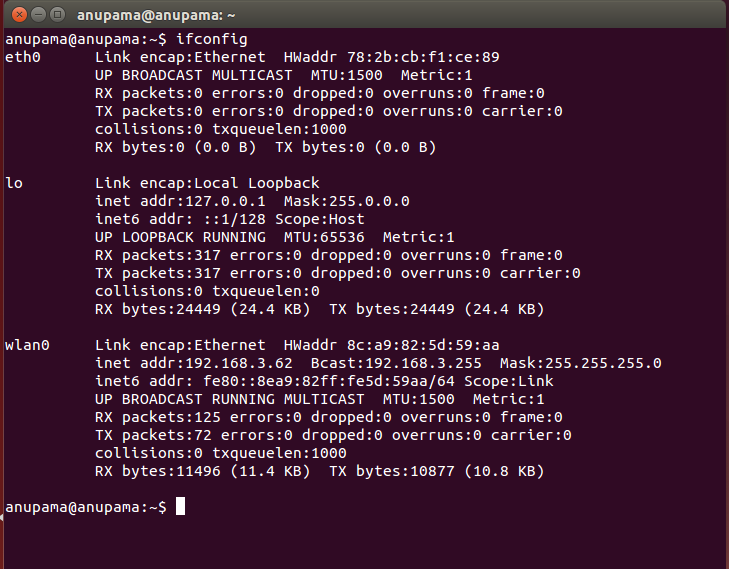
DHCP IP address checking on terminal
Checking the website www.linuxproject4.com on browser

Future Improvements
[edit | edit source]- Should support IPv6 and IPv4 simultaneously.
- More DNS servers for backup, load distribution and decentralization.
- Adding security for mail server by integrating confidentiality, integrity and more authentication options by using methods such as RSA, DES, MD5, including certificates etc.
- Adding more security in Firewall for prevention against serious external attacks.
- Expand the server capabilities to accommodate many more uses using at the same time.
References
[edit | edit source]- Computer Networking A TopDown Approach by KUROSE and ROSS
- https://help.ubuntu.com/lts/serverguide/dns-configuration.html
- https://help.ubuntu.com/community/isc-dhcp-server
- https://help.ubuntu.com/lts/serverguide/httpd.html
