Data Networking/Fall 2014/YunweiJiang
The Folks
[edit | edit source]Yunwei Jiang (Jiang.yun@husky.neu.edu)
Tianhe Wang (wang.tianh@husky.neu.edu)
Manish Reddy Bhimavarapu (bhimavarapu.m@husky.neu.edu)
Samuelraj Vibin Mohanraj Samuel (mohanrajsamuel.s@husky.neu.edu)
Motivation
[edit | edit source]The purpose of project is to create a network includes a webserver with firewall, a DNS server, a DHCP server, a NFS server, a NIS server, a VPN server. And in order to test VPN, another network with only a webserver is also built.
In this project, when a new coming client joins the network, it can be assigned IP addresses(both IPv4 and IPv6) dynamically by the DHCP server, and the user can log in with his username and password which are registered in the NIS server. When the user try to access the webserver, the DNS server will translate the domain name the user input in the browser blank into a corresponing IP address so that the certain webpage can be shown in the client brower. Since the firewall only allow data traffic from port 80 which is the port for HTTP, the user cannot ping the webserver or telnet the webserver. When testing the VPN, what we should do first is to verificate that the client cannot get access to the webserver locating in another network. After that, we should make the client connect to VPN and then try to get access to the webserver. If it works, it means that the VPN works!
Network Topology
[edit | edit source]The central network topology is Star Topology, all servers and clients are connected to the switch.
However, in the project, we use 4 physical PCs, and connected them to the switch. They may have a virtual network in the Host system if one run Virtual Machines. There are 2 type of virtual network. The one is vmNet0, auto bridged network, which bridged to Ethernet port, on link layer. Another is vmNet2, the Host-only network, which means it is a internal network between virtual machines and Host system. It not connected to any other network in any form.
Specially, the VPN server have two interfaces, one connected to the vmNet0, another connected to vmNet2. The Private Server have one interface and it connected to vmNet2. All other Virtual machines only have one interface and connected to the vmNet0.
-
Logical topology
-
Phsical topology
DHCP Server
[edit | edit source]Understanding the Protocol
[edit | edit source]Behavior of the protocol
[edit | edit source]Dynamic Host Configuration Protocol (DHCP) is a client/server protocol that automatically provides an Internet Protocol (IP) host with its IP address and other related configuration information such as the subnet mask and default gateway. This TCP/IP standard reduces the complexity and administrative overhead of managing network client IPv4 / IPv6 addresses and other configuration parameters.
Signaling [1]
[edit | edit source]DHCP servers and DHCP clients communicate through a series of DHCP messages. To obtain a lease, the DHCP client initiates a conversation with a DHCP server using a series of these DHCP messages.
The common messages that can be sent between DHCP clients and servers are as follows:
DHCPDiscover Broadcast by a DHCP client when it first attempts to connect to the network. This message requests IP address information from a DHCP server.
DHCPOffer Broadcast by each DHCP server that receives the client DHCP Discover message and has an IP address configuration to offer to the client. The DHCPOffer message contains an unleased IP address and additional TCP/IP configuration information, such as the subnet mask and default gateway.
DHCPRequest Broadcast by a DHCP client after it selects a DHCPOffer. The DHCPRequest message contains the IP address from the DHCPOffer that it selected. If the client is renewing or rebinding to a previous lease, this packet might be unicast directly to the server.
DHCPAck Broadcast by a DHCP server to a DHCP client acknowledging the DHCPRequest message. Upon receipt of the DHCPAck, the client can use the leased IP address to participate in the TCP/IP network and complete its system startup. This message is typically broadcast, because the DHCP client does not officially have an IP address that it can use at this point.
DHCPNack, DHCPDecline, DHCPRelease and DHCPInform are the other common messages used by the server and client.

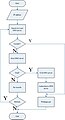
Flow Chat of DHCP
[edit | edit source]-
DHCP Flow Chat
The Requirements
[edit | edit source]1. A DHCP server that has installed isc-dhcp-server and isc-dhcp6-server (will manually create after)
2. A client.
Steps to perform the installation and configuration [2]
[edit | edit source]Install isc-dhcp-server
[edit | edit source]sudo apt-get install isc-dhcp-server
Edit the configuration file
[edit | edit source]sudo gedit /etc/dhcp/dhcpd.conf
Add these lines into it.
default-lease-time 600;
max-lease-time 7200;
option subnet-mask 255.255.255.0;
option broadcast-address 192.168.5.255;
option routers 192.168.5.1;
option domain-name-servers 192.168.5.6;
option domain-name "mvrs.com";
subnet 192.168.5.0 netmask 255.255.255.0 {
range 192.168.5.15 192.168.5.40;
}
<nowiki>
==== Restart the services ====
<nowiki>
sudo isc-dhcp-server start
or
sudo isc-dhcp-server restart
<nowiki>
=== Implementing PXE boot support<ref>http://askubuntu.com/questions/412574/pxe-boot-server-installation-steps-in-ubuntu-server-vm</ref><ref>https://wiki.debian.org/PXEBootInstall#Activate_PXE_boot</ref> ===
In order to support PXE boot, the server should provide TFTP service which can hand out the file when client needs to boot.
==== Install required packages ====
<nowiki>sudo apt-get install openbsd-inetd tftpd-hpa
Configure inetd.conf
[edit | edit source]sudo gedit /etc/inetd.conf
Add this line into it, insert it below "#BOOT:......" without any '#' as the beginning of the line.
tftp dgram udp wait root /usr/sbin/in.tftpd /usr/sbin/in.tftpd -s /var/lib/tftpboot
Get PXE boot images
[edit | edit source]Get Ubuntu PXE boot environment file from internet, of course you can choose other PXE boot images.
You can get Ubuntu installer pxelinux from here:
http://archive.ubuntu.com/ubuntu/dists/utopic/main/installer-amd64/current/images/netboot/
You can also use FTP tool to get it. You should download all belongings from it and do not change the folder's order. Then, Copy it to /var/lib/tftpboot/
It likes the picture shows above.
Then, change the access permissions of these files.
sudo chmod +444 /var/lib/tftpboot/*
Restart the services.
[edit | edit source]sudo service tftpd-hpa restart sudo service openbsd-inetd restart
Testing
[edit | edit source]When testing DHCP server, what we need to do is just to see whether our client can get a IP address in a dynamical way.
We also can test the DHCP server and PXE boot at the same time.
Open a computer which support PXE boot. You may need press F12 button during the diagnose/POST screen, then entering the PXE boot.
It looks like following scenario.
-
PXE boot start up screen
After it has been successfully allocated IP address from the DHCP server, the client will run the pxelinux.0, which is download from the TFTP server.
-
Linux_tftpboot_start screen
When it loaded whole image from the TFTP server, it will be booted. Then, there is no different between regular computer booting.
-
Linux_tftpboot_success screen
DNS Server
[edit | edit source]Understanding the Protocol
[edit | edit source]DNS is a protocol within the set of standards for how computers exchange data on the Internet and on many private networks, known as the TCP/IP protocol suite. Its basic job is to turn a user-friendly domain name into an Internet Protocol (IP) address like 70.42.251.42 that computers use to identify each other on the network. Whether you're accessing a Web site or sending e-mail, your computer uses a DNS server to look up the domain name you're trying to access. The proper term for this process is DNS name resolution, and you would say that the DNS server resolves the domain name to the IP address.
Signaling
[edit | edit source][3]
DNS queries can be sent from a DNS client (resolver) to a DNS server, or between two DNS servers.
A DNS query is merely a request for DNS resource records of a specified resource record type with a specified DNS name. For example, a DNS query can request all resource records of host with a specified DNS name.
A recursive query forces a DNS server to respond to a request with either a failure or a successful response. DNS clients (resolvers) typically make recursive queries. With a recursive query, the DNS server must contact any other DNS servers it needs to resolve the request. When it receives a successful response from the other DNS server(s), it then sends a response to the DNS client. The recursive query is the typical query type used by a resolver querying a DNS server and by a DNS server querying its forwarder, which is another DNS server configured to handle requests forwarded to it.
An iterative query is one in which the DNS server is expected to respond with the best local information it has, based on what the DNS server knows from local zone files or from caching. It may have to query a number of outside DNS servers in an attempt to resolve the name.
The DNS Client service queries the DNS servers in the following order:
• The DNS Client service sends the name query to the first DNS server on the preferred adapter’s list of DNS servers and waits one second for a response.
• If the DNS Client service does not receive a response from the first DNS server within one second, it sends the name query to the first DNS servers on all adapters that are still under consideration and waits two seconds for a response.
• If the DNS Client service does not receive a response from any DNS server within two seconds, the DNS Client service sends the query to all DNS servers on all adapters that are still under consideration and waits another two seconds for a response.
• If the DNS Client service still does not receive a response from any DNS server, it sends the name query to all DNS servers on all adapters that are still under consideration and waits four seconds for a response.
• If it the DNS Client service does not receive a response from any DNS server, the DNS client sends the query to all DNS servers on all adapters that are still under consideration and waits eight seconds for a response.
• If the DNS Client service receives a positive response, it stops querying for the name, adds the response to the cache and returns the response to the client.
• If the DNS Client service has not received a response from any server within eight seconds, the DNS Client service responds with a time-out. Also, if it has not received a response from any DNS server on a specified adapter, then for the next 30 seconds, the DNS Client service responds to all queries destined for servers on that adapter with a time-out and does not query those servers. Only computers running Windows 2000 or Windows Server 2003 return this time-out.
• If at any point the DNS Client service receives a negative response from a server, it removes every server on that adapter from consideration during this search. For example, if in step 2, the first server on Alternate Adapter A gave a negative response, the DNS Client service would not send the query to any other server on the list for Alternate Adapter A.
The DNS Client service keeps track of which servers answer name queries more quickly, and it moves servers up or down on the list based on how quickly they reply to name queries.
Heirarchy
[edit | edit source]-
DNS Server Hierarchy
Flow Chat
[edit | edit source]-
DNS Flow Chat
Steps to perform the setup / Installation[4]
[edit | edit source]1. Update and Upgrade the packages
sudo apt-get update sudo apt-get upgrade
2. Choose a preferred editor to work on. gedit is pre-installed in most of the Ubuntu versions. Vi editor is also an option.
3. Install the service BIND9 (Berkeley Internet Name Domain)
sudo apt-get install bind9
4. Files that need to be configured inside /etc/bind:
gedit /etc/bind/ named.conf.local
5. Edit the file, add the following: This is our domain name and reverse area
zone "physicsboy.org"{
type master;
file "/etc/bind/db.physicsboy.org";
};
zone "19.68.10.in-addr.arpa"{
type master;
file "/etc/bind/db.10.68.19";
};
5. Static DNS Record This means the DNS server is responsible for such domain names Edit the file. The file name needed to be in this order: db.yourdomain, for example gedit /etc/bind/db.physicsboy.org
put following record in it
;
; BIND data file for dev sites
;
$TTL 604800
@ IN SOA physicsboy.org. root.physicsboy.org. (
1 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS ns.physicsboy.org.
IN MX 10 mail.physicsboy.org.
IN A 10.68.19.61
ns IN A 10.68.19.61
IN AAAA 2001:1988:709::1000
www IN CNAME w1.physicsboy.org.
w1 IN A 10.68.19.62
IN AAAA 2001:1988:709::1:1000
w2 IN A 10.68.19.63
IN AAAA 2001:1988:709::1:1001
mail IN A 10.68.19.64
nis IN A 10.68.19.69
ubuntu IN A 10.68.19.69
vpn IN A 10.68.19.66
vpn2 IN A 10.68.19.67
prv IN CNAME private.physicsboy.org.
private IN A 192.168.182.129
;
Testing
[edit | edit source]Try to use the command nslookup on the DNS server. Another choice is to use the client to get access to the webserver, and type a domain name, such as www.physicsboy.org. If you can get the webpage, it means that the DNS sever is done!
NIS Server / Client
[edit | edit source]Understanding the Protocol
[edit | edit source]NIS is the abbreviation of Network Information System which is a directory service protocol used to manage configuration files which are related to computer system management, such as account, passwords, hostname, group, etc. Usually, NIS can be called as "Yellow Page". The service was developed by SUN.
The Requirements
[edit | edit source]1. Hardware: A configured NIS server and a configured NIS client.
2. Software: The server and the client should install NIS and portmap(in Ubuntu 14.04, portmap has been abolished and we should use rpcbind instead).
3. The NIS server should be turned on.
Steps to perform the setup / installation
[edit | edit source]1. Server Configuration
[edit | edit source]1) Install rpcbind:
sudo apt-get install rpcbind
In previous versions of Ubuntu, wheat should be installed is portmap service, however, in Ubuntu 14.04, we should choose rpcbind because portmap has stopped being used.
2) Update rpcbind defaults:
sudo update-rc.d rpcbind defaults 10
3) Install NIS:
sudo apt-get install nis
When nis service is installed in your host for the first time, you will be asked to input a NIS domain, and usually, the NIS domain should be your organization's domain name.
4)Edit /etc/defaults/nis:
sudo vi /etc/defaults/nis
When editting the file, only 2 lines need to be updated, the default contents of the 2 lines are:
NISSERVER=true NISCLIENT=true
Here, we should update the 2 lines to
NISSERVER=Master NISCLIENT=false
This modification is to make your host be the NIS server.
5) Edit /etc/ypserv.securenets: sudo vi /etc/ypserv.securenets
In this file, only 1 line need to be update,the original line is:
#This line gives access to everybody. PLEASE ADJUST! 255.0.0.0 127.0.0.0
Here we should update the Network ID to your organization's ID, and the results in this project is:
#This line gives access to everybody. PLEASE ADJUST! 255.255.255.0 10.68.19.0
This modification is to determine the subnet that NIS server works for.
6) Edit /var/yp/makefile:
sudo vi /var/yp/Makefil
Modify the line from
”ALL=passwd group hosts rpc services netid protocols netgrp”
to
“ALL=passwd shadow group hosts rpc services netid protocols netgrp”
7) Restart the service:
sudo service rpcbind restart
8) Invoke /usr/lib/yp/ypinit -m:
sudo /usr/lib/yp/ypinit -m
9) Add users and group to be used by NIS clients throughout the network to the NIS server:
sudo useradd –d /home/username –m username
For example,
sudo useradd –d /home/user1 –m user1
10) Set the passwords for all these new users: sudo passwd username. For example, sudo passwd user1.
11) Compile new uses, groups and passwords into the NIS database:
cd /var/yp/ sudo make
2. Client Configuration
[edit | edit source]1) Install rpcbind:
sudo apt-get install rpcbind
2) Update rpcbind:
sudo update-rc.d rpcbind defaults 10
3) Install NIS:
sudo apt-get install nis
4) Edit /etc/hosts:
sudo vi /etc/hosts
Here we need to append our NIS server's IP address and hostname as well as the domain name we set for the NIS server before to the file.
5) Edit /etc/yp.conf:
sudo vi /etc/yp.conf
Here we need to append our NIS server's domain name to the file.
6) Edit /etc/nsswitch.conf:
sudo vi /etc/nsswitch.conf
Update the content
passwd: compat group: compat shadow: compat
to
passwd: nis compat group: nis compat shadow: nis compat
7) Modify the permission of the default /home folder:
sudo chmod 777 /home
8) Reboot the client:
sudo reboot
3. NFS Configuration
[edit | edit source]After completing the configuration of NIS server and NIS client, we need to test whether the two hosts can work well. During the test, the users registered in the NIS server may not find their /Home directory. In order to solve the problem, we need to configure NFS on both the NIS server and NIS client. We will give more details about configuring the NFS service later.
Testing
[edit | edit source]When the NIS is on, we can log in with the identification of user1/user2/user3, however, if the NIS server is off, none of these users can log in on the NIS client.
Web Server
[edit | edit source]Understanding the Protocol
[edit | edit source]A web server is a computer system that processes requests via HTTP, the basic network protocol used to distribute information on the World Wide Web. The primary function is to serve web pages or store information. Every web server has an IP address and a domain name if possible. Any computer can be turned into a Web server by installing server software and connecting the machine to the Internet. Apache Webserver is the most widely used webserver. And for secure consider, we can also implement SSL.
The Requirements
[edit | edit source]The requirements for webserver is quite simple. 1. A webserver installing Apache2 and openssl; 2. A host which can get access to the webserver.
== Steps to perform the setup / installation ==[5]
1. Install Apache2
sudo apt-get install apache2
2. Edit the configuration file of the server
sudo vim /var/www/index.html
3. Create web pages using HTML and save them using filename.html Web pages are saved at /var/www
4. To edit HTML web page give
cd /var/www$ sudo nano filename.html
To view the web page give localhost/filename.html or /var/www/filename.html in the web browser.
5. Web Server stop/restart
a) To stop the web server, enter
sudo /etc/init.d/apache2 stop
b) To restart the web server give
sudo /etc/init.d/apache2 restart
6. Enable SSL
sudo a2enmod ssl
7. Create a folder to save the key and certification
sudo mkdir /etc/apache2/newssl
8. To generate the key and certification
sudo openssl req –x509 –nodes –days 365 –newkey rsa:2048 –keyout /etc/apache2/newssl/owncloud.key –out /etc/apache2/newssl/owncloud.crt
After executing the command, you will see such words on your screen:
Country Name (2 letter code) [AU]: State or Province Name (full name) [Some-State]: QLD Locality Name (eg, city) []: Organization Name (eg, company) [Internet Widgits Pty Ltd]: Organization Unit Name (eg, section) []: Common Name (e.g. Server FQDN or YOUR name) []: Email Address []:
Usually, we can keep all lines but “Common Name” default, and we can set “Common Name” as our organization name or our IP address.
9. Set up the certificate by editing the file /etc/apache2/sites-available/default-ssl.conf.
sudo vi /etc/apache2/sites-available/default-ssl.conf
10. Active the website created
sudo a2ensite default-ssl.conf
Testing
[edit | edit source]1. To test Apache, we need only open our browser and then type the IP address of the webserver to see whether the default test page of Apache will show. 2. To test SSL, we need to open our browser and then type "https://" and the IP address of the webserver to see whether the default test page of Apache will show.
NFS Server
[edit | edit source]Understanding the Protocol
[edit | edit source][6] NFS, or Network File System is one kind of file systems supported by FreeBSD. NFS allows a system share its directories and files on the network. Users and programs can access files residing in remote servers as directories and files locating in local host.
The advantages of NFS are obvious:
1. Local workstation can save hard-disk space because files can be saved on the NFS server and can be accessed through the network.
2. It's not necessary for users to have a home directory on each hosts because this directory can be placed in the NFS server which can be accessed through the network.
3. Devices like CDROM, floppy drive can be used by other hosts through the network, reducing the amount of removable devices.
The Requirements
[edit | edit source]1. A NFS server and one or more NFS clients.
2. The NFS server should install nfs-kernel-server, rpcbind.
3. The NFS client should install nfs-common, rpcbind.
Steps to perform the setup / installation
[edit | edit source]1. Server Configuration
[edit | edit source]1) Install nfs-kernel-server on the NFS server:
sudo apt-get install nfs-kernel-server rpcbind
2) Build the folder going to share:
sudo mkdir /armnfs
3) Change the permission of the folder
sudo chmod 777 /armnfs
4) Edit /etc/exports:
sudo vi /etc/exports
Here, we need to append the shared directory, /armnfs, and set the operating permission.
"*" means that all subnets can get access to the directory;
"rw" means that users can read and write the files;
"sync" means the file contents are written to RAM and ROM at the same time
Other details are no more listed here
5) Restart NFS service:
sudo service rpcbind nfs-kernel-server restart
2. Client Configuration
[edit | edit source]Here we select the webserver as the NFS client and most html files are located in the NFS server.
1) Install nfs-common and rpcbind
sudo apt-get install nfs-common rpcbind
2) Build a new subfolder in the folder /var/www/:
sudo mkdir /var/www/armnfs
After executing the command, open the browser of the webserver and type "localhost/armnfs/homepage.html" which is a html file locating in the NFS server in the browser blank, if you can get access to it, your NFS client configuration is done!
Testing
[edit | edit source]1) Test the NFS server:
sudo showmount -e
If it shows
/Export list for ubuntu: /armnfs *
It means that the NFS server has been configured successfully.
2. Test the client:
sudo mount 10.68.19.65:/armnfs /var/www/armnfs
If you want stop the connection between the NFS client and the NFS server, use the below command:
sudo umount 10.68.19.65:/armnfs /var/www/armnfs
VPN Server / Client
[edit | edit source]Understanding the Protocol
[edit | edit source]A VPN is a method of connecting to a private network by way of a public network. A Virtual Private Network, or VPN, creates an encrypted tunnel between computer (client) and the VPN (server). The VPN server must have IP addresses available in order to assign them to the VPN server's virtual interface and to VPN clients during the negotiation phase of the connection process. The IP address assigned to the VPN client is assigned to the virtual interface of the VPN client.
The Requirements
[edit | edit source]1. A client which has installed openvpn service;
2. The client must have installed the certificate geneated by the VPN server;
3. A VPN server which has installed openvpn service.
Steps to perform the setup / installation
[edit | edit source]1. Install openvpn and easy-rsa
sudo apt-get install openvpn easy-rsa
2. Certificate Authority Setup:
i. mkdir /etc/openvpn/easy-rsa/ ii. cp –r /usr/share/easy-rsa/* /etc/openvpn/easy-rsa/
3. Edit /etc/openvpn/easy-rsa/vars:
sudo vi /etc/openvpn/easy-rsa/vars
Modify the default configuration to what is shown above.
4. Generate the master Certificate Authority certificate and key:
i. cd /etc/openvpn/easy-rsa/ ii. source vars iii. ./clean-all iv. ./build-ca
5. Generate a certificate and private key for the server:
i. ./build-key-server physicsboy.org ii. ./build-dh iii. cd keys iv. cp /physicsboy.org.crt physicsboy.org.key ca.crt dh2048.pem /etc/openvpn/
6. Generate client certificates and copy it to the client in a secure way and delete it in the server:
i. cd /etc/openvpn/easy-rsa/ ii. source vars iii. ./build-key client1
7. Copying and unpacking server.conf.gz to /etc/openvpn/server.conf:
i. sudo cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz /etc/openvpn ii. sudo gzip –d /etc/openvpn/server.conf.gz
8. Edit /etc/openvpn/server.conf to make sure the following lines are pointing to the certificates and keys created in the section above:
9. Start the openvpn service:
sudo service openvpn start
10. To check if OpenVPN created a tun0 interface:
ifconfig tun0
Testing
[edit | edit source]Shutting down the VPN service, we can find that the client cannot get access to the webserver locating in another network. Then we turn on the VPN service and try to make the client access to the webserver. If the client can get the webpage, it means that the VPN is done!
=Firewall= [7]
Understanding the protocol
[edit | edit source]A firewall is a network security system that controls the incoming and outgoing network traffic based on applied rule set. A firewall establishes a barrier between a trusted, secure internal network and another network (e.g., the Internet) that is assumed not to be secure and trusted. By configuring commands on a Linux terminal, an Ubuntu machine both at the (web server end and at the client end) a set of rules are applied so that it will drop certain packets but allows rest all packets.
Steps to perform the setup / Installation
[edit | edit source]1. To show iptables configuration:
sudo iptables –L
2. Allow established sessions to receive traffic:
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
3. Allow incoming traffic on specific ports, here we only allow traffic on port 80:
iptables -A INPUT -p tcp -i eth0 --dport 80 -j ACCEPT
4. Blocking traffic:
iptables -A INPUT -j DROP
5. Insert to allow lo traffic:
iptables -I INPUT 3 -i lo -j ACCEPT
Testing
[edit | edit source]Let's shut down the firewall first, and try to ping the webserver. We will find that the webserver will give icmp response to the client. Then start the firewall, since the firewall configured here only allows HTTP request, thus no icmp can get access to the webserver. We try to ping the server, and find that no response. Buy we can still get access to the webpage. This means that our configuration for firewall works.
Testing
[edit | edit source]Because of the limited number of laptops, we have to run most of these servers on VMware. Here, we use A, B, C, D to denote different 4 laptops.
In laptop A, we install a VPN server and a webserver which belongs to network1;
In laptop B, we install a DHCP server and a DNS server;
In laptop C, we install a webserver including the firewall and SSL configuration, and s NIS server as well as a NFS server;
We take laptop D as the client, and in order to test NIS and VPN, we implement NIS client configuration and VPN client configuration on laptop D.
The test steps are simple:
1. Open all servers and client;
2. Log in with the identification registered in the NIS server, such as user1, user2, and user3.
3. Once the user log in successfully, meaning that the NIS server is configured correctly, open the browser of the client;
4. Check the IP addresses(IPv4 and IPv6) of the client;
5. Type a domain name or a IP address which can be find in the DNS server in the browser's blanket, here we can use www.physicsboy.org or 10.68.19.62.
6. Type a domain name or a IP address with a prefix "https://" which can help to prove SSL in the brower's blanket, here we can use https://www.physicsboy.org or https://10.68.19.62.
7. Visit a webpage which is not locate in the webserver but the NFS server.
8. If all above are done successfully, it means that the requirements for webserver, DNS server, DHCP server, NIS, NFS are all completed.
9. When testing the VPN part, we should first shut down the VPN service of the client, then try to get access to a webpage existing in the webserver locating in another network, and the browser will show us a error if everything is correct. Then open the VPN service of the client, and then try to access to the same webpage, if the browser displays the webpage correctly, VPN part is proved.
Future Prospects
[edit | edit source]In this project, we implemented the webserver, the DHCP server, the DNS server, the NIS service, the NFS service, the VPN service. However, because of the limited time, we did not make our LAN get access to the internet, although it is not quite difficult to implement. If the future time, we may try to make our LAN get access to the Internet so that our project can work in the real life.
Reference
[edit | edit source]- ↑ http://computernetworkingnotes.com/network-administrations/web-server.html
- ↑ https://help.ubuntu.com/community/isc-dhcp-server
- ↑ Computer Networking: A Top-Down Approach (6th Edition) - James F.Kurose, Keith W.Ross
- ↑ http://www.tldp.org/LDP/lame/LAME/linux-admin-made-easy/domain-name-server.html
- ↑ http://computernetworkingnotes.com/network-administrations/web-server.html
- ↑ http://linuxconfig.org/how-to-configure-nfs-on-linux
- ↑ http://www.techrepublic.com/blog/10-things/10-iptables-rules-to-help-secure-your-linux-box/