Data Networking/Fall 2016/NMLT
Project Objective[edit | edit source]
The objective of this project is to design a dynamic, secure internetwork for a startup company using Linux environment using Ubuntu 16.04. We have designed and implemented Domain Name Server (DNS) using BIND, Dynamic Host Configuration Protocol (DHCP) using isc-dhcp-server, WebServer and Firewall. We have also implemented Backup System which will make the system robust.
Project Team members[edit | edit source]
MIHIR BORKAR
NAMRATA SHIRKE
LAKSHITA TANEJA
TEJAL EKBOTE
Dynamic Host Configuration Protocol (DHCP)[edit | edit source]
Behaviour of the protocol[edit | edit source]
DHCP is a networking protocol that allocates IP address to end system. DHCP allocates a temporary IP address to a host when it connects to the network. DHCP server also allocates additional information like subnet mask, default gateway and address of DNS server.
Signalling[edit | edit source]
DHCP is a client-server protocol that is often referred as plug-and-play protocol. Whenever a host joins a network, DHCP server allocates a IP address from the pool of available address and whenever the client leaves, the IP address is returned back to the DHCP server. For a new host, the process executed is: - Whenever a new host joins, it discovers DHCP server using a DHCP discover message which is send using UDP on port number 67. The host sends the discover message on broadcast address 255.255.255.255 which is then broadcasted to all the nodes on subnet. - The DHCP servers receive the discover message and offers proposed IP address for the host, the network mask and IP address lease time. - The client then receives offers from server and respond to offer with a DHCP request message requesting configuration parameters. - The server then responds with DHCP ACK message allocating the requested parameters.
DHCP Configuration[edit | edit source]
For DHCP – Server: 1) Install DHCP server using: sudo apt-get install isc-dhcp-server
2) Install radvd package: sudo apt-get install radvd
3) Configure static IP address to network interfaces
4) Allow IPv6 and IPv4 forwarding using: sudo nano /etc/sysctl.conf
5) Configure eth0 as default interface using: sudo nano /etc/default/isc-dhcp-server
6) For IPv4: Configure DHCP server using sudo nano /etc/dhcp/dhcpd.conf
7) Edit resolv.conf file using sudo nano /etc/resolv.conf

8) For IPv6: edit conf file using: sudo nano /etc/dhcp/dhcpd6.conf

9) For IP v6: configure radvd conf file using: sudo nano /etc/radvd.conf

10) Reboot the system using: sudo init 6
11) Restart the DHCP server: sudo service networking restart
For DHCP Client:
1. Change the /etc/network/interfaces at the client side:

2. restart the client using: sudo init 6
Testing[edit | edit source]
Output on the client side:
Domain Name System (DNS)[edit | edit source]
Behaviour of Protocol[edit | edit source]
DNS is a distributed database which will provide the response that translate hostname to IP address like a directory services. One of the key element of DNS is DNS servers which maps the domain name to the corresponding IP address. All DNS messages and responses are sent within UDP on port 53. There are 5 types of DNS records – A, NS, CNAME, MX AND PTR.
Signalling[edit | edit source]
A host is identified by two ways, hostname and IP address and DNS is employed to translate a hostname to IP address. Other application layer protocols also employ DNS which also provide other functions like host aliasing, mail server, aliasing and load redistribution. An application will invoke client-side DNS which sends a query to the local DNS server to obtain IP address. The local DNS server then forwards the query message root DNS. The Root DNS replies to local DNS with IP address of TLD servers. The local DNS will then send message query to TLD servers. The TLD server’s responds to local DNS with IP address of authoritative DNS which contain the mapping of hostname to IP address. Finally, local DNS server sends query to authoritative DNS server which responds with IP address of the desired mapping of hostname.
DNS Configuration[edit | edit source]
For IPv4 1) Configure and assign static IP address to DNS Server: sudo nano “/etc/network/interfaces”.
2) Reboot the network interfaces: sudo /etc/init.d/networking restart 3) Install the bind9 server: sudo apt-get install bind9 4) Make changes in the configuration file in the Bind directory and add the forwarders in the file: sudo nano /etc/bind/named.conf.options

5) Configure forward and reverse lookup zones in local file: sudo nano /etc/bind/named.conf.local
6) Create new directory ‘zones’ and create forward and reverse database files in zone directory
7) Create the reverse lookup database file
8) Then edit resolv.conf file: sudo nano /etc/resolv.conf
9) then restart the bind9 server using: sudo service bind9 restart. 10) For the Slave Server repeat steps 1 to 5 and edit named.conf.local file using: sudo nano /etc/bind/named.conf.local
11) Configure the resolv.conf file and restart the bind9 server: sudo /etc/init.d/networking restart
• For IPv6 1) Configure static IPv6 address to the master and slave server by the following commands sudo nano /etc/network/interface
2) Add the reverse IPv6 domain for master and slave in the named.conf.local file. 3) In the master configuration file add:
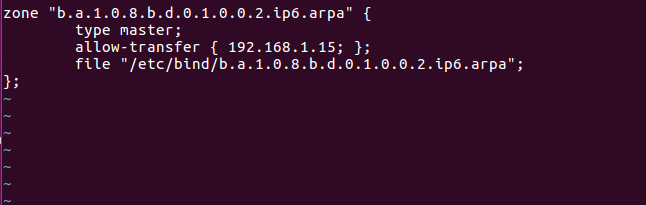
4) In the slave configuration file add:
5) In the master DNS server, create a new file for reverse zone for IPv6 configuration.
4) In Master DNS enter the entry for IPv6 record for forward zone:
5) Restart both master and slave DNS servers: sudo service bind9 restart Testing: • Master
• Output of Slave when master is ON
• Output of Slave when master is suspended
Web server and Firewall[edit | edit source]
Behaviour of Protocol[edit | edit source]
Web Server is a network protocol which servers the HTTP requests from the clients. A user agent like web browser requests for objects and it responds by sending the requested objects. The web servers allow users to obtain documents on demand. HTTP protocol defines the structure of the messages exchanged between the webserver and client. Apache2 web server is installed in Linux. Firewall is a network security device that isolates the traffic incoming and outgoing from the network. Network administrator can control and manage the traffic flow to and from the resources. Firewalls can be classified as traditional packet filters, stateful filters and application gateways. There are 2 ways to configure firewall management program – default deny policy and default allow policy.
Signaling[edit | edit source]
When user requests for web page, the browser will send HTTP request message to Web Server. The Server will receive the request for objects in web page. Then the server will respond to request and respond with HTTP response message.
Configuration Web Browser[edit | edit source]
1.Install apache2 sudo-apt get install apache2
2.create the www directory and change its permissions sudo mkdir -p /var/www/linux.tsm/public_html sudo chown -R $USER:$USER /var/www/linux.tsm/public_html sudo chmod -R 755 /var/www
3.modify the html file for the web browser using the following sudo nano /var/www/linux.tsm/public_html/index.html
4. copy the default configurations into new file sudo cp /etc/apache2/sites-available/000-default.conf /etc/apache2/sites-available/linux.tsm.conf
5. Modify the new file tsm.com.conf to contain the following ServerAdmin info@linux.tsm ServerName linux.tsm ServerAlias www.linux.tsm DocumentRoot /var/www/linux.tsm ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined
6.disable the default configuration and enable our new modified configuration and restart the services. sudo a2ensite linux.tsm.conf sudo a2dissite 000-default.conf
Configuration Firewall[edit | edit source]
- Install UFW and enable it using: sudo apt-get install ufw and sudo ufw enable
- Add rules to allow and block the traffic
- Allow port 22 for ftp using: sudo ufw allow 22# Numbered list item
- Allow port 80 for http traffic using: sudo ufw allow 80
- Block icmp requests using: sudo iptables –A INPUT –p icmp –j REJECT
- Block telnet request using: sudo iptables –A INPUT -d 192.168.1.40 –p tcp –dport 23 –j REJECT.
- Check the iptable updates using: sudo iptables –L
Testing[edit | edit source]
Output of Web browser:
Web Server Backup[edit | edit source]
Configuration backup[edit | edit source]
- Set up public key authentication without any password using: ssh -keygen
- To pass public key use command ssh-copy-id n@192.168.1.2
- Then, add a cron job executing appropriate rsync commands for scheduling backup.
Add-ons implemented[edit | edit source]
ARP Poisoning[edit | edit source]
Address Resolution Protocol poisoning (ARP Poisoning) is an attack where MAC address is changed by the attacker and also changed victim’s ARP cache with fake ARP packet and reply packet. This is also known as Man-in-the-middle-attack where attacker secretly alters the communication between two devices. Common example of Man-in-the-middle-attack is distributing malware that allows attacker to access the web browser and alters the communication and transaction.
Configuration[edit | edit source]
1) Install python scapy using: sudo apt-get update install python-scapy.
2) Write a scapy code to send malicious arp packets:
3) Run the scapy script to infect the client: sudo python poison.py
Testing[edit | edit source]
1) Install wireshark: sudo apt-get install wireshark
2) As soon as we excute the script, we can monitor the traffic on wireshark between the attacker and victim.
Network File System (NFS)[edit | edit source]
Behavior of protocol:[edit | edit source]
Network File System is a distributed file system protocol. It is server client application that allows a client computer to access files shared by the server system. NFS allows user to mount files that can be accessed by the clients with the assigned privileges.
Configuration[edit | edit source]
1) Install nfs-kernel-server with command: sudo apt-get install nfs-kernel-server.
2) Configure the directories which would be imported to client: sudo nano /etc/exports and edit the file as follows:
3) Create NFS table to hold the record of shares: sudo exportfs -a
4) Restart the NFS service: sudo service nfs-kernel-server start

At the client side:
1) Install nfs common in client side: Sudo apt-get install nfs-common
2) Create an empty directory in the client side: sudo mkdir -p /home/tejal
3) Mount the file we want to share with the client: sudo mount 192.168.1.8:/home /home/tejal
4) Check the mounted files using disk space: df -h
Testing:[edit | edit source]
IPSEC Virtual Private Network[edit | edit source]
A Virtual Private Network is created over public and private network to enable secure communication over the internet. It allows users to send data across public network, if the devices are connected to private network. Using virtual tunneling protocols a virtual point-to-point connection is created. The two modes that can be configured to operate are Tunnel and Transport mode, where Tunnel mode is the default one. The whole data traffic is encrypted using IPsec which protect the communication between 2 hosts. It also blocks packet sniffing to discover the traffic.
Configuration[edit | edit source]
1) We have two virtual machines on Ubuntu 14.04 with following IP address where we want to encrypt communication: Server1: 192.168.1.50 Server2: 192.168.1.55
For Server1: 1) Install ipsec tools on server1: apt-get install ipsec-tools strongswan-starter 2) create crypto maps using IPSEC configuration file: sudo nano /etc/ipsec.conf
3) create file to store PSKs: sudo nano /etc/ipsec.secrets
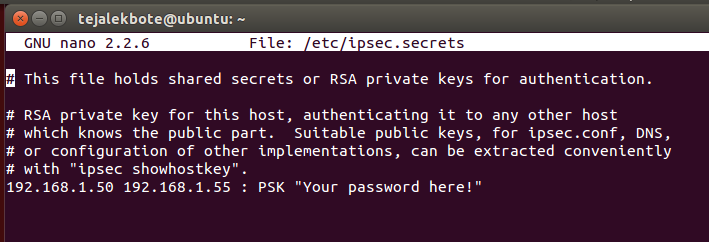
4) Then restart IPsec: sudo ipsec restart

5) Check the status: sudo ipsec statusall
Server2 configuration:
1) apt-get install ipsec-tools strongswan-starter 2) Configure ipsec.conf again:
3) Create file for PSKs: nano /etc/ipsec.secrets
4) Restart ipsec: ipsec restart
Testing Tunnel: 1) On Server1 use: ping -s 4048 192.168.1.55
2) On Server2: watch ipsec statusall
We observe number of packets and number of bytes increasing while the ping is running.
References[edit | edit source]
- Computer Networking A TopDown Approach by KUROSE and ROSS
- http://www.vaspects.com/2014/01/15/ipv6-for-the-debian-dns-server/
- http://askubuntu.com/questions/330148/how-do-i-do-a-complete-bind9-dns-server-configuration-with-a-hostname
- www.youtube.com
- www.wikipedia.org
- https://www.digitalocean.com/community/tutorials/how-to-set-up-an-nfs-mount-on-ubuntu-14-04
- https://www.gypthecat.com/ipsec-vpn-host-to-host-on-ubuntu-14-04-with-strongswan



































